With browser makers steadily clamping down on third-party tracking, advertising technology companies are increasingly embracing a DNS technique to evade such defenses, thereby posing a threat to web security and privacy. Called CNAME Cloaking, the practice of blurring the distinction between first-party and third-party cookies not only results in leaking sensitive private … [Read more...] about Online Trackers Increasingly Switching to Invasive CNAME Cloaking Technique
Search Results for: clear dns cache os x
How to Fight Business Email Compromise (BEC) with Email Authentication?
An ever-evolving and rampant form of cybercrime that targets emails as the potential medium to conduct fraud is known as Business Email Compromise. Targeting commercial, government as well as non-profit organizations, BEC can lead to huge amounts of data loss, security breach, and compromised financial assets. It is a common misconception that cybercriminals usually lay their … [Read more...] about How to Fight Business Email Compromise (BEC) with Email Authentication?
Here’s How Iran Spies on Dissidents with the Help of Hackers
Twin cyber operations conducted by state-sponsored Iranian threat actors demonstrate their continued focus on compiling detailed dossiers on Iranian citizens that could threaten the stability of the Islamic Republic, including dissidents, opposition forces, and ISIS supporters, and Kurdish natives. Tracing the extensive espionage operations to two advanced Iranian cyber-groups … [Read more...] about Here’s How Iran Spies on Dissidents with the Help of Hackers
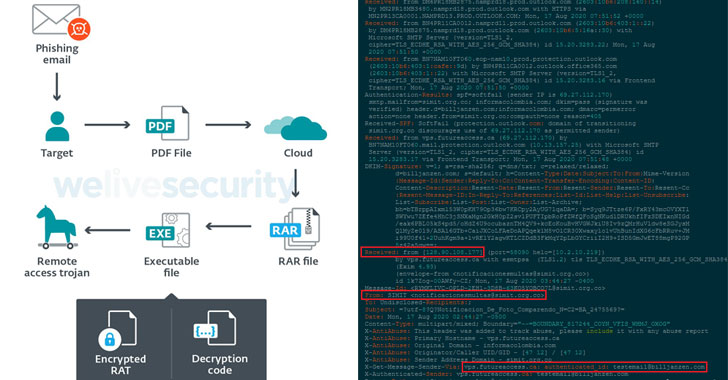
Experts Uncover Malware Attacks Against Colombian Government and Companies
Cybersecurity researchers took the wraps off an ongoing surveillance campaign directed against Colombian government institutions and private companies in the energy and metallurgical industries. In a report published by ESET on Tuesday, the Slovak internet security company said the attacks — dubbed "Operation Spalax" — began in 2020, with the modus operandi sharing some … [Read more...] about Experts Uncover Malware Attacks Against Colombian Government and Companies
Law Enforcement Seizes Joker’s Stash — Stolen Credit Card Marketplace
The US Federal Bureau of Investigation (FBI) and Interpol have allegedly seized proxy servers used in connection with Blockchain-based domains belonging to Joker's Stash, a notorious fraud bazaar known for selling compromised payment card data in underground forums. The takedown happened last week on December 17. The operators of Joker's Stash operate several versions of the … [Read more...] about Law Enforcement Seizes Joker’s Stash — Stolen Credit Card Marketplace
Software Supply-Chain Attack Hits Vietnam Government Certification Authority
Cybersecurity researchers today disclosed a new supply-chain attack targeting the Vietnam Government Certification Authority (VGCA) that compromised the agency's digital signature toolkit to install a backdoor on victim systems. Uncovered by Slovak internet security company ESET early this month, the "SignSight" attack involved modifying software installers hosted on the CA's … [Read more...] about Software Supply-Chain Attack Hits Vietnam Government Certification Authority
Amnesia:33 — Critical TCP/IP Flaws Affect Millions of IoT Devices
Cybersecurity researchers disclosed a dozen new flaws in multiple widely-used embedded TCP/IP stacks impacting millions of devices ranging from networking equipment and medical devices to industrial control systems that could be exploited by an attacker to take control of a vulnerable system. Collectively called "AMNESIA:33" by Forescout researchers, it is a set of 33 … [Read more...] about Amnesia:33 — Critical TCP/IP Flaws Affect Millions of IoT Devices
How DMARC Can Stop Criminals Sending Fake Emails on Behalf of Your Domain
21st-century technology has allowed Cybercriminals to use sophisticated and undetectable methods for malicious activities. In 2020 alone, a survey revealed that 65% of US-based companies were vulnerable to email phishing and impersonation attacks. This calls for upgrading your organization's security with DMARC, which if not implemented, will enable cyber-attackers … [Read more...] about How DMARC Can Stop Criminals Sending Fake Emails on Behalf of Your Domain
Hackers-For-Hire Group Develops New ‘PowerPepper’ In-Memory Malware
Cybersecurity researchers on Thursday disclosed details of a previously undiscovered in-memory Windows backdoor developed by a hacker-for-hire operation that can execute remotely malicious code and steal sensitive information from its targets in Asia, Europe, and the US. Dubbed "PowerPepper" by Kaspersky researchers, the malware has been attributed to the DeathStalker group … [Read more...] about Hackers-For-Hire Group Develops New ‘PowerPepper’ In-Memory Malware
Why Replace Traditional Web Application Firewall (WAF) With New Age WAF?
At present, web applications have become the top targets for attackers because of potential monetization opportunities. Security breaches on the web application can cost millions. Strikingly, DNS (Domain Name System) related outage and Distributed denial of service (DDoS) lead a negative impact on businesses. Among the wide range of countermeasures, a web application firewall … [Read more...] about Why Replace Traditional Web Application Firewall (WAF) With New Age WAF?