A new tax-themed malware campaign targeting insurance and finance sectors has been observed leveraging GitHub links in phishing email messages as a way to bypass security measures and deliver Remcos RAT, indicating that the method is gaining traction among threat actors. "In this campaign, legitimate repositories such as the open-source tax filing software, UsTaxes, HMRC, and … [Read more...] about GitHub, Telegram Bots, and QR Codes Abused in New Wave of Phishing Attacks
Abused
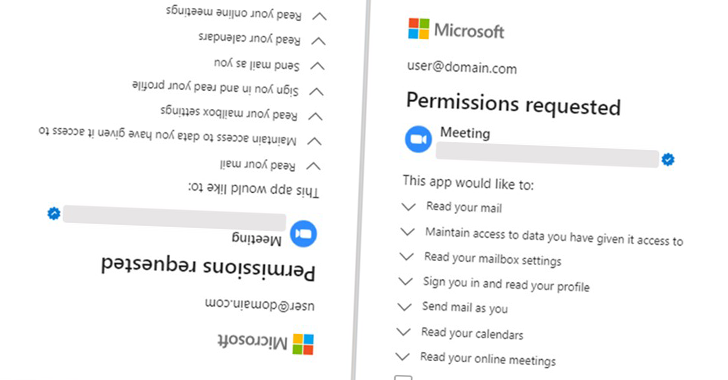
Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
Feb 01, 2023Ravie LakshmananEnterprise Security / Authentication Microsoft on Tuesday said it took steps to disable fake Microsoft Partner Network (MPN) accounts that were used for creating malicious OAuth applications as part of a malicious campaign designed to breach organizations' cloud environments and steal email. "The applications created by these fraudulent actors were … [Read more...] about Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
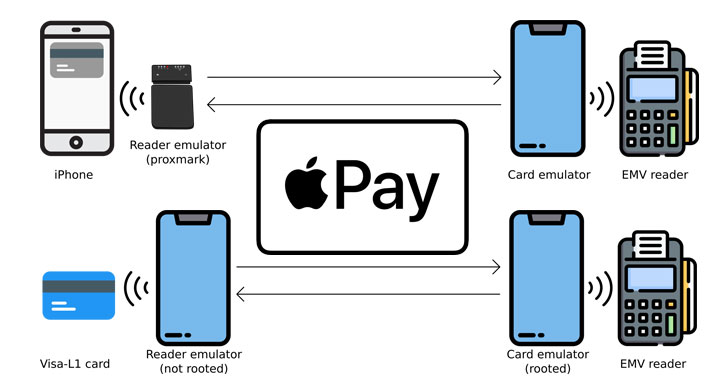
Apple Pay Can be Abused to Make Contactless Payments From Locked iPhones
Cybersecurity researchers have disclosed an unpatched flaw in Apple Pay that attackers could abuse to make an unauthorized Visa payment with a locked iPhone by taking advantage of the Express Travel mode set up in the device's wallet. "An attacker only needs a stolen, powered on iPhone. The transactions could also be relayed from an iPhone inside someone's bag, without their … [Read more...] about Apple Pay Can be Abused to Make Contactless Payments From Locked iPhones
Atlassian Confluence RCE Flaw Abused in Multiple Cyberattack Campaigns
Opportunistic threat actors have been found actively exploiting a recently disclosed critical security flaw in Atlassian Confluence deployments across Windows and Linux to deploy web shells that result in the execution of crypto miners on compromised systems. Tracked as CVE-2021-26084 (CVSS score: 9.8), the vulnerability concerns an OGNL (Object-Graph Navigation Language) … [Read more...] about Atlassian Confluence RCE Flaw Abused in Multiple Cyberattack Campaigns
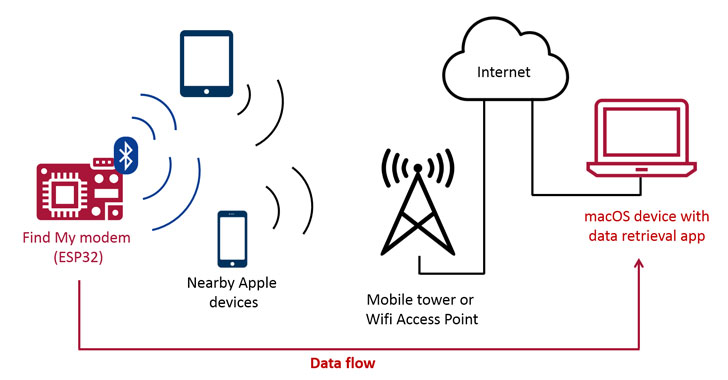
Apple’s Find My Network Can be Abused to Exfiltrate Data From Nearby Devices
Latest research has demonstrated a new exploit that enables arbitrary data to be uploaded from devices that are not connected to the Internet by simply sending "Find My Bluetooth" broadcasts to nearby Apple devices. "It's possible to upload arbitrary data from non-internet-connected devices by sending Find My [Bluetooth Low Energy] broadcasts to nearby Apple devices that then … [Read more...] about Apple’s Find My Network Can be Abused to Exfiltrate Data From Nearby Devices