Oct 16, 2024Ravie LakshmananEndpoint Security / Malware Threat actors are attempting to abuse the open-source EDRSilencer tool as part of efforts to tamper endpoint detection and response (EDR) solutions and hide malicious activity. Trend Micro said it detected "threat actors attempting to integrate EDRSilencer in their attacks, repurposing it as a means of evading … [Read more...] about Hackers Abuse EDRSilencer Tool to Bypass Security and Hide Malicious Activity
Activity
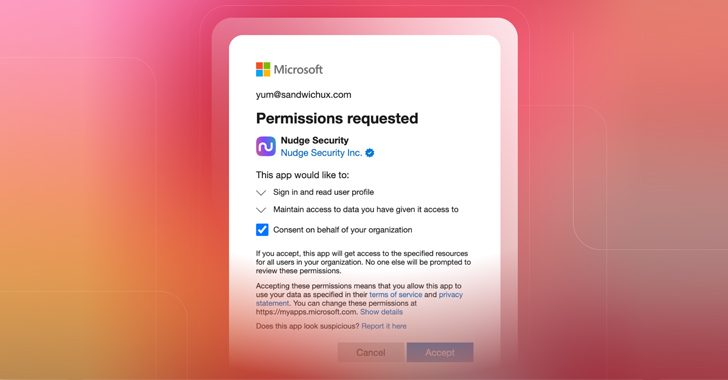
How to Investigate an OAuth Grant for Suspicious Activity or Overly Permissive Scopes
From a user's perspective, OAuth works like magic. In just a few keystrokes, you can whisk through the account creation process and gain immediate access to whatever new app or integration you're seeking. Unfortunately, few users understand the implications of the permissions they allow when they create a new OAuth grant, making it easy for malicious actors to manipulate … [Read more...] about How to Investigate an OAuth Grant for Suspicious Activity or Overly Permissive Scopes
Detecting Lateral Movement activity: A new Kibana integration
Cyber attacks are becoming more frequent, targeted, and complex. When it comes to sophisticated attacks, one of the most commonly seen tactics is Lateral Movement. During lateral movement, many attackers try impersonating a legitimate user by abusing admin tools (e.g., SMB, SAMBA, FTP, WMI, WinRM, and PowerShell Remoting) to move laterally from system to system in search of … [Read more...] about Detecting Lateral Movement activity: A new Kibana integration
Analyze and visualize Strava activity details with the Elastic Stack
Analyze and visualize Strava activity details with the Elastic StackEnglish简体中文한국어日本語FrançaisDeutschEspañolPortuguêsThis is the second blog post in our Strava series, based on the first one: “How to import Strava data into the Elastic Stack.” I will take you through a journey of data onboarding, manipulation, and visualization.What is Strava and why is it the focus? Strava is a … [Read more...] about Analyze and visualize Strava activity details with the Elastic Stack
KNOTWEED Activity Group Assessment | Elastic Blog
Key TakeawaysKNOTWEED is an activity group sponsored by the PSOA entity DSIRFKNOTWEED uses 0-day exploits to load custom malware and frameworks onto victim systemsElastic Endpoint Security prevents the execution chain of the VBA from infecting the host with spyware associated with KNOTWEEDSummaryOn July 27, 2022, Microsoft Threat Intelligence Center (MSTIC) disclosed a … [Read more...] about KNOTWEED Activity Group Assessment | Elastic Blog
Detect domain generation algorithm (DGA) activity with new Kibana integration
Searching for a way to help protect your network from potential domain generation algorithm (DGA) attacks? Look no further — a DGA detection package is now available in the Integrations app in Kibana. In a single click, users can install and start using the DGA model and associated assets, including ingest pipeline configurations, anomaly detection jobs, and detection rules. … [Read more...] about Detect domain generation algorithm (DGA) activity with new Kibana integration
Back from vacation: Analyzing Emotet’s activity in 2020
Cisco Blogs / Security / Threat Research / Back from vacation: Analyzing Emotet’s activity in 2020 By Nick Biasini, Edmund Brumaghin, and Jaeson Schultz. Emotet is one of the most heavily distributed malware families today. Cisco Talos observes large quantities of Emotet emails being sent to individuals and organizations around the world on an almost daily basis. … [Read more...] about Back from vacation: Analyzing Emotet’s activity in 2020
How We Trained Overfit Models to Identify Malicious Activity
In this blog, we present the results of some preliminary experiments with training highly “overfit” (interpolated) models to identify malicious activity based on behavioral data. These experiments were inspired by an expanding literature that questions the traditional approach to machine learning, which has sought to avoid overfitting in order to encourage model … [Read more...] about How We Trained Overfit Models to Identify Malicious Activity
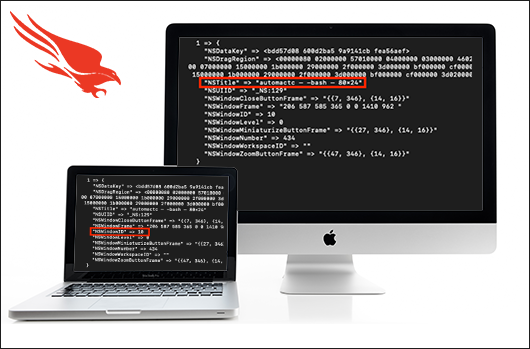
Reconstructing Command-Line Activity on MacOS
In Mac OSX Lion (10.7), Apple introduced a feature called “User Interface (UI) Preservation”, intended to save the state of application windows and restore them upon future launches. Like many features intended to enhance the user experience, UI Preservation can also provide immense forensic value to an investigator. In the case of anti-forensic measures taken by an adversary, … [Read more...] about Reconstructing Command-Line Activity on MacOS
Dear Apple: Face to Face — Apple Watch
Every day, people reach out to Apple to say how Apple Watch is helping them live healthier lives. So we decided to reach out to some of them. Learn more: https://apple.co/2kulkSL … [Read more...] about Dear Apple: Face to Face — Apple Watch