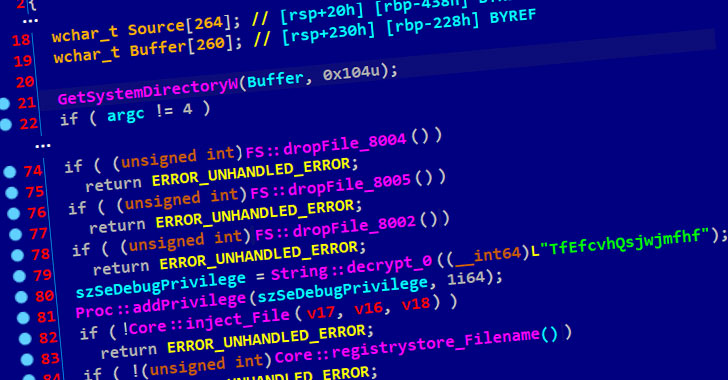
Cybersecurity researchers took the wraps off a novel supply chain attack in South Korea that abuses legitimate security software and stolen digital certificates to distribute remote administration tools (RATs) on target systems. Attributing the operation to the Lazarus Group, also known as Hidden Cobra, Slovak internet security company ESET said the state-sponsored threat actor … [Read more...] about Trojanized Security Software Hits South Korea Users in Supply-Chain Attack
attack
A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems
German authorities last week disclosed that a ransomware attack on the University Hospital of Düsseldorf (UKD) caused a failure of IT systems, resulting in the death of a woman who had to be sent to another hospital that was 20 miles away. The incident marks the first recorded casualty as a consequence of cyberattacks on critical healthcare facilities, which has ramped up in … [Read more...] about A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems
New Raccoon Attack Could Let Attackers Break SSL/TLS Encryption
A group of researchers has detailed a new timing vulnerability in Transport Layer Security (TLS) protocol that could potentially allow an attacker to break the encryption and read sensitive communication under specific conditions.Dubbed "Raccoon Attack," the server-side attack exploits a side-channel in the cryptographic protocol (versions 1.2 and lower) to extract the shared … [Read more...] about New Raccoon Attack Could Let Attackers Break SSL/TLS Encryption
Reducing the Attack Surface with Custom Indicators of Attack
Introduction As many organizations around the globe are settling into longer-term remote working situations for their employees, IT Hygiene should be at the forefront of preventative security protocol. Adversaries are getting increasingly savvy, taking advantage of changes in work environments. Since IT hygiene requires even more oversight than before, how can security teams … [Read more...] about Reducing the Attack Surface with Custom Indicators of Attack
Falcon Complete Uncovers Global Attack Campaign [Case Study]
In this blog, we describe a recent incident that highlights the CrowdStrike® Falcon Complete™ team’s ability to act as an extension of our customer’s security team to quickly detect, triage and contain an active attacker before they were able to complete their goal. In this example, we outline an active web exploitation campaign that was impacting multiple customers at the same … [Read more...] about Falcon Complete Uncovers Global Attack Campaign [Case Study]
How the Falcon Complete Team Stopped an RDP Attack [Part 1]
Welcome to the CrowdStrike® Falcon CompleteTM team’s first “Tales from the Trenches” blog, where we describe a recent intrusion that shows how the Falcon Complete managed detection and response (MDR) service operates as an extension of the customer’s security team to quickly detect, investigate and contain an active attacker before they’re able to complete their goal. Once this … [Read more...] about How the Falcon Complete Team Stopped an RDP Attack [Part 1]
How the Falcon Complete Team Stopped an RDP Attack [Part 2]
In Part 1 of this two-part “Tales from the Trenches” blog, we examined a stealthy Remote Desktop Protocol (RDP) intrusion uncovered by CrowdStrike® Falcon CompleteTM experts. In this installment, we’ll walk you through remediation efforts, highlighting Falcon Complete’s ability to directly eject a threat actor and bring the customer’s environment back to a clean, operational … [Read more...] about How the Falcon Complete Team Stopped an RDP Attack [Part 2]
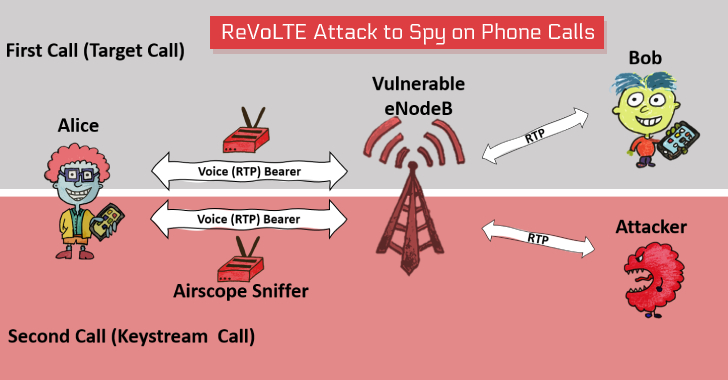
New Attack Lets Hackers Decrypt VoLTE Encryption to Spy on Phone Calls
A team of academic researchers—who previously made the headlines earlier this year for uncovering severe security issues in the 4G LTE and 5G networks—today presented a new attack called 'ReVoLTE,' that could let remote attackers break the encryption used by VoLTE voice calls and spy on targeted phone calls.The attack doesn't exploit any flaw in the Voice over LTE (VoLTE) … [Read more...] about New Attack Lets Hackers Decrypt VoLTE Encryption to Spy on Phone Calls
Reducing the Attack Surface with Custom Indicators of Attack
Introduction The evolving nature of malicious activity is keeping security teams on their toes. Adversaries may start with commodity malware but quickly shift tactics as they encounter resistance or zero-in on their specific target. As tactics get more targeted and tailored, detection and protection can get more complicated. Can security teams easily customize protection rules … [Read more...] about Reducing the Attack Surface with Custom Indicators of Attack
Researcher Demonstrates 4 New Variants of HTTP Request Smuggling Attack
A new research has identified four new variants of HTTP request smuggling attacks that work against various commercial off-the-shelf web servers and HTTP proxy servers.Amit Klein, VP of Security Research at SafeBreach who presented the findings today at the Black Hat security conference, said that the attacks highlight how web servers and HTTP proxy servers are still … [Read more...] about Researcher Demonstrates 4 New Variants of HTTP Request Smuggling Attack