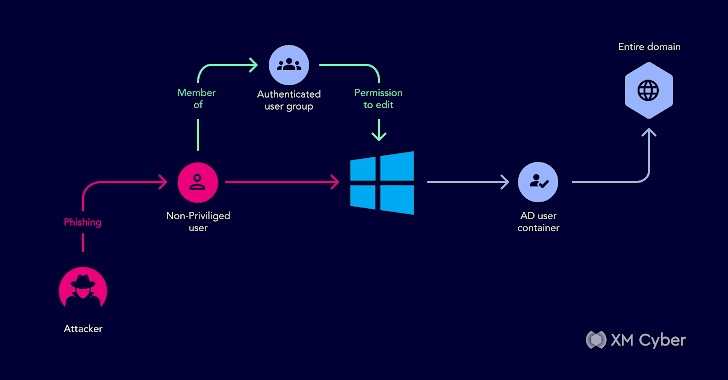
Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning and enforcing security policies for all network endpoints. With it, users can access various resources across networks. As things tend to do, times, they are a'changin' – and a few years back, Microsoft introduced Azure Active … [Read more...] about Understanding Active Directory Attack Paths to Improve Security
attack
A Data Exfiltration Attack Scenario: The Porsche Experience
As part of Checkmarx's mission to help organizations develop and deploy secure software, the Security Research team started looking at the security posture of major car manufacturers. Porsche has a well-established Vulnerability Reporting Policy (Disclosure Policy)[1], it was considered in scope for our research, so we decided to start there, and see what we could find. What we … [Read more...] about A Data Exfiltration Attack Scenario: The Porsche Experience
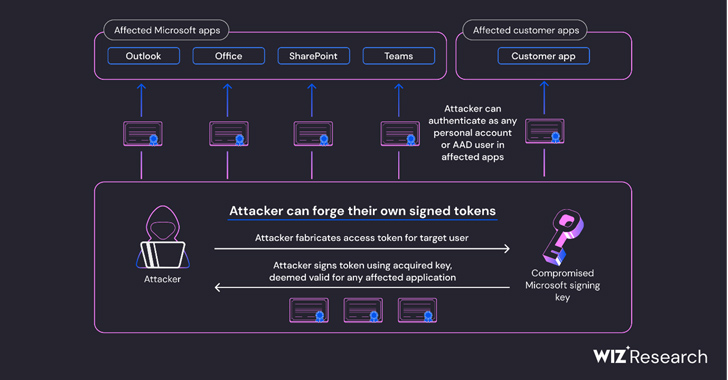
Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports
Jul 21, 2023THNEmail Security / Cyber Attack The recent attack against Microsoft's email infrastructure by a Chinese nation-state actor referred to as Storm-0558 is said to have a broader scope than previously thought. According to cloud security company Wiz, the inactive Microsoft account (MSA) consumer signing key used to forge Azure Active Directory (Azure AD or AAD) … [Read more...] about Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports
How to Manage Your Attack Surface?
Attack surfaces are growing faster than security teams can keep up. To stay ahead, you need to know what's exposed and where attackers are most likely to strike. With cloud migration dramatically increasing the number of internal and external targets, prioritizing threats and managing your attack surface from an attacker's perspective has never been more important. Let's look … [Read more...] about How to Manage Your Attack Surface?
These 6 Questions Will Help You Choose the Best Attack Surface Management Platform
Jul 17, 2023The Hacker NewsAttack Surface Management The hype around different security categories can make it difficult to discern features and capabilities from bias when researching new platforms. You want to advance your security measures, but what steps actually make sense for your business? For anyone ready to find an attack surface management (ASM) vendor, review … [Read more...] about These 6 Questions Will Help You Choose the Best Attack Surface Management Platform
Gain Insights from Gcore’s 2023 DDoS Attack Statistics
Jul 06, 2023The Hacker News Gcore Radar is a quarterly report prepared by Gcore that provides insights into the current state of the DDoS protection market and cybersecurity trends. This report offers you an understanding of the evolving threat landscape and highlights the measures required to protect against attacks effectively. It serves as an insight for businesses and … [Read more...] about Gain Insights from Gcore’s 2023 DDoS Attack Statistics
DDoSia Attack Tool Evolves with Encryption, Targeting Multiple Sectors
The threat actors behind the DDoSia attack tool have come up with a new version that incorporates a new mechanism to retrieve the list of targets to be bombarded with junk HTTP requests in an attempt to bring them down. The updated variant, written in Golang, "implements an additional security mechanism to conceal the list of targets, which is transmitted from the … [Read more...] about DDoSia Attack Tool Evolves with Encryption, Targeting Multiple Sectors
How Attack Surface Management Prioritizes Vulnerability Remediation
As the business environment becomes increasingly connected, organizations' attack surfaces continue to expand, making it challenging to map and secure both known and unknown assets. In particular, unknown assets present security challenges related to shadow IT, misconfigurations, ineffective scan coverage, among others. Given attack surface sprawl and evolving threats, many … [Read more...] about How Attack Surface Management Prioritizes Vulnerability Remediation
Mastering API Security: Understanding Your True Attack Surface
Jun 13, 2023The Hacker NewsAPI Security / Webinar Believe it or not, your attack surface is expanding faster than you realize. How? APIs, of course! More formally known as application programming interfaces, API calls are growing twice as fast as HTML traffic, making APIs an ideal candidate for new security solutions aimed at protecting customer data, according to … [Read more...] about Mastering API Security: Understanding Your True Attack Surface
Why Now? The Rise of Attack Surface Management
Jun 12, 2023The Hacker NewsAttack Surface Management The term "attack surface management" (ASM) went from unknown to ubiquitous in the cybersecurity space over the past few years. Gartner and Forrester have both highlighted the importance of ASM recently, multiple solution providers have emerged in the space, and investment and acquisition activity have seen an uptick. Many … [Read more...] about Why Now? The Rise of Attack Surface Management