We often write about scams promising someone mountains of gold, when in reality the opposite happens and their pockets get emptied. Similarly, cybercriminals can get their hands on the money of entire companies by exploiting the greed and negligence of their employees. That’s exactly what happened with the Ronin Networks blockchain system, created by Sky Mavis for the … [Read more...] about Sky Mavis robbed of $540 million in spyware attack
attack
Hackers Exploit Mitel VoIP Zero-Day in Likely Ransomware Attack
A suspected ransomware intrusion against an unnamed target leveraged a Mitel VoIP appliance as an entry point to achieve remote code execution and gain initial access to the environment. The findings come from cybersecurity firm CrowdStrike, which traced the source of the attack to a Linux-based Mitel VoIP device sitting on the network perimeter, while also identifying a … [Read more...] about Hackers Exploit Mitel VoIP Zero-Day in Likely Ransomware Attack
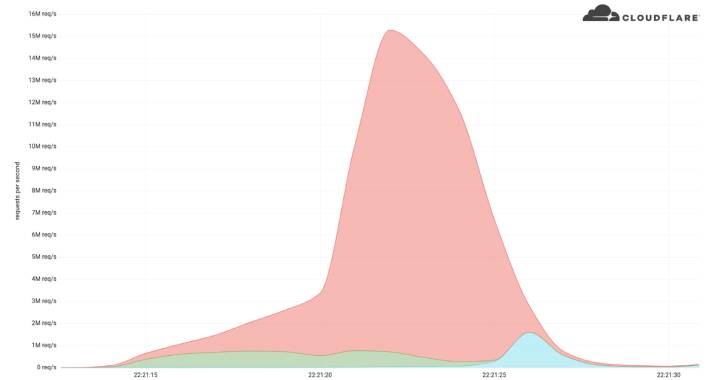
Cloudflare Thwarts Record DDoS Attack Peaking at 15 Million Requests Per Second
Cloudflare on Wednesday disclosed that it acted to mitigate a 15.3 million request-per-second (RPS) distributed denial-of-service (DDoS) attack. The web infrastructure and website security company called it one of the "largest HTTPS DDoS attacks on record." "HTTPS DDoS attacks are more expensive in terms of required computational resources because of the higher cost of … [Read more...] about Cloudflare Thwarts Record DDoS Attack Peaking at 15 Million Requests Per Second
What is a browser-in-the-browser (BitB) attack?
In their relentless pursuit of folks’ credentials, secret keys and other valuable information, cybercriminals are continually inventing new ways to deceive users. It’s worth noting that normally, no matter how sophisticated these schemes become, they’re all aimed at users who drop their guard. If you just pay close attention to a few details — first and foremost, the address of … [Read more...] about What is a browser-in-the-browser (BitB) attack?
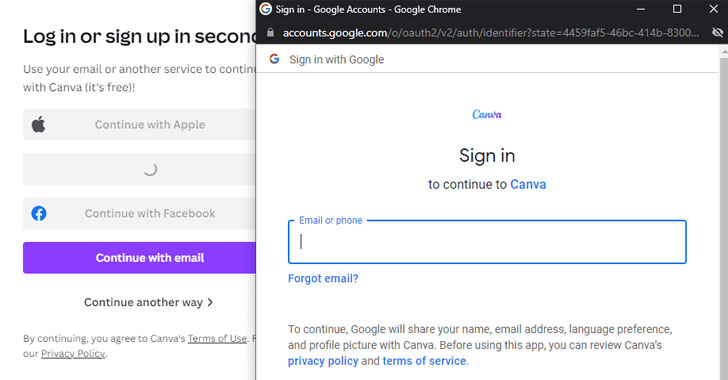
New Browser-in-the Browser (BITB) Attack Makes Phishing Nearly Undetectable
A novel phishing technique called browser-in-the-browser (BitB) attack can be exploited to simulate a browser window within the browser in order to spoof a legitimate domain, thereby making it possible to stage convincing phishing attacks. According to penetration tester and security researcher, who goes by the handle mrd0x_, the method takes advantage of third-party single … [Read more...] about New Browser-in-the Browser (BITB) Attack Makes Phishing Nearly Undetectable
Enhancing Fileless Attack Detection with Memory Scanning
CrowdStrike introduces memory scanning into the CrowdStrike Falcon® sensor for Windows to enhance existing visibility and detection of fileless threats The Falcon sensor integrates Intel threat detection technology to perform accelerated memory scanning for malicious byte patterns Memory scanning is optimized for performance on Intel CPUs, including high-performance operation, … [Read more...] about Enhancing Fileless Attack Detection with Memory Scanning
Researchers Demonstrate New Side-Channel Attack on Homomorphic Encryption
A group of academics from the North Carolina State University and Dokuz Eylul University have demonstrated what they say is the "first side-channel attack" on homomorphic encryption that could be exploited to leak data as the encryption process is underway. "Basically, by monitoring power consumption in a device that is encoding data for homomorphic encryption, we are able to … [Read more...] about Researchers Demonstrate New Side-Channel Attack on Homomorphic Encryption
Cyber Asset Attack Surface Management with Cisco Secure Cloud Insights: Beyond CSPM
In today’s digital-first world having enterprise grade information, services, and workloads in the cloud is becoming increasingly important for success. Nonetheless the lack of asset visibility that haunted private networks has not disappeared in the cloud era; it has been transferred, or some may say even aggravated. In its Hype Cycle for Security Operations, Gartner has … [Read more...] about Cyber Asset Attack Surface Management with Cisco Secure Cloud Insights: Beyond CSPM
Hackers Using Device Registration Trick to Attack Enterprises with Lateral Phishing
Microsoft has disclosed details of a large-scale, multi-phase phishing campaign that uses stolen credentials to register devices on a victim's network to further propagate spam emails and widen the infection pool. The tech giant said the attacks manifested through accounts that were not secured using multi-factor authentication (MFA), thereby making it possible for the … [Read more...] about Hackers Using Device Registration Trick to Attack Enterprises with Lateral Phishing
What is NoReboot and how to protect yourself from such an attack
To be absolutely sure your phone isn’t tracking you or listening in on any conversations, you might turn it off. It seems logical; that way, even if the phone is infected with serious spyware, it can’t do anything. In addition, turning off or restarting a smartphone is one of the most reliable ways to fight such infections; in many cases, spyware “lives” only until the next … [Read more...] about What is NoReboot and how to protect yourself from such an attack