Cybersecurity researchers have discovered an entirely new attack vector that enables adversaries to exploit the Log4Shell vulnerability on servers locally by using a JavaScript WebSocket connection. "This newly-discovered attack vector means that anyone with a vulnerable Log4j version on their machine or local private network can browse a website and potentially trigger the … [Read more...] about New Local Attack Vector Expands the Attack Surface of Log4j Vulnerability
attack
Apache Log4j Vulnerability — Log4Shell — Widely Under Active Attack
Threat actors are actively weaponizing unpatched servers affected by the newly identified "Log4Shell" vulnerability in Log4j to install cryptocurrency miners, Cobalt Strike, and recruit the devices into a botnet, even as telemetry signs point to exploitation of the flaw nine days before it even came to light. Netlab, the networking security division of Chinese tech giant Qihoo … [Read more...] about Apache Log4j Vulnerability — Log4Shell — Widely Under Active Attack
Why Holidays Put Your Company at Risk of Cyber Attack (And How to Take Precautions)
It is a time when many are thinking of their families and loved ones, time off work, and gift-giving – the holidays. However, while many have their minds outside the realm of work during the holiday season, often, this is when attackers plan their most sinister attacks. So how can you take precautions to protect your organization during these times? Why holidays put your … [Read more...] about Why Holidays Put Your Company at Risk of Cyber Attack (And How to Take Precautions)
Researches Detail 17 Malicious Frameworks Used to Attack Air-Gapped Networks
Four different malicious frameworks designed to attack air-gapped networks were detected in the first half of 2020 alone, bringing the total number of such toolkits to 17 and offering adversaries a pathway to cyber espionage and exfiltrate classified information. "All frameworks are designed to perform some form of espionage, [and] all the frameworks used USB drives as the … [Read more...] about Researches Detail 17 Malicious Frameworks Used to Attack Air-Gapped Networks
New Blacksmith Exploit Bypasses Current Rowhammer Attack Defenses
Cybersecurity researchers have demonstrated yet another variation of the Rowhammer attack affecting all DRAM (dynamic random-access memory) chips that bypasses currently deployed mitigations, thereby effectively compromising the security of the devices. The new technique — dubbed "Blacksmith" (CVE-2021-42114, CVSS score: 9.0) — is designed to trigger bit flips on target refresh … [Read more...] about New Blacksmith Exploit Bypasses Current Rowhammer Attack Defenses
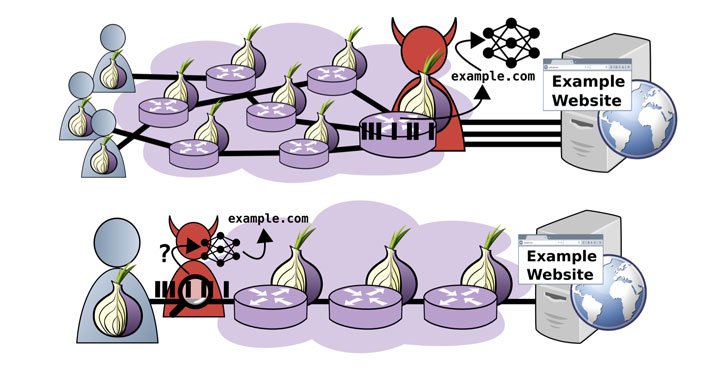
Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
A new analysis of website fingerprinting (WF) attacks aimed at the Tor web browser has revealed that it's possible for an adversary to glean a website frequented by a victim, but only in scenarios where the threat actor is interested in a specific subset of the websites visited by users. "While attacks can exceed 95% accuracy when monitoring a small set of five popular … [Read more...] about Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
One-Click Attack Surface in Linux Desktop Environments
The Advanced Research Team at CrowdStrike Intelligence discovered multiple vulnerabilities affecting libvncclient. In some widely used desktop environments, such as GNOME, these vulnerabilities can be triggered in a one-click fashion. Introduction Client-side exploitation has become a crucial component of many attackers’ toolkits. In the desktop space, exploiting browsers is … [Read more...] about One-Click Attack Surface in Linux Desktop Environments
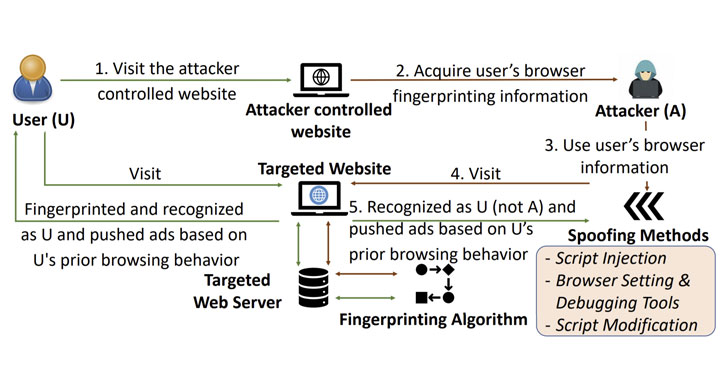
New Attack Let Attacker Collect and Spoof Browser’s Digital Fingerprints
A "potentially devastating and hard-to-detect threat" could be abused by attackers to collect users' browser fingerprinting information with the goal of spoofing the victims without their knowledge, thus effectively compromising their privacy. Academics from Texas A&M University dubbed the attack system "Gummy Browsers," likening it to a nearly 20-year-old "Gummy Fingers" … [Read more...] about New Attack Let Attacker Collect and Spoof Browser’s Digital Fingerprints
Researchers Break Intel SGX With New ‘SmashEx’ CPU Attack Technique
A newly disclosed vulnerability affecting Intel processors could be abused by an adversary to gain access to sensitive information stored within enclaves and even run arbitrary code on vulnerable systems. The vulnerability (CVE-2021-0186, CVSS score: 8.2) was discovered by a group of academics from ETH Zurich, the National University of Singapore, and the Chinese National … [Read more...] about Researchers Break Intel SGX With New ‘SmashEx’ CPU Attack Technique
Update Your Windows PCs Immediately to Patch New 0-Day Under Active Attack
Microsoft on Tuesday rolled out security patches to contain a total of 71 vulnerabilities in Microsoft Windows and other software, including a fix for an actively exploited privilege escalation vulnerability that could be exploited in conjunction with remote code execution bugs to take control over vulnerable systems. Two of the addressed security flaws are rated Critical, 68 … [Read more...] about Update Your Windows PCs Immediately to Patch New 0-Day Under Active Attack