By comparison, a phishing attack makes sense: Click a link, land on a malicious page, enter some details, and an attacker steals them. Try this one on for size, instead: Click a link and an attacker steals your data. That’s right, today we’re talking about malicious pages that exploit a fundamental CPU feature to steal data without requiring a victim to enter anything. And the … [Read more...] about How a Spook.js attack works
attack
Big Game Hunting TTPs Continue to Shift After DarkSide Pipeline Attack
The eCrime ecosystem is an active and diverse economy of financially motivated threat actors engaging in a myriad of criminal activities to generate revenue. With the CrowdStrike eCrime Index (ECX), CrowdStrike’s Intelligence team maintains a composite score to track changes to this ecosystem. The ECX is composed of several key observables covering different aspects of … [Read more...] about Big Game Hunting TTPs Continue to Shift After DarkSide Pipeline Attack
Update Google Chrome to Patch 2 New Zero-Day Flaws Under Attack
Google on Monday released security updates for Chrome web browser to address a total of 11 security issues, two of which it says are actively exploited zero-days in the wild. Tracked as CVE-2021-30632 and CVE-2021-30633, the vulnerabilities concern an out of bounds write in V8 JavaScript engine and a use after free flaw in Indexed DB API respectively, with the internet giant … [Read more...] about Update Google Chrome to Patch 2 New Zero-Day Flaws Under Attack
Mēris Botnet Hit Russia’s Yandex With Massive 22 Million RPS DDoS Attack
Russian internet giant Yandex has been the target of a record-breaking distributed denial-of-service (DDoS) attack by a new botnet called Mēris. The botnet is believed to have pummeled the company's web infrastructure with millions of HTTP requests, before hitting a peak of 21.8 million requests per second (RPS), dwarfing a recent botnet-powered attack that came to light last … [Read more...] about Mēris Botnet Hit Russia’s Yandex With Massive 22 Million RPS DDoS Attack
Microsoft Says Chinese Hackers Were Behind SolarWinds Serv-U SSH 0-Day Attack
Microsoft has shared technical details about a now-fixed, actively exploited critical security vulnerability affecting SolarWinds Serv-U managed file transfer service that it has attributed with "high confidence" to a threat actor operating out of China. In mid-July, the Texas-based company remedied a remote code execution flaw (CVE-2021-35211) that was rooted in Serv-U's … [Read more...] about Microsoft Says Chinese Hackers Were Behind SolarWinds Serv-U SSH 0-Day Attack
What is AS-REP Roasting attack, really?
Microsoft's Active Directory is said to be used by 95% of Fortune 500. As a result, it is a prime target for attackers as they look to gain access to credentials in the organization, as compromised credentials provide one of the easiest ways for hackers to access your data. A key authentication technology that underpins Microsoft Active Directory is Kerberos. Unfortunately, … [Read more...] about What is AS-REP Roasting attack, really?
Microsoft Exchange Under Attack With ProxyShell Flaws
The U.S. Cybersecurity and Infrastructure Security Agency is warning of active exploitation attempts that leverage the latest line of "ProxyShell" Microsoft Exchange vulnerabilities that were patched earlier this May, including deploying LockFile ransomware on compromised systems. Tracked as CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207, the vulnerabilities enable … [Read more...] about Microsoft Exchange Under Attack With ProxyShell Flaws
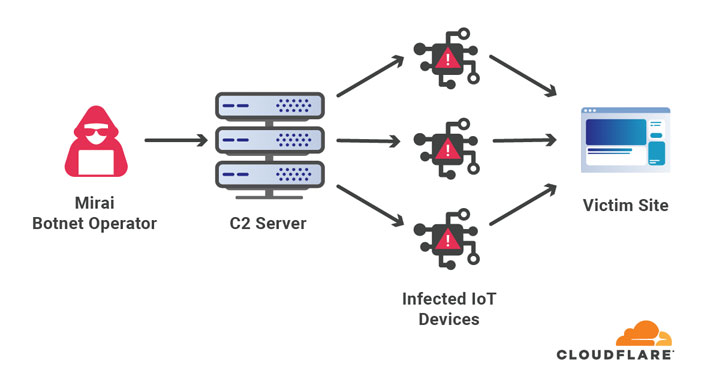
Cloudflare mitigated one of the largest DDoS attack involving 17.2 million rps
Web infrastructure and website security company Cloudflare on Thursday disclosed that it mitigated the largest ever volumetric distributed denial of service (DDoS) attack recorded to date. The attack, launched via a Mirai botnet, is said to have targeted an unnamed customer in the financial industry last month. "Within seconds, the botnet bombarded the Cloudflare edge with over … [Read more...] about Cloudflare mitigated one of the largest DDoS attack involving 17.2 million rps
New Glowworm Attack Recovers Device’s Sound from Its LED Power Indicator
A novel technique leverages optical emanations from a device's power indicator LED to recover sounds from connected peripherals and spy on electronic conversations from a distance of as much as 35 meters. Dubbed the "Glowworm attack," the findings were published by a group of academics from the Ben-Gurion University of the Negev earlier this week, describing the method as "an … [Read more...] about New Glowworm Attack Recovers Device’s Sound from Its LED Power Indicator
Anatomy of a Breach: Preventing the Next Advanced Attack
Your company’s stock price nosedives by 15% in a single day. You get a flood of messages from concerned family and friends about your company. Your company’s name is all over the news. Your colleagues exchange hundreds of frantic messages while trying to figure out what happened and how to respond. This is what it looks like when your organization is breached. I know this from … [Read more...] about Anatomy of a Breach: Preventing the Next Advanced Attack