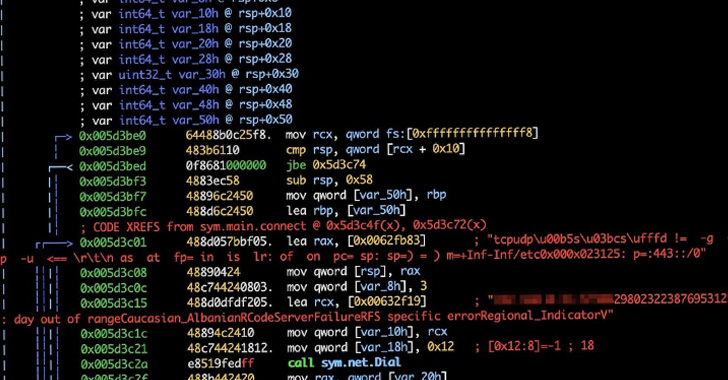
A newly discovered evasive malware leverages the Secure Shell (SSH) cryptographic protocol to gain entry into targeted systems with the goal of mining cryptocurrency and carrying out distributed denial-of-service (DDoS) attacks. Dubbed KmsdBot by the Akamai Security Intelligence Response Team (SIRT), the Golang-based malware has been found targeting a variety of companies … [Read more...] about New KmsdBot Malware Hijacking Systems for Mining Crypto and Launch DDoS Attacks
attacks
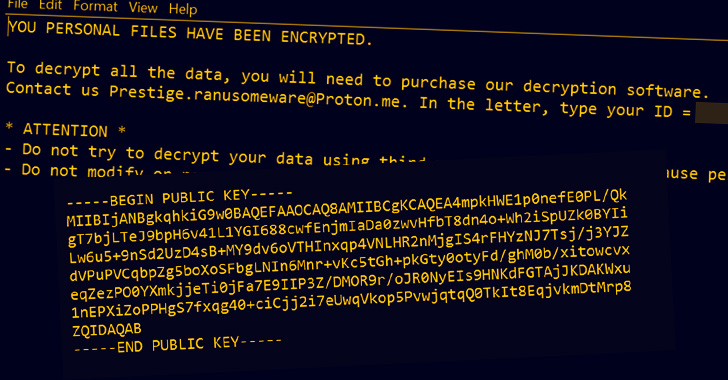
Microsoft Blames Russian Hackers for Prestige Ransomware Attacks on Ukraine and Poland
Microsoft on Thursday attributed the recent spate of ransomware incidents targeting transportation and logistics sectors in Ukraine and Poland to a threat cluster that shares overlaps with the Russian state-sponsored Sandworm group. The attacks, which were disclosed by the tech giant last month, involved a strain of previously undocumented malware called Prestige and is said to … [Read more...] about Microsoft Blames Russian Hackers for Prestige Ransomware Attacks on Ukraine and Poland
How can I help protect my company from phishing attacks?
I’m sure you’ve seen them — emails or messages that sound alarming and ask you to act quickly. We live in a digital world that produces hundreds of messages and alerts every day. It’s often hard to determine the validity of a suspicious message or phishing email. Whether you are an administrator, or an end-user, it can be overwhelming to accurately identify a malicious message. … [Read more...] about How can I help protect my company from phishing attacks?
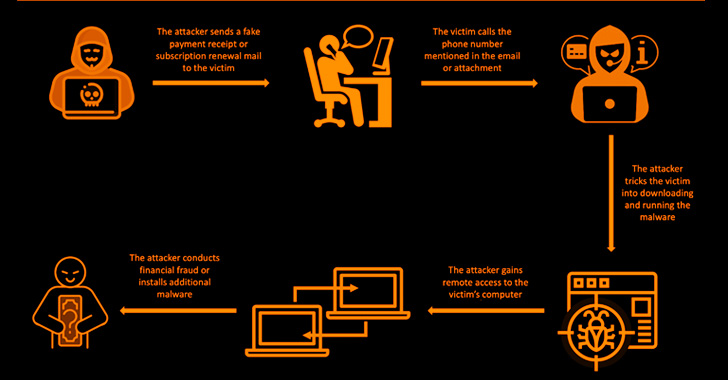
BazarCall Callback Phishing Attacks Constantly Evolving Its Social Engineering Tactics
The operators behind the BazaCall call back phishing method have continued to evolve with updated social engineering tactics to deploy malware on targeted networks. The scheme eventually acts as an entry point to conduct financial fraud or the delivery of next-stage payloads such as ransomware, cybersecurity company Trellix said in a report published last week. Primary targets … [Read more...] about BazarCall Callback Phishing Attacks Constantly Evolving Its Social Engineering Tactics
Defend your organization from ransomware attacks with Cisco Secure Endpoint
Ransomware is one of the most dangerous threats organizations face today, so it’s no wonder that Cisco Talos Incident Response named it the top threat of the year in 2021. These attacks continue to grow and become more advanced, with ransomware attacks growing by 13% over 2021 and a whopping 79% over 2020 so far this year (see Figure 1 below).1 Stopping ransomware attacks … [Read more...] about Defend your organization from ransomware attacks with Cisco Secure Endpoint
Iranian APT42 Launched Over 30 Espionage Attacks Against Activists and Dissidents
A state-sponsored advanced persistent threat (APT) actor newly christened APT42 (formerly UNC788) has been attributed to over 30 confirmed espionage attacks against individuals and organizations of strategic interest to the Iranian government at least since 2015. Cybersecurity firm Mandiant said the group operates as the intelligence gathering arm of Iran's Islamic … [Read more...] about Iranian APT42 Launched Over 30 Espionage Attacks Against Activists and Dissidents
Some Members of Conti Group Targeting Ukraine in Financially Motivated Attacks
Former members of the Conti cybercrime cartel have been implicated in five different campaigns targeting Ukraine from April to August 2022. The findings, which come from Google's Threat Analysis Group (TAG), builds upon a prior report published in July 2022, detailing the continued cyber activity aimed at the Eastern European nation amid the ongoing Russo-Ukrainian … [Read more...] about Some Members of Conti Group Targeting Ukraine in Financially Motivated Attacks
Conti Cybercrime Cartel Using ‘BazarCall’ Phishing Attacks as Initial Attack Vector
Three different offshoots of the notorious Conti cybercrime cartel have resorted to the technique of call-back phishing as an initial access vector to breach targeted networks. "Three autonomous threat groups have since adopted and independently developed their own targeted phishing tactics derived from the call back phishing methodology," cybersecurity firm AdvIntel said in a … [Read more...] about Conti Cybercrime Cartel Using ‘BazarCall’ Phishing Attacks as Initial Attack Vector
Detecting NTLM Relay Attacks with CrowdStrike Identity Protection
Adversaries often exploit legacy protocols like Windows NTLM that unfortunately remain widely deployed despite known vulnerabilities. Previous CrowdStrike blog posts have covered critical vulnerabilities in NTLM that allow remote code execution and other NTLM attacks where attackers could exploit vulnerabilities to bypass MIC (Message Integrity Code) protection, session signing … [Read more...] about Detecting NTLM Relay Attacks with CrowdStrike Identity Protection
New Study Finds Most Enterprise Vendors Failing to Mitigate Speculative Execution Attacks
With speculative execution attacks remaining a stubbornly persistent vulnerability ailing modern processors, new research has highlighted an "industry failure" to adopting mitigations released by AMD and Intel, posing a firmware supply chain threat. Dubbed FirmwareBleed by Binarly, the information leaking assaults stem from the continued exposure of microarchitectural attack … [Read more...] about New Study Finds Most Enterprise Vendors Failing to Mitigate Speculative Execution Attacks