Jan 11, 2025Ravie LakshmananAI Security / Cybersecurity Microsoft has revealed that it's pursuing legal action against a "foreign-based threat–actor group" for operating a hacking-as-a-service infrastructure to intentionally get around the safety controls of its generative artificial intelligence (AI) services and produce offensive and harmful content. The tech giant's … [Read more...] about Microsoft Sues Hacking Group Exploiting Azure AI for Harmful Content Creation
Azure
Elastic Cloud Serverless coming soon on Microsoft Azure for cost-efficient scalability
Building on the success of Elastic's Azure Native ISV Service and its availability on the Azure Marketplace, Elastic Cloud Serverless on Microsoft Azure takes cloud innovation a step further. As we think about the next decade, we recognize the need for a simpler user experience that still delivers fast performance. Elastic Cloud Serverless now provides hassle-free operations … [Read more...] about Elastic Cloud Serverless coming soon on Microsoft Azure for cost-efficient scalability
Cisco Secure Firewall integrates with Azure Virtual WAN (vWAN) to simplify firewall insertion in Azure environments
Enterprise networks have become more complex as the number of branches, data centers, and cloud deployments have increased. The complex spiderweb of connectivity makes it challenging to comprehensively secure all the applications and workloads without needing to deploy firewalls everywhere. To help customers manage complex connectivity, Microsoft Azure launched the Virtual WAN … [Read more...] about Cisco Secure Firewall integrates with Azure Virtual WAN (vWAN) to simplify firewall insertion in Azure environments
Get started with Elastic AI Assistant for Observability and Microsoft Azure OpenAI
Recently, Elastic announced the AI Assistant for Observability is now generally available for all Elastic users. The AI Assistant enables a new tool for Elastic Observability providing large language model (LLM) connected chat and contextual insights to explain errors and suggest remediation. Similar to how Microsoft Copilot is an AI companion that introduces new capabilities … [Read more...] about Get started with Elastic AI Assistant for Observability and Microsoft Azure OpenAI
5 Best Practices for Securing Azure Resources
Cloud computing has become the backbone for modern businesses due to its scalability, flexibility and cost-efficiency. As organizations choose cloud service providers to power their technological transformations, they must also properly secure their cloud environments to protect sensitive data, maintain privacy and comply with stringent regulatory requirements. Today’s … [Read more...] about 5 Best Practices for Securing Azure Resources
CrowdStrike Defends Against Azure Cross-Tenant Synchronization Attacks
Azure cross-tenant synchronization (CTS) was made generally available on May 30, 2023, and introduced a new attack surface on Microsoft Entra ID (formerly Azure Active Directory) where attackers can move laterally to a partner tenant or create a backdoor on an existing tenant. CrowdStrike showcases two observed attack paths to outline how adversaries can abuse CTS CrowdStrike … [Read more...] about CrowdStrike Defends Against Azure Cross-Tenant Synchronization Attacks
Migrate self-managed Elastic stack to Elastic Cloud using Azure Blob Storage
The process of migration involves taking a snapshot of the data in the self-managed Elastic stack, saving that snapshot to an Azure Blob Storage Container, and then restoring the snapshot to your Elastic Cloud deployment. Here’s a guided tour of all the steps to accomplish this right within your browser.While the migration process covered in this blog post migrates an Elastic … [Read more...] about Migrate self-managed Elastic stack to Elastic Cloud using Azure Blob Storage
How to deploy and manage Elasticsearch on Azure
2. Click on the checkboxes for subscription activity logs and/or resource logs.3. Optionally, you can specify tag rules to include or exclude specific resources from log collection. By default, if no tag rule is specified, the logs from all supported resources will be ingested.4. Select Save (or finish creating your resource). Log data will begin to appear in Elastic shortly … [Read more...] about How to deploy and manage Elasticsearch on Azure
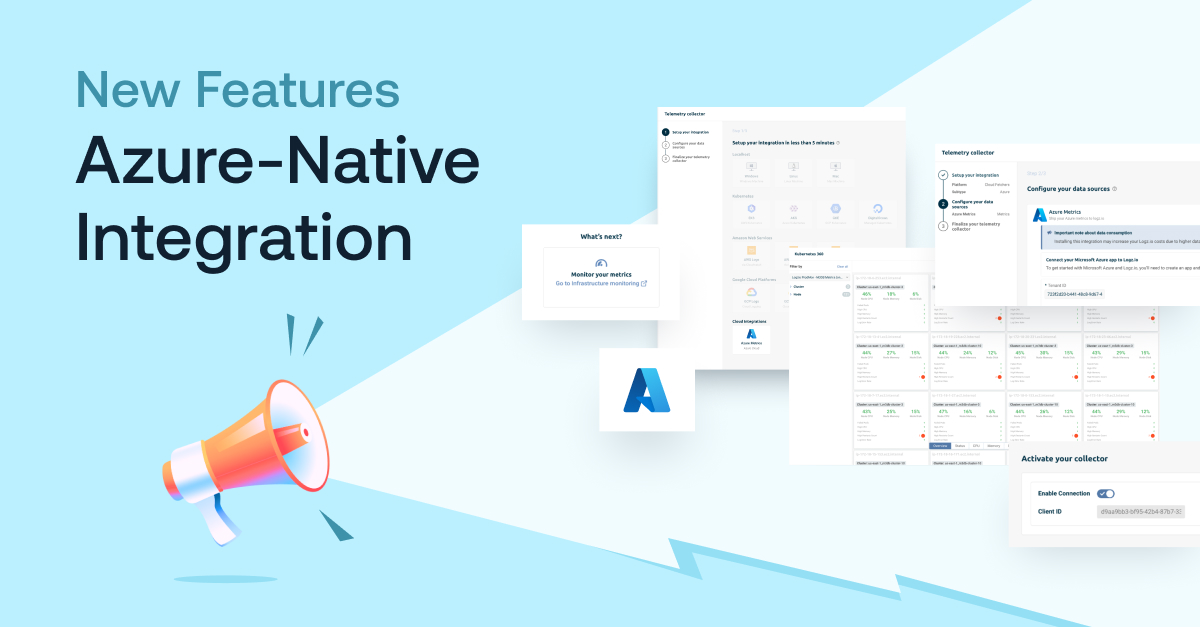
Simplify Azure Monitoring with Logz.io’s New Azure-Native Integration
If you’re looking to monitor Microsoft Azure infrastructure with Logz.io, we’re now making it easier than ever with our new Azure-native integrationTypically, collecting infrastructure metrics from Azure involves installing and configuring data collection components on your system, such as Prometheus, Telegraph, or a number of proprietary agents that are specific to different … [Read more...] about Simplify Azure Monitoring with Logz.io’s New Azure-Native Integration
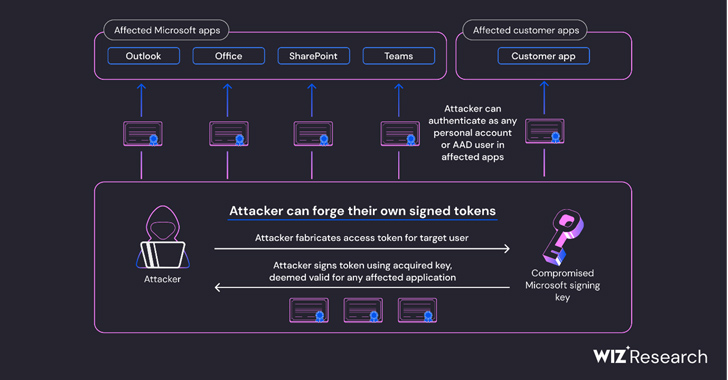
Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports
Jul 21, 2023THNEmail Security / Cyber Attack The recent attack against Microsoft's email infrastructure by a Chinese nation-state actor referred to as Storm-0558 is said to have a broader scope than previously thought. According to cloud security company Wiz, the inactive Microsoft account (MSA) consumer signing key used to forge Azure Active Directory (Azure AD or AAD) … [Read more...] about Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports