Sep 12, 2024Ravie LakshmananMobile Security / Financial Fraud Bank customers in the Central Asia region have been targeted by a new strain of Android malware codenamed Ajina.Banker since at least November 2024 with the goal of harvesting financial information and intercepting two-factor authentication (2FA) messages. Singapore-headquartered Group-IB, which discovered the … [Read more...] about New Android Malware ‘Ajina.Banker’ Steals Financial Data and Bypasses 2FA via Telegram
bypasses
New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections
Jan 01, 2024NewsroomWindows Security / Vulnerability Security researchers have detailed a new variant of a dynamic link library (DLL) search order hijacking technique that could be used by threat actors to bypass security mechanisms and achieve execution of malicious code on systems running Microsoft Windows 10 and Windows 11. The approach "leverages executables commonly … [Read more...] about New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections
New Exploit Bypasses Existing Spectre-V2 Mitigations in Intel, AMD, Arm CPUs
Researchers have disclosed a new technique that could be used to circumvent existing hardware mitigations in modern processors from Intel, AMD, and Arm, and stage speculative execution attacks such as Spectre to leak sensitive information from host memory. Attacks like Spectre are designed to break the isolation between different applications by taking advantage of an … [Read more...] about New Exploit Bypasses Existing Spectre-V2 Mitigations in Intel, AMD, Arm CPUs
New Blacksmith Exploit Bypasses Current Rowhammer Attack Defenses
Cybersecurity researchers have demonstrated yet another variation of the Rowhammer attack affecting all DRAM (dynamic random-access memory) chips that bypasses currently deployed mitigations, thereby effectively compromising the security of the devices. The new technique — dubbed "Blacksmith" (CVE-2021-42114, CVSS score: 9.0) — is designed to trigger bit flips on target refresh … [Read more...] about New Blacksmith Exploit Bypasses Current Rowhammer Attack Defenses
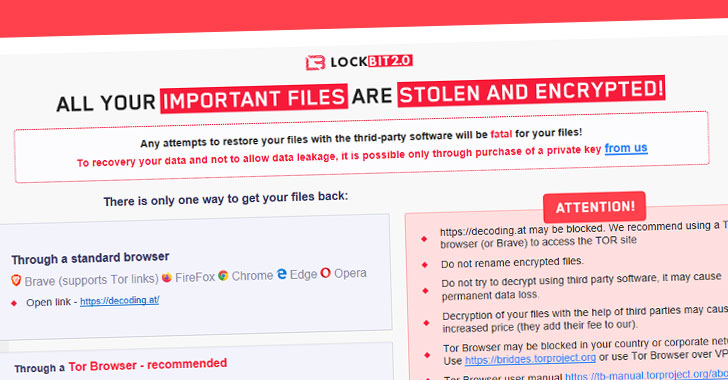
LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "intermittent encryption." Called LockFile, the operators of the ransomware has been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware … [Read more...] about LockFile Ransomware Bypasses Protection Using Intermittent File Encryption