“There’s so much left to know, and I’m on the road to find out.” –Cat Stevens (Yusuf) Two years ago, we asked the question: What actually works in cybersecurity? Not what everyone’s doing—because there are plenty of cybersecurity reports out there that answer that question—but which data-backed practices lead to the outcomes we want to implement in cybersecurity strategies? The … [Read more...] about Cracking the Code to Security Resilience: Lessons from the Latest Cisco Security Outcomes Report
CODE
Hackers Breach LastPass Developer System to Steal Source Code
Password management service LastPass confirmed a security incident that resulted in the theft of certain source code and technical information. The security breach is said to have occurred two weeks ago, targeting its development environment. No customer data or encrypted passwords were accessed, although the company provided no further details regarding the hack and what … [Read more...] about Hackers Breach LastPass Developer System to Steal Source Code
An Easier Way to Keep Old Python Code Healthy and Secure
Python has its pros and cons, but it's nonetheless used extensively. For example, Python is frequently used in data crunching tasks even when there are more appropriate languages to choose from. Why? Well, Python is relatively easy to learn. Someone with a science background can pick up Python much more quickly than, say, C. However, Python's inherent approachability also … [Read more...] about An Easier Way to Keep Old Python Code Healthy and Secure
T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code
Telecom company T-Mobile on Friday confirmed that it was the victim of a security breach in March after the LAPSUS$ mercenary gang managed to gain access to its networks. The acknowledgment came after investigative journalist Brian Krebs shared internal chats belonging to the core members of the group indicating that LAPSUS$ breached the company several times in March prior to … [Read more...] about T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code
Code coverage for eBPF programs
By analyzing the resulting LLVM IR for source-based coverage instrumented programs, we should now have a better understanding of what we need to do for having it on eBPF programs running in the Linux kernel. We now know what to completely get rid of and do differently, and what we need to patch to make it loadable and usable by the BPF VM in the kernel.The plan is simple: get … [Read more...] about Code coverage for eBPF programs
New BLISTER Malware Using Code Signing Certificates to Evade Detection
Cybersecurity researchers have disclosed details of an evasive malware campaign that makes use of valid code signing certificates to sneak past security defenses and stay under the radar with the goal of deploying Cobalt Strike and BitRAT payloads on compromised systems. The binary, a loader, has been dubbed "Blister" by researchers from Elastic Security, with the malware … [Read more...] about New BLISTER Malware Using Code Signing Certificates to Evade Detection
Experts Detail Malicious Code Dropped Using ManageEngine ADSelfService Exploit
At least nine entities across the technology, defense, healthcare, energy, and education industries were compromised by leveraging a recently patched critical vulnerability in Zoho's ManageEngine ADSelfService Plus self-service password management and single sign-on (SSO) solution. The spying campaign, which was observed starting September 22, 2021, involved the threat actor … [Read more...] about Experts Detail Malicious Code Dropped Using ManageEngine ADSelfService Exploit
Webex by Cisco earns adherence to the EU Cloud Code of Conduct
With the 2018 General Data Protection Regulation (GDPR), Europe marked a big step in strengthening individuals’ privacy rights. While the GDPR aims to bring consistency to the data protection landscape, incorporating well-recognized privacy principles like transparency, fairness, and accountability – operationalizing it has been a challenge. Even before GDPR enforcement, Cisco, … [Read more...] about Webex by Cisco earns adherence to the EU Cloud Code of Conduct
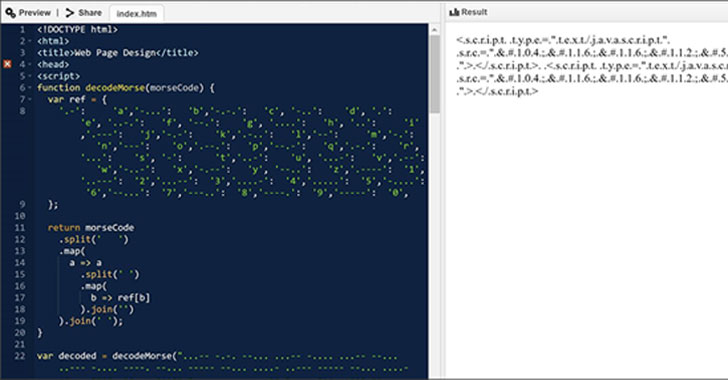
Hackers Spotted Using Morse Code in Phishing Attacks to Evade Detection
Microsoft has disclosed details of an evasive year-long social engineering campaign wherein the operators kept changing their obfuscation and encryption mechanisms every 37 days on average, including relying on Morse code, in an attempt to cover their tracks and surreptitiously harvest user credentials. The phishing attacks take the form of invoice-themed lures mimicking … [Read more...] about Hackers Spotted Using Morse Code in Phishing Attacks to Evade Detection
Wake up! Identify API Vulnerabilities Proactively, From Production Back to Code
After more than 20 years in the making, now it's official: APIs are everywhere. In a 2021 survey, 73% of enterprises reported that they already publish more than 50 APIs, and this number is constantly growing. APIs have crucial roles to play in virtually every industry today, and their importance is increasing steadily, as they move to the forefront of business strategies. This … [Read more...] about Wake up! Identify API Vulnerabilities Proactively, From Production Back to Code