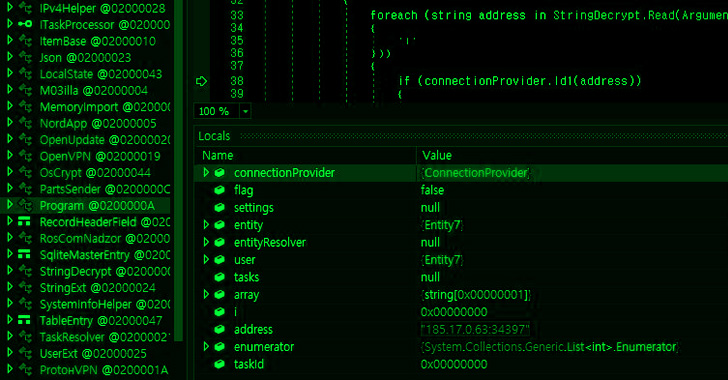
Jan 29, 2025Ravie LakshmananThreat Intelligence / Malware The North Korean threat actor known as the Lazarus Group has been observed leveraging a "web-based administrative platform" to oversee its command-and-control (C2) infrastructure, giving the adversary the ability to centrally supervise all aspects of their campaigns. "Each C2 server hosted a web-based administrative … [Read more...] about Lazarus Group Uses React-Based Admin Panel to Control Global Cyber Attacks
Control
Cyberattackers Exploit Google Sheets for Malware Control in Likely Espionage Campaign
Cybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism. The activity, detected by Proofpoint starting August 5, 2024, impersonates tax authorities from governments in Europe, Asia, and the U.S., with the goal of targeting over 70 organizations worldwide by means of a bespoke tool called Voldemort … [Read more...] about Cyberattackers Exploit Google Sheets for Malware Control in Likely Espionage Campaign
Researchers Uncover Flaws in Windows Smart App Control and SmartScreen
Aug 05, 2024Ravie LakshmananThreat Intelligence / Vulnerability Cybersecurity researchers have uncovered design weaknesses in Microsoft's Windows Smart App Control and SmartScreen that could enable threat actors to gain initial access to target environments without raising any warnings. Smart App Control (SAC) is a cloud-powered security feature introduced by Microsoft in … [Read more...] about Researchers Uncover Flaws in Windows Smart App Control and SmartScreen
Security Cloud Control: Pioneering the Future of Security Management
Organizations face a critical challenge today: attackers are exploiting the weakest links in their networks, such as unsecured users, devices, and workloads. This threat landscape is complicated by the shift from traditional data centers to a distributed environment, where protecting dispersed data across multiple touchpoints becomes complex. To address these threats, many … [Read more...] about Security Cloud Control: Pioneering the Future of Security Management
Google Kubernetes Misconfig Lets Any Gmail Account Control Your Clusters
Jan 24, 2024NewsroomCloud Security / Kubernetes Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Engine (GKE) that could be potentially exploited by threat actors with a Google account to take control of a Kubernetes cluster. The critical shortcoming has been codenamed Sys:All by cloud security firm Orca. As many as 250,000 active GKE clusters … [Read more...] about Google Kubernetes Misconfig Lets Any Gmail Account Control Your Clusters
Hackers Abusing GitHub to Evade Detection and Control Compromised Hosts
Dec 19, 2023The Hacker NewsSoftware Security / Threat intelligence Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret Gists and issuing malicious commands via git commit messages. "Malware authors occasionally place their samples in services like Dropbox, Google Drive, OneDrive, and Discord to host second … [Read more...] about Hackers Abusing GitHub to Evade Detection and Control Compromised Hosts
Take control of your Elastic Cloud spend with data-driven insights
As we continue to expand our product offerings, new products, and services will be integrated into the usage page. The latest addition to this offering is Synthetic Monitoring. This feature offers insights into the utilization and expenses associated with synthetics products, making it easier to manage and optimize your overall spending.We encourage you to explore the enriched … [Read more...] about Take control of your Elastic Cloud spend with data-driven insights
Industrial control systems security with Elastic Security and Zeek
Keeping track of all ICS asset history and accurate status in a global inventory is critical not only for purposes like maintenance, cost management, and environment optimization but also for the system's security. Well-implemented and maintained inventories are key to ICS security programs, since you can’t protect what you don’t know about. Knowing what is on the ICS network, … [Read more...] about Industrial control systems security with Elastic Security and Zeek
CISA Warns of Flaws in Siemens, GE Digital, and Contec Industrial Control Systems
Jan 18, 2023Ravie LakshmananICS/SCADA Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published four Industrial Control Systems (ICS) advisories, calling out several security flaws affecting products from Siemens, GE Digital, and Contec. The most critical of the issues have been identified in Siemens SINEC INS that could lead to remote code … [Read more...] about CISA Warns of Flaws in Siemens, GE Digital, and Contec Industrial Control Systems
Crypto Miners Using Tox P2P Messenger as Command and Control Server
Threat actors have begun to use the Tox peer-to-peer instant messaging service as a command-and-control method, marking a shift from its earlier role as a contact method for ransomware negotiations. The findings from Uptycs, which analyzed an Executable and Linkable Format (ELF) artifact ("72client") that functions as a bot and can run scripts on the compromised host using the … [Read more...] about Crypto Miners Using Tox P2P Messenger as Command and Control Server