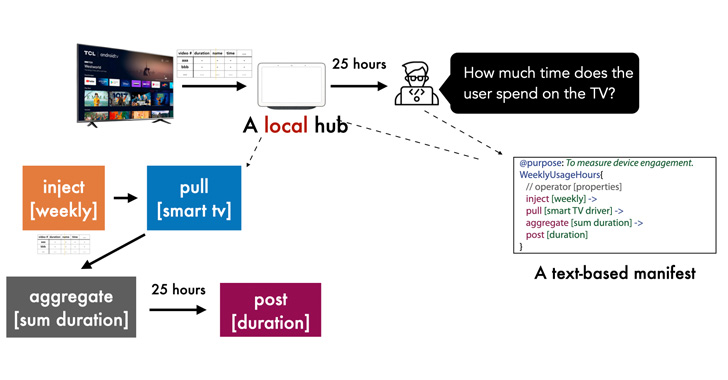
A newly designed privacy-sensitive architecture aims to enable developers to create smart home apps in a manner that addresses data sharing concerns and puts users in control over their personal information. Dubbed Peekaboo by researchers from Carnegie Mellon University, the system "leverages an in-home hub to pre-process and minimize outgoing data in a structured and … [Read more...] about New Privacy Framework for IoT Devices Gives Users Control Over Data Sharing
Control
JekyllBot:5 Flaws Let Attackers Take Control of Aethon TUG Hospital Robots
As many as five security vulnerabilities have been addressed in Aethon Tug hospital robots that could enable remote attackers to seize control of the devices and interfere with the timely distribution of medication and lab samples. "Successful exploitation of these vulnerabilities could cause a denial-of-service condition, allow full control of robot functions, or expose … [Read more...] about JekyllBot:5 Flaws Let Attackers Take Control of Aethon TUG Hospital Robots
Taking Full Control of your Telemetry with the Intelligent Telemetry Plane
Earlier this year, we introduced the Cisco Telemetry Broker (CTB) and showed customers how it can free their telemetry from proprietary protocols and allow them to use the tools and solutions they already have in place to coexist seamlessly. Today, we would like to introduce you all to the notion of the Intelligent Telemetry Plane. Products in the market today like the UDP … [Read more...] about Taking Full Control of your Telemetry with the Intelligent Telemetry Plane
Building Consumer Confidence Through Transparency and Control
Protecting privacy continues to be a critical issue for individuals, organizations, and governments around the world. Eighteen months into the COVID-19 pandemic, our health information and vaccination status are needed more than ever to understand the virus, control the spread, and enable safer environments for work, learning, recreation, and other activities. Nonetheless, … [Read more...] about Building Consumer Confidence Through Transparency and Control
Control Across Your Hybrid Environments Using Cisco Secure Workload 3.6
Business needs are driving significant changes in today’s datacenters. Enterprises are not only migrating applications to the cloud from on-premises data centers, but they are developing multicloud strategies that take advantage of availability, global footprint, and cost saving structures. In fact, IDC has predicted that more than 90% of IT organizations will commit to … [Read more...] about Control Across Your Hybrid Environments Using Cisco Secure Workload 3.6
The Risk-Conscious, Security-Aware Culture: The Forgotten Critical Security Control
Chief Information Security Officers (CISOs) across the Global 2000 and Fortune 1000 are obsessed with protecting the workforce endpoints as critical vulnerabilities in the cybersecurity and risk management posture of their enterprises. CISOs focus on cybersecurity controls that operate mostly transparently and are focused on mitigating the potential risks to the computing … [Read more...] about The Risk-Conscious, Security-Aware Culture: The Forgotten Critical Security Control
Cisco Firewalls and ISE Extend Zero Trust Network Visibility and Control
As the number of remote workers continues to grow worldwide, organizations are diligently seeking to strike the right balance between security and convenience. Employees utilize a wide variety of devices to access company web sites, applications, and data. Some devices are maintained by the company and therefore assumed to be secure, but many devices are provided by employees … [Read more...] about Cisco Firewalls and ISE Extend Zero Trust Network Visibility and Control