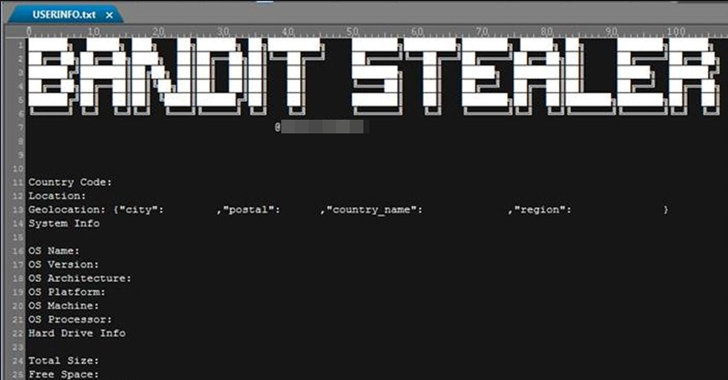
A new stealthy information stealer malware called Bandit Stealer has caught the attention of cybersecurity researchers for its ability to target numerous web browsers and cryptocurrency wallets. "It has the potential to expand to other platforms as Bandit Stealer was developed using the Go programming language, possibly allowing cross-platform compatibility," Trend Micro said … [Read more...] about New Stealthy Bandit Stealer Targeting Web Browsers and Cryptocurrency Wallets
cyber attacks
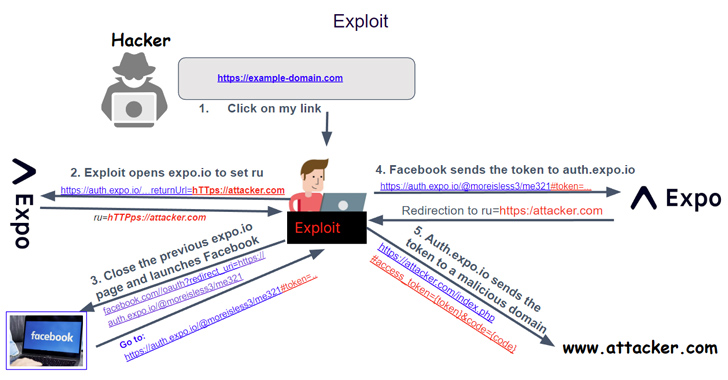
Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
May 27, 2023Ravie LakshmananAPI Security / Vulnerability A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development framework Expo.io. The shortcoming, assigned the CVE identifier CVE-2023-28131, has a severity rating of 9.6 on the CVSS scoring system. API security firm Salt Labs said the issue rendered … [Read more...] about Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
May 26, 2023Ravie LakshmananICS/SCADA Security A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unearthed. Google-owned threat intelligence firm Mandiant dubbed the malware COSMICENERGY, adding it was uploaded to a public malware scanning utility in December 2021 by a submitter in Russia. There … [Read more...] about New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
China’s Stealthy Hackers Infiltrate U.S. and Guam Critical Infrastructure Undetected
May 25, 2023Ravie LakshmananCyber Threat / Espionage A stealthy China-based group managed to establish a persistent foothold into critical infrastructure organizations in the U.S. and Guam without being detected, Microsoft and the "Five Eyes" nations said on Wednesday. The tech giant's threat intelligence team is tracking the activity, which includes post-compromise … [Read more...] about China’s Stealthy Hackers Infiltrate U.S. and Guam Critical Infrastructure Undetected
What to Look for When Selecting a Static Application Security Testing (SAST) Solution
If you're involved in securing the applications your organization develops, there is no question that Static Application Security Testing (SAST) solutions are an important part of a comprehensive application security strategy. SAST secures software, supports business more securely, cuts down on costs, reduces risk, and speeds time to development, delivery, and deployment of … [Read more...] about What to Look for When Selecting a Static Application Security Testing (SAST) Solution
China Bans U.S. Chip Giant Micron, Citing “Serious Cybersecurity Problems”
May 23, 2023Ravie LakshmananNational Security / Hardware China has banned U.S. chip maker Micron from selling its products to Chinese companies working on key infrastructure projects, citing national security risks. The development comes nearly two months after the country's cybersecurity authority initiated a probe in late March 2023 to assess potential network security … [Read more...] about China Bans U.S. Chip Giant Micron, Citing “Serious Cybersecurity Problems”
Are Your APIs Leaking Sensitive Data?
It's no secret that data leaks have become a major concern for both citizens and institutions across the globe. They can cause serious damage to an organization's reputation, induce considerable financial losses, and even have serious legal repercussions. From the infamous Cambridge Analytica scandal to the Equifax data breach, there have been some pretty high-profile leaks … [Read more...] about Are Your APIs Leaking Sensitive Data?
User Sign-Ups and Package Uploads Temporarily Halted
May 21, 2023Ravie LakshmananSoftware Security / Malware The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have temporarily disabled the ability for users to sign up and upload new packages until further notice. "The volume of malicious users and malicious projects being created on the index in the … [Read more...] about User Sign-Ups and Package Uploads Temporarily Halted
Notorious Cyber Gang FIN7 Returns Cl0p Ransomware in New Wave of Attacks
May 20, 2023Ravie LakshmananCyber Crime / Ransomware The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ransomware campaign since late 2021. Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest. "In these recent … [Read more...] about Notorious Cyber Gang FIN7 Returns Cl0p Ransomware in New Wave of Attacks
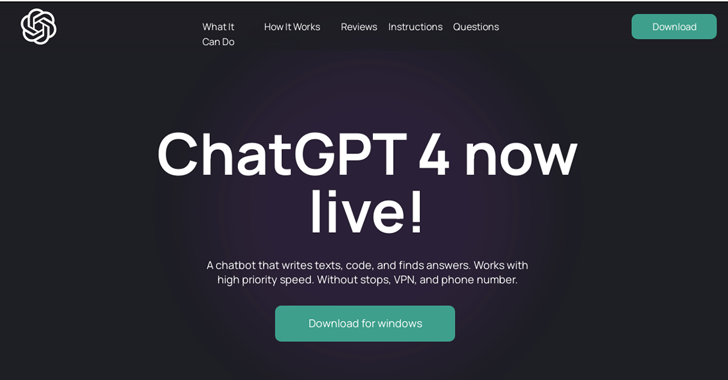
Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware
May 19, 2023Ravie LakshmananArtificial Intelligence / Cyber Threat Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware. "Both AI services are extremely popular but lack first-party standalone apps (i.e., users … [Read more...] about Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware