Misconfigurations in multiple Android apps leaked sensitive data of more than 100 million users, potentially making them a lucrative target for malicious actors. "By not following best-practices when configuring and integrating third-party cloud-services into applications, millions of users' private data was exposed," Check Point researchers said in an analysis published today … [Read more...] about 23 Android Apps Expose Over 100,000,000 Users’ Personal Data
data
How Apple Gave Chinese Government Access to iCloud Data and Censored Apps
In July 2018, when Guizhou-Cloud Big Data (GCBD) agreed to a deal with state-owned telco China Telecom to move users' iCloud data belonging to Apple's China-based users to the latter's servers, the shift raised concerns that it could make user data vulnerable to state surveillance. Now, according to a deep-dive report from The New York Times, Apple's privacy and security … [Read more...] about How Apple Gave Chinese Government Access to iCloud Data and Censored Apps
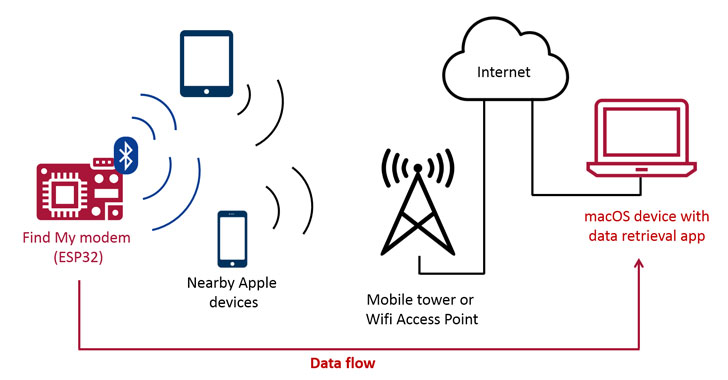
Apple’s Find My Network Can be Abused to Exfiltrate Data From Nearby Devices
Latest research has demonstrated a new exploit that enables arbitrary data to be uploaded from devices that are not connected to the Internet by simply sending "Find My Bluetooth" broadcasts to nearby Apple devices. "It's possible to upload arbitrary data from non-internet-connected devices by sending Find My [Bluetooth Low Energy] broadcasts to nearby Apple devices that then … [Read more...] about Apple’s Find My Network Can be Abused to Exfiltrate Data From Nearby Devices
Can Data Protection Systems Prevent Data At Rest Leakage?
Protection against insider risks works when the process involves controlling the data transfer channels or examining data sources. One approach involves preventing USB flash drives from being copied or sending them over email. The second one concerns preventing leakage or fraud in which an insider accesses files or databases with harmful intentions. What's the best way to … [Read more...] about Can Data Protection Systems Prevent Data At Rest Leakage?
533 Million Facebook Users’ Phone Numbers and Personal Data Leaked Online
In what's likely to be a goldmine for bad actors, personal information associated with approximately 533 million Facebook users worldwide has been leaked on a popular cybercrime forum for free—which was harvested by hackers in 2019 using a Facebook vulnerability. The leaked data includes full names, Facebook IDs, mobile numbers, locations, email addresses, gender, occupation, … [Read more...] about 533 Million Facebook Users’ Phone Numbers and Personal Data Leaked Online
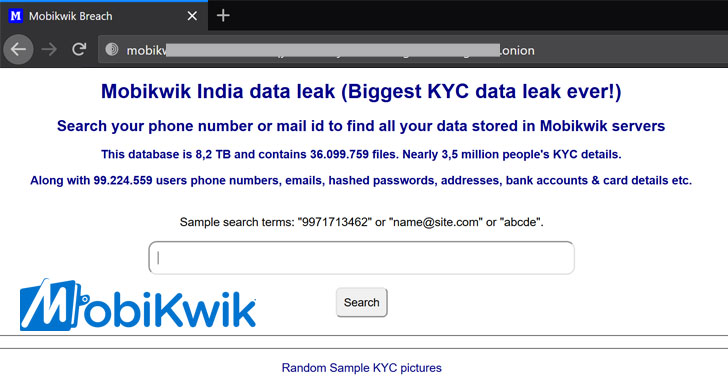
MobiKwik Suffers Major Breach — KYC Data of 3.5 Million Users Exposed
Popular Indian mobile payments service MobiKwik on Monday came under fire after 8.2 terabytes (TB) of data belonging to millions of its users began circulating on the dark web in the aftermath of a major data breach that came to light earlier this month. The leaked data includes sensitive personal information such as:customer names,hashed passwords,email addresses,residential … [Read more...] about MobiKwik Suffers Major Breach — KYC Data of 3.5 Million Users Exposed
Data Breach Exposes 1.6 Million Jobless Claims Filed in the Washington State
The Office of the Washington State Auditor (SAO) on Monday said it's investigating a security incident that resulted in the compromise of personal information of more than 1.6 million people who filed for unemployment claims in the state in 2020. The SAO blamed the breach on a software vulnerability in Accellion's File Transfer Appliance (FTA) service, which allows … [Read more...] about Data Breach Exposes 1.6 Million Jobless Claims Filed in the Washington State
Desktops in the Data Center: Establishing ground rules for VDI
Since the earliest days of computing, we’ve endeavored to provide users with efficient, secure access to the critical applications which power the business. From those early mainframe applications being accessed from hard-wired dumb terminals to the modern cloud-based application architectures of today, accessible to any user, from anywhere, on any device, we’ve witnessed the … [Read more...] about Desktops in the Data Center: Establishing ground rules for VDI
WhatsApp Will Delete Your Account If You Don’t Agree Sharing Data With Facebook
"Respect for your privacy is coded into our DNA," opens WhatsApp's privacy policy. "Since we started WhatsApp, we've aspired to build our Services with a set of strong privacy principles in mind." But come February 8, 2021, this opening statement will no longer find a place in the policy. The Facebook-owned messaging service is alerting users in India of an update to its terms … [Read more...] about WhatsApp Will Delete Your Account If You Don’t Agree Sharing Data With Facebook
Introducing the Cisco Secure Network Analytics Data Store!
Security professionals are currently facing a big data conundrum If you work in IT networking or security, you’re all too familiar with how difficult it can be to effectively manage and analyze large volumes of network data. If so, you aren’t alone – many organizations face significant challenges when it comes to effectively managing the collection and storage of their network … [Read more...] about Introducing the Cisco Secure Network Analytics Data Store!