Cost optimization has been one of the hottest topics in observability (and beyond!) lately. Everyone is striving to be efficient, spend money wisely, and get the most out of every dollar invested. At Logz.io, we recently embarked on a very interesting and fruitful data volume optimization journey, reducing our own internal log volume by a whopping 50%. In this article, I’ll … [Read more...] about How Logz.io Reduced Internal Logs Volume by 50% Using Data Optimization Hub
data
ChatGPT is Back in Italy After Addressing Data Privacy Concerns
Apr 29, 2023Ravie LakshmananData Safety / Privacy / AI OpenAI, the company behind ChatGPT, has officially made a return to Italy after the company met the data protection authority's demands ahead of April 30, 2023, deadline. The development was first reported by the Associated Press. OpenAI's CEO, Sam Altman, tweeted, "we're excited ChatGPT is available in [Italy] … [Read more...] about ChatGPT is Back in Italy After Addressing Data Privacy Concerns
ChatGPT and Elasticsearch: OpenAI meets private data
In recent months, there has been a surge of excitement around ChatGPT, a groundbreaking AI model created by OpenAI. But what exactly is ChatGPT? Based on the powerful GPT architecture, ChatGPT is designed to understand and generate human-like responses to text inputs. GPT stands for "Generative Pre-trained Transformer.” The Transformer is a cutting-edge model architecture that … [Read more...] about ChatGPT and Elasticsearch: OpenAI meets private data
Vice Society Ransomware Using Stealthy PowerShell Tool for Data Exfiltration
Apr 17, 2023Ravie LakshmananRansomware / Cyber Attack Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool to fly under the radar and automate the process of exfiltrating data from compromised networks. "Threat actors (TAs) using built-in data exfiltration methods like [living off the land binaries and … [Read more...] about Vice Society Ransomware Using Stealthy PowerShell Tool for Data Exfiltration
Insights into chess game trends: A detailed look at Lichess data
The two other options would be to use a runtime field, dissect the data away, and store a field timecontrol_base and timecontrol_increment with the information. Don’t forget to set the type long.Timecontrol_base:String custom=dissect('%{custom}+%{}').extract($('timecontrol', ''))?.custom;if (custom != null) { emit(Long.parseLong(custom));}Timecontrol_increment:String … [Read more...] about Insights into chess game trends: A detailed look at Lichess data
Shein’s Android App Caught Transmitting Clipboard Data to Remote Servers
Mar 07, 2023Ravie LakshmananPrivacy / Data Breach An older version of Shein's Android application suffered from a bug that periodically captured and transmitted clipboard contents to a remote server. The Microsoft 365 Defender Research Team said it discovered the problem in version 7.9.2 of the app that was released on December 16, 2021. The issue has since been addressed as … [Read more...] about Shein’s Android App Caught Transmitting Clipboard Data to Remote Servers
How to Ingest Data into Falcon LogScale Using Python
This post covers how to ingest data into CrowdStrike Falcon® LogScale from your MacOS platform using Python. This guide is great for setting up a one-node proof of concept (POC) so you can take advantage of LogScale’s free trial. Before you can write your ingest client, you must prepare a good foundation. That means preparing your MacOS instance via the following … [Read more...] about How to Ingest Data into Falcon LogScale Using Python
What the public sector can learn from CDM’s data strategy
The US government handles massive quantities of data — via separate agencies and disconnected data systems. Having a central dashboard to track this data is absolutely essential for uncovering and sharing cybersecurity vulnerabilities before they can do harm to citizens or critical infrastructure.This dashboard — known as the Continuous Diagnostics and Mitigation (CDM) … [Read more...] about What the public sector can learn from CDM’s data strategy
Dutch Police Arrest 3 Hackers Involved in Massive Data Theft and Extortion Scheme
Feb 27, 2023Ravie Lakshmanan The Dutch police announced the arrest of three individuals in connection with a "large-scale" criminal operation involving data theft, extortion, and money laundering. The suspects include two 21-year-old men from Zandvoort and Rotterdam and an 18-year-old man without a permanent residence. The arrests were made on January 23, 2023. It's estimated … [Read more...] about Dutch Police Arrest 3 Hackers Involved in Massive Data Theft and Extortion Scheme
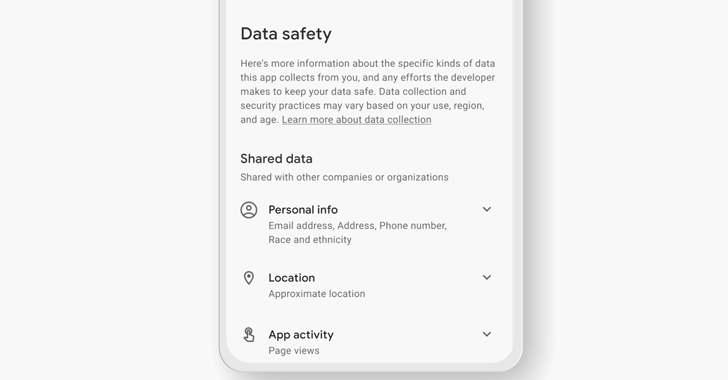
Even Top-Ranked Android Apps in Google Play Store Provide Misleading Data Safety Labels
Feb 24, 2023Ravie LakshmananPrivacy / Data Safety An investigation into data safety labels for Android apps available on the Google Play Store has uncovered "serious loopholes" that allow apps to provide misleading or outright false information. The study, conducted by the Mozilla Foundation as part of its *Privacy Not Included initiative, compared the privacy policies and … [Read more...] about Even Top-Ranked Android Apps in Google Play Store Provide Misleading Data Safety Labels