Microsoft Entra ID Primary Refresh Tokens (PRTs) are an attractive target for threat actors because they are long-lived, they are broadly scoped and they often don’t have additional multifactor authentication requirements after they are obtained. In this blog, we will discuss what PRTs are, how they are issued and how recently released research gives threat attackers a new way … [Read more...] about Detecting Microsoft Entra ID Primary Refresh Token Abuse with Next-Gen SIEM
detecting
Detecting Lateral Movement activity: A new Kibana integration
Cyber attacks are becoming more frequent, targeted, and complex. When it comes to sophisticated attacks, one of the most commonly seen tactics is Lateral Movement. During lateral movement, many attackers try impersonating a legitimate user by abusing admin tools (e.g., SMB, SAMBA, FTP, WMI, WinRM, and PowerShell Remoting) to move laterally from system to system in search of … [Read more...] about Detecting Lateral Movement activity: A new Kibana integration
Detecting NTLM Relay Attacks with CrowdStrike Identity Protection
Adversaries often exploit legacy protocols like Windows NTLM that unfortunately remain widely deployed despite known vulnerabilities. Previous CrowdStrike blog posts have covered critical vulnerabilities in NTLM that allow remote code execution and other NTLM attacks where attackers could exploit vulnerabilities to bypass MIC (Message Integrity Code) protection, session signing … [Read more...] about Detecting NTLM Relay Attacks with CrowdStrike Identity Protection
Detecting Targeted Attacks on Public Cloud Services with Cisco Secure Cloud Analytics
The Public Cloud and Security Responsibility Across many businesses, leveraging services offered and hosted by public cloud providers such as AWS proves to be extremely advantageous for both improving operational efficiencies, cost savings, scaling, and for security. For AWS customers, Lambda functions are a great example of this advantage in providing a useful way to execute … [Read more...] about Detecting Targeted Attacks on Public Cloud Services with Cisco Secure Cloud Analytics
Detecting Vishing Intrusions at a Retail Company
The CrowdStrike Falcon OverWatch™ 2021 Threat Hunting Report details the interactive intrusion activity observed by hunters from July 2020 to June 2021. While the report brings to light some of the new and innovative ways threat actors are gaining access into victim organization’s networks, social engineering remains a tried and true method of gaining access to victim … [Read more...] about Detecting Vishing Intrusions at a Retail Company
Detecting Evasive Malware on IoT Devices Using Electromagnetic Emanations
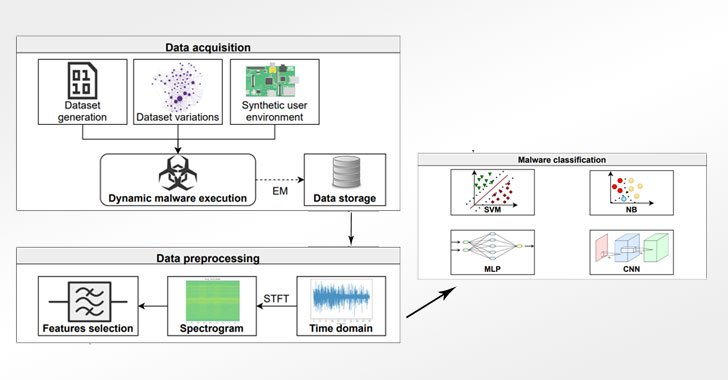
Cybersecurity researchers have proposed a novel approach that leverages electromagnetic field emanations from the Internet of Things (IoT) devices as a side-channel to glean precise knowledge about the different kinds of malware targeting the embedded systems, even in scenarios where obfuscation techniques have been applied to hinder analysis. With the rapid adoption of IoT … [Read more...] about Detecting Evasive Malware on IoT Devices Using Electromagnetic Emanations
Detecting and Responding to SolarWinds Infrastructure Attack with Cisco Secure Analytics
On December 8, FireEye reported that it had been compromised in a sophisticated supply chain attack: more specifically through the SolarWinds Orion IT monitoring and management software. The attackers leveraged business software updates in order to distribute a malware named SUNBURST, and then used this foothold in the organization to contact their Command & Control … [Read more...] about Detecting and Responding to SolarWinds Infrastructure Attack with Cisco Secure Analytics
The Importance of the Network in Detecting Incidents in Critical Infrastructure
As we saw in my last blog, the network plays a key role in defending critical infrastructure and IoT. The devices that we are connecting drive our business, enabling us to make smarter decisions and gain greater efficiency through digitization. But how do we ensure those connected devices are acting as intended? From an industrial operations perspective, we need to know that … [Read more...] about The Importance of the Network in Detecting Incidents in Critical Infrastructure