In part one of this series we introduced the notion of risk-based extended detection with SecureX – the idea that a user can prioritise detections into incidents based on their idea of what constitutes risk in their environments and then extend those detections with enrichments from other products. In subsequent posts we are diving deeper into different Cisco Secure detection … [Read more...] about Relevant and Extended Detection with SecureX, Part Two: Endpoint Detections
detection
Relevant and Extended Detection with SecureX
In a recent blog, Al Huger spoke about Cisco’s vision of Extended Detection and Response (XDR); specifically covering the breadth of definitions in the industry and clarifying Cisco’s definition of XDR: “A unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.” He also detailed the … [Read more...] about Relevant and Extended Detection with SecureX
How CrowdStrike Supercharges IR with Identity Threat Detection
CrowdStrike Incident Response teams leverage Falcon Identity Threat Detection (ITD) for Microsoft Active Directory (AD) and Azure AD account authentication visibility, credential hygiene and multifactor authentication implementation Falcon ITD is integrated into the CrowdStrike Falcon® platform and provides alerts, dashboards and custom templates to identify compromised … [Read more...] about How CrowdStrike Supercharges IR with Identity Threat Detection
Why the Detection Funnel Hits Diminishing Returns
Noisy alerts caused by an increased number of rules for detecting malicious behavior overburden security analysts. Alert fatigue happens when an overwhelming number of alerts desensitize the security team tasked with responding to them. CrowdStrike CrowdScore™ automatically prioritizes activity that is more unusual in part by noticing which alerts are noisy in each … [Read more...] about Why the Detection Funnel Hits Diminishing Returns
New Malware Targets Windows Subsystem for Linux to Evade Detection
A number of malicious samples have been created for the Windows Subsystem for Linux (WSL) with the goal of compromising Windows machines, highlighting a sneaky method that allows the operators to stay under the radar and thwart detection by popular anti-malware engines. The "distinct tradecraft" marks the first instance where a threat actor has been found abusing WSL to install … [Read more...] about New Malware Targets Windows Subsystem for Linux to Evade Detection
This New Malware Family Using CLFS Log Files to Avoid Detection
Cybersecurity researchers have disclosed details about a new malware family that relies on the Common Log File System (CLFS) to hide a second-stage payload in registry transaction files in an attempt to evade detection mechanisms. FireEye's Mandiant Advanced Practices team, which made the discovery, dubbed the malware PRIVATELOG, and its installer, STASHLOG. Specifics about the … [Read more...] about This New Malware Family Using CLFS Log Files to Avoid Detection
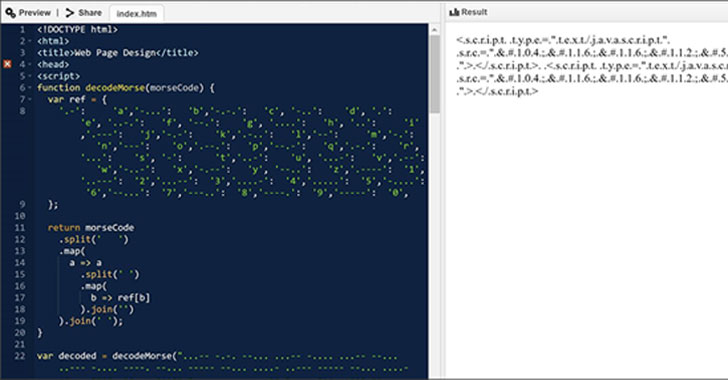
Hackers Spotted Using Morse Code in Phishing Attacks to Evade Detection
Microsoft has disclosed details of an evasive year-long social engineering campaign wherein the operators kept changing their obfuscation and encryption mechanisms every 37 days on average, including relying on Morse code, in an attempt to cover their tracks and surreptitiously harvest user credentials. The phishing attacks take the form of invoice-themed lures mimicking … [Read more...] about Hackers Spotted Using Morse Code in Phishing Attacks to Evade Detection
Extending Detection into Automated Response with SecureX and Secure Cloud Analytics
Networks span across the enterprise, campus, branch, and into the cloud. Resources that enable agile operational models to allow the business to anticipate and respond to change are expanding the attack surface and bring with them more complexity. Complexity that attackers are taking advantage of. Meanwhile an ever-increasing amount of sensitive and legally protected data is … [Read more...] about Extending Detection into Automated Response with SecureX and Secure Cloud Analytics
Simplified Security with Purpose-Built Networking for Advanced Threat Detection
Have you ever looked at your switch and wondered what is going on inside there? It hums, at times it buzzes, and it has a few blinky lights, but what is it really doing? Are you able to understand what types of traffic are being sent to and fro? And do you ever wonder if any threats are lurking within? Of course you have; we all know that threats are everywhere and can be … [Read more...] about Simplified Security with Purpose-Built Networking for Advanced Threat Detection
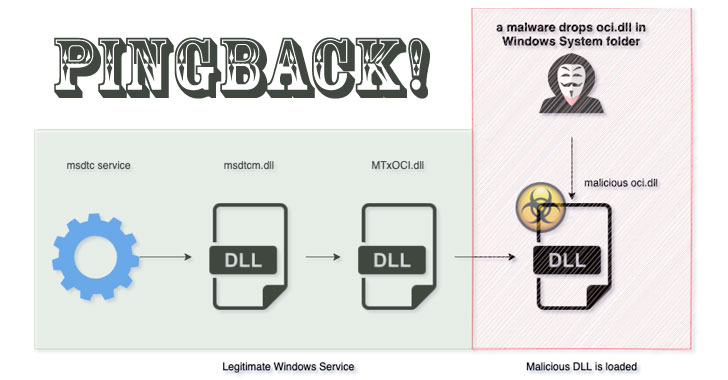
New Pingback Malware Using ICMP Tunneling to Evade C&C Detection
Researchers on Tuesday disclosed a novel malware that uses a variety of tricks to stay under the radar and evade detection, while stealthily capable of executing arbitrary commands on infected systems. Called 'Pingback,' the Windows malware leverages Internet Control Message Protocol (ICMP) tunneling for covert bot communications, allowing the adversary to utilize ICMP packets … [Read more...] about New Pingback Malware Using ICMP Tunneling to Evade C&C Detection