Feb 07, 2025Ravie LakshmananMobile Security / Artificial Intelligence A new audit of DeepSeek's mobile app for the Apple iOS operating system has found glaring security issues, the foremost being that it sends sensitive data over the internet sans any encryption, exposing it to interception and manipulation attacks. The assessment comes from NowSecure, which also found that … [Read more...] about DeepSeek App Transmits Sensitive User and Device Data Without Encryption
device
How One Vulnerable Device Can Spell Disaster
Dec 20, 2023NewsroomNetwork Security / Data Breach Ransomware groups are increasingly switching to remote encryption in their attacks, marking a new escalation in tactics adopted by financially motivated actors to ensure the success of their campaigns. "Companies can have thousands of computers connected to their network, and with remote ransomware, all it takes is one … [Read more...] about How One Vulnerable Device Can Spell Disaster
Smart device vulnerabilities and securing against them
Intelligent features and internet connectivity are built into most television sets, baby monitors, and many other digital devices these days. Regardless of whether you use these smart features or not, smart devices produce security risks that you should know about and take steps to protect yourself against, while if you’re using plenty of the features of your smart home, … [Read more...] about Smart device vulnerabilities and securing against them
Boosting your XDR Potential with Device Insights and Kenna Integrations
It’s a busy month for cybersecurity, with the return of in-person RSAC in San Francisco, followed by Cisco Live in very lively Las Vegas! With so much happening, and so many announcements from every security vendor out there, it can be hard to keep track of everything going on. Let us help give you the highlights from a Cisco SecureX perspective! We have been busy this past … [Read more...] about Boosting your XDR Potential with Device Insights and Kenna Integrations
New in SecureX: Device Insights
Since its release, Cisco SecureX has helped over 10,000 customers gain better visibility into their infrastructure. As the number of devices in many customer environments continues to increase, so does the number of products with information about those devices. Between mobile device managers (MDM), posture agents, and other security products, a wealth of data is being … [Read more...] about New in SecureX: Device Insights
Hackers Using Device Registration Trick to Attack Enterprises with Lateral Phishing
Microsoft has disclosed details of a large-scale, multi-phase phishing campaign that uses stolen credentials to register devices on a victim's network to further propagate spam emails and widen the infection pool. The tech giant said the attacks manifested through accounts that were not secured using multi-factor authentication (MFA), thereby making it possible for the … [Read more...] about Hackers Using Device Registration Trick to Attack Enterprises with Lateral Phishing
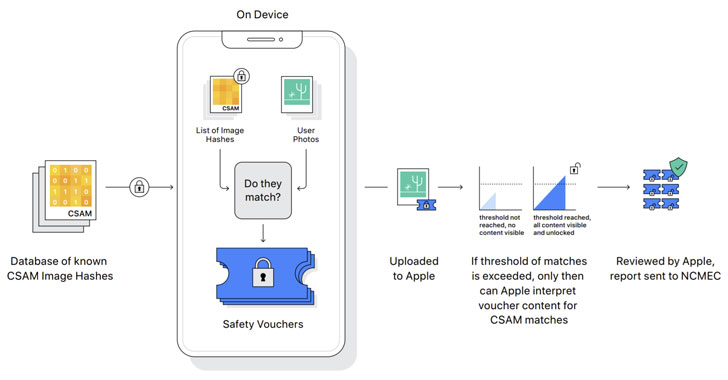
Apple to Scan Every Device for Child Abuse Content — But Experts Fear for Privacy
Apple on Thursday said it's introducing new child safety features in iOS, iPadOS, watchOS, and macOS as part of its efforts to limit the spread of Child Sexual Abuse Material (CSAM) in the U.S. To that effect, the iPhone maker said it intends to begin client-side scanning of images shared via every Apple device for known child abuse content as they are being uploaded into … [Read more...] about Apple to Scan Every Device for Child Abuse Content — But Experts Fear for Privacy
TV remote hacked, turned into listening device
There’s a certain reliability to everyday objects. Take a TV remote for example: It’s hard to imagine one eavesdropping on conversations, but cybersecurity researchers J. J. Lehman and Ofri Ziv from Israeli company Guardicore got one to do just that. They reported their findings at RSA Conference 2021. How researchers hacked a remote The subject of Lehman and Ziv’s research was … [Read more...] about TV remote hacked, turned into listening device
Introducing Device Insights for Cisco SecureX
Cisco SecureX: Year 2 It’s hard to believe it’s been nearly a year since we announced the Cisco SecureX platform at RSA 2020! We set out with the goal to streamline our customers’ operations with increased visibility across their security portfolio, provide out-of-the-box integrations, powerful security analytics, and automated workflows to speed threat detection and … [Read more...] about Introducing Device Insights for Cisco SecureX
Missing Link in a ‘Zero Trust’ Security Model—The Device You’re Connecting With!
Like it or not, 2020 was the year that proved that teams could work from literally anywhere. While terms like "flex work" and "WFH" were thrown around before COVID-19 came around, thanks to the pandemic, remote working has become the defacto way people work nowadays. Today, digital-based work interactions take the place of in-person ones with near-seamless fluidity, and the … [Read more...] about Missing Link in a ‘Zero Trust’ Security Model—The Device You’re Connecting With!