Continuous Threat Exposure Management (CTEM) is a strategic framework that helps organizations continuously assess and manage cyber risk. It breaks down the complex task of managing security threats into five distinct stages: Scoping, Discovery, Prioritization, Validation, and Mobilization. Each of these stages plays a crucial role in identifying, addressing, and mitigating … [Read more...] about How to Get Going with CTEM When You Don’t Know Where to Start
Dont
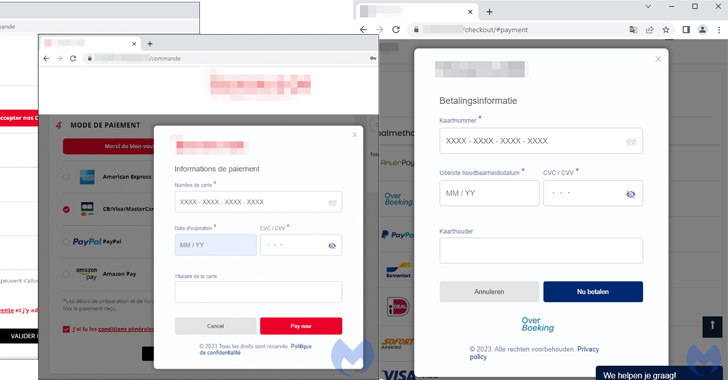
Don’t Be Fooled by Their Sleek, Modern Looks — It’s Magecart!
Apr 28, 2023Ravie LakshmananOnline Security / Website Hacking An ongoing Magecart campaign has attracted the attention of cybersecurity researchers for leveraging realistic-looking fake payment screens to capture sensitive data entered by unsuspecting users. "The threat actor used original logos from the compromised store and customized a web element known as a modal to … [Read more...] about Don’t Be Fooled by Their Sleek, Modern Looks — It’s Magecart!
REPEAT AND REFINE: HOW DO YOU GET TO CARNEGIE HALL? (Pt. 6 of “Why Don’t You Go Dox Yourself?”)
Welcome back! In our last article, you cleared out your extraneous digital footprints by removing unnecessary accounts and opting-out of data broker services, and have finished a dedicated review of your online history. In this final section, we will answer the natural question encountered at the end of any journey: What’s next? Before becoming the series you’ve just read, I … [Read more...] about REPEAT AND REFINE: HOW DO YOU GET TO CARNEGIE HALL? (Pt. 6 of “Why Don’t You Go Dox Yourself?”)
CLEANING UP THE CLUTTER (Pt. 5 of “Why Don’t You Go Dox Yourself?”)
Welcome back! Previously in our Go Dox Yourself series, we walked through reviewing what information is available about you online, prioritizing those accounts that are most important or still active, and then restricting how much we share through those accounts and who gets to see it. That’s two out of our three steps — maybe good enough for Meatloaf, but not for us! You’re in … [Read more...] about CLEANING UP THE CLUTTER (Pt. 5 of “Why Don’t You Go Dox Yourself?”)
LOCKING THE BACK DOOR (Pt. 4 of “Why Don’t You Go Dox Yourself?”)
With passwords and MFA out of the way, let’s next look at connected apps or services that are tied to our priority accounts. When you log into other sites on the web through Facebook, Google, or another social account, as well as when you install social media apps or games, you are sharing information about those accounts with those services. This may be as limited as the email … [Read more...] about LOCKING THE BACK DOOR (Pt. 4 of “Why Don’t You Go Dox Yourself?”)
RESTRICT: LOCKING THE FRONT DOOR (Pt. 3 of “Why Don’t You Go Dox Yourself?”)
In the first step of your doxxing research, we collected a list of our online footprint, digging out the most important accounts that you want to protect and obsolete or forgotten accounts you no longer use. Because the most recent and relevant data is likely to live in the accounts you use regularly, our next step will be to review the full scope of what’s visible from these … [Read more...] about RESTRICT: LOCKING THE FRONT DOOR (Pt. 3 of “Why Don’t You Go Dox Yourself?”)
COLLECTING OUR BREADCRUMBS (Pt. 2 of “Why Don’t You Go Dox Yourself?”)
Sharing is caring… but on the internet, sharing can also be tricky! When we post something, we have to look at the forest and not just the trees. Doxxers usually start with one or two pieces of relatively innocent or public information, but by connecting the dots between those pieces they can build a frighteningly detailed picture of an individual. Seemingly innocuous details … [Read more...] about COLLECTING OUR BREADCRUMBS (Pt. 2 of “Why Don’t You Go Dox Yourself?”)
Why Don’t You Go Dox Yourself?
Whether or not you’ve heard the term “doxxing” before, you’re probably familiar with the problem it names: collecting personal information about someone online to track down and reveal their real-life identity. The motivations for doxxing are many, and mostly malicious: for some doxxers, the goal in tracking someone is identity theft. For others, it’s part of a pattern of … [Read more...] about Why Don’t You Go Dox Yourself?
Don’t Use Public Wi-Fi Without DNS Filtering
Providing public Wi-Fi is a great service to offer your customers as it becomes more and more standard in today's society. I like the fact that I do not have to worry about accessing the Internet while I am away, or spending a lot of money on an international connection, or just staying offline while I am away. With public Wi-Fi, modern life has become a constant connection to … [Read more...] about Don’t Use Public Wi-Fi Without DNS Filtering
What are you missing when you don’t enable global threat alerts?
Network telemetry is a reservoir of data that, if tapped, can shed light on users’ behavioral patterns, weak spots in security, potentially malicious tools installed in enterprise environments, and even malware itself. Global threat alerts (formerly Cognitive Threat Analytics known as CTA) is great at taking an enterprise’s network telemetry and running it through a pipeline of … [Read more...] about What are you missing when you don’t enable global threat alerts?