Dec 09, 2024Ravie LakshmananThreat Intelligence / Malware The threat actors linked to the Black Basta ransomware have been observed switching up their social engineering tactics, distributing a different set of payloads such as Zbot and DarkGate since early October 2024. "Users within the target environment will be email bombed by the threat actor, which is often achieved by … [Read more...] about Black Basta Ransomware Evolves with Email Bombing, QR Codes, and Social Engineering
What to do if you receive a sextortion email
Sextortion — a portmanteau of “sex” and “extortion” — originally referred to blackmail using compromising photos or videos obtained either by hacking a victim’s device or voluntarily from the victim themselves. While this form of crime still exists, today’s sextortioners are far less likely to be in the possession of any juicy material. Some varieties of sextortion work even … [Read more...] about What to do if you receive a sextortion email
Harnessing Email Data to Stop Phishing Attacks with Falcon Next-Gen SIEM
Phishing is a formidable–and financially devastating–threat costing organizations $4.76 million USD per breach on average. With a simple, deceptive email, adversaries can masquerade as trusted entities, tricking even savvy individuals into handing over their credentials and other sensitive information. Whether it’s a duplicitous link or a crafty call to action, phishing … [Read more...] about Harnessing Email Data to Stop Phishing Attacks with Falcon Next-Gen SIEM
Email Security Reinvented: How AI is Revolutionizing Digital Defense
Do you remember when attackers were sending the same email to everyone? Those days are long gone! Attacks are now more targeted, creative, and leverage reputable cloud applications to initiate malicious attacks that evade reputation detection engines. The use of Machine Learning and Deep Learning models allows us to understand the intention of the message, who is sending it, … [Read more...] about Email Security Reinvented: How AI is Revolutionizing Digital Defense
Mitigate Cyber Risk From Email With the Falcon LogScale and Mimecast Integration
Email is the top initial attack vector, with phishing campaigns responsible for many damaging cyber attacks, including ransomware. Being able to search Mimecast email security logs in CrowdStrike Falcon® LogScale (formerly known as Humio), alongside other log sources such as endpoint, network and authentication data helps cybersecurity teams detect and respond to cyber … [Read more...] about Mitigate Cyber Risk From Email With the Falcon LogScale and Mimecast Integration
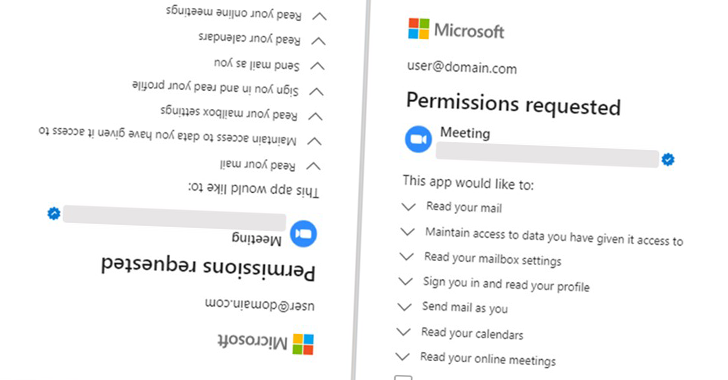
Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
Feb 01, 2023Ravie LakshmananEnterprise Security / Authentication Microsoft on Tuesday said it took steps to disable fake Microsoft Partner Network (MPN) accounts that were used for creating malicious OAuth applications as part of a malicious campaign designed to breach organizations' cloud environments and steal email. "The applications created by these fraudulent actors were … [Read more...] about Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
Understanding Business Email Compromise to better protect against it
What is business email compromise? Imagine this: Your CEO sends you an email asking for your help transferring $5,000 to a new vendor for an urgent project. You make the transfer, only to find out later that the email was actually from an imposter, and that money is now in the hands of cybercriminals. Oops, right? crickets Business Email Compromise (BEC) is a type of cybercrime … [Read more...] about Understanding Business Email Compromise to better protect against it
Secure Email Threat Defense: Providing critical insight into business risk
Attackers specifically craft business email compromise (BEC) and phishing emails using a combination of malicious techniques, expertly selected from an ever-evolving bag of tricks. They’ll use these techniques to impersonate a person or business that’s well-known to the targeted recipient and hide their true intentions, while attempting to avoid detection by security … [Read more...] about Secure Email Threat Defense: Providing critical insight into business risk
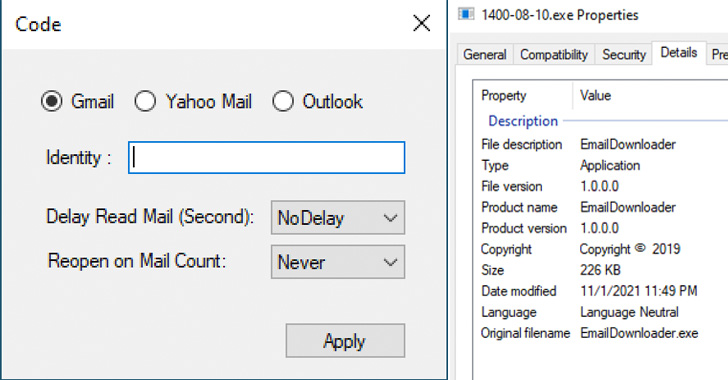
Google Uncovers Tool Used by Iranian Hackers to Steal Data from Email Accounts
The Iranian government-backed actor known as Charming Kitten has added a new tool to its malware arsenal that allows it to retrieve user data from Gmail, Yahoo!, and Microsoft Outlook accounts. Dubbed HYPERSCRAPE by Google Threat Analysis Group (TAG), the actively in-development malicious software is said to have been used against less than two dozen accounts in Iran, with the … [Read more...] about Google Uncovers Tool Used by Iranian Hackers to Steal Data from Email Accounts
New Zimbra Email Vulnerability Could Let Attackers Steal Your Login Credentials
A new high-severity vulnerability has been disclosed in the Zimbra email suite that, if successfully exploited, enables an unauthenticated attacker to steal cleartext passwords of users sans any user interaction. "With the consequent access to the victims' mailboxes, attackers can potentially escalate their access to targeted organizations and gain access to various internal … [Read more...] about New Zimbra Email Vulnerability Could Let Attackers Steal Your Login Credentials