No one can deny the convenience of cloud file-storage services like Dropbox or OneDrive. The one drawback is that cybercriminals, intelligence agencies, or the hosting provider itself can view your cloud-based files without authorization. But there’s a more secure alternative: encrypted cloud file-storage. Some call it end-to-end encryption (E2EE) — similar to Signal and … [Read more...] about Which encrypted file storage to choose?
encrypted
Facebook Introduces New Features for End-to-End Encrypted Messenger App
Jan 24, 2023Ravie LakshmananEncryption / Privacy Meta Platforms on Monday announced that it has started to expand global testing of end-to-end encryption (E2EE) in Messenger chats by default. "Over the next few months, more people will continue to see some of their chats gradually being upgraded with an extra layer of protection provided by end-to-end encryption," Meta's … [Read more...] about Facebook Introduces New Features for End-to-End Encrypted Messenger App
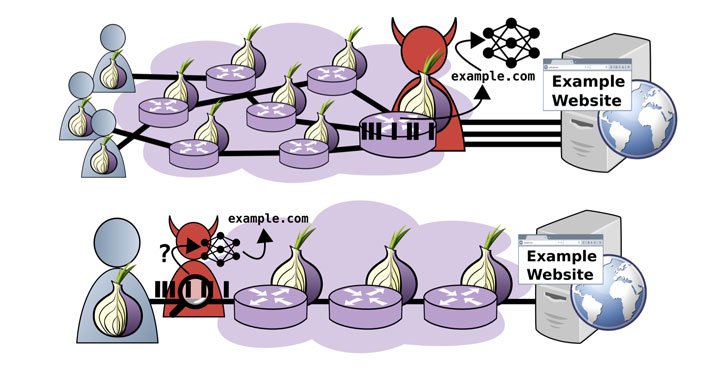
Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
A new analysis of website fingerprinting (WF) attacks aimed at the Tor web browser has revealed that it's possible for an adversary to glean a website frequented by a victim, but only in scenarios where the threat actor is interested in a specific subset of the websites visited by users. "While attacks can exceed 95% accuracy when monitoring a small set of five popular … [Read more...] about Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
How to decrypt files encrypted by Fonix
When the Fonix ransomware group suddenly announced the end of its activities and published a master key for decoding encrypted files, our experts immediately updated the Rakhni Decryptor tool to automate the process. You can download the tool right here. The Fonix example illustrates yet again why even if you don’t plan to pay the ransom (a smart choice), you should hold on to … [Read more...] about How to decrypt files encrypted by Fonix
Police Arrested Hundreds of Criminals After Hacking Into Encrypted Chat Network
In a joint operation, European and British law enforcement agencies recently arrested hundreds of alleged drug dealers and other criminals after infiltrating into a global network of an encrypted chatting app that was used to plot drug deals, money laundering, extortions, and even murders.Dubbed EncroChat, the top-secret encrypted communication app comes pre-installed on a … [Read more...] about Police Arrested Hundreds of Criminals After Hacking Into Encrypted Chat Network
How to recover files encrypted by Yatron and FortuneCrypt
Ransomware has been and remains a big headache for both users and experts alike. It is not a simple task to recover files encrypted by ransomware, and in many cases it’s impossible. But we have good news for the victims of Yatron and FortuneCrypt malware: Kaspersky experts have developed and published decryptors for the files this particular malware encrypts. How to decrypt … [Read more...] about How to recover files encrypted by Yatron and FortuneCrypt
Threats in encrypted traffic – Cisco Blog
There was a time when the web was open. Quite literally—communications taking place on the early web were not masked in any significant fashion. This meant that it was fairly trivial for a bad actor to intercept and read the data being transmitted between networked devices. This was especially troublesome when it came to sensitive data, such as password authentication or credit … [Read more...] about Threats in encrypted traffic – Cisco Blog
New Bluetooth Vulnerability Lets Attackers Spy On Encrypted Connections
Over a billion Bluetooth-enabled devices, including smartphones, laptops, smart IoT devices, and industrial devices, have been found vulnerable to a high severity vulnerability that could allow attackers to spy on data transmitted between the two devices.The vulnerability, assigned as CVE-2019-9506, resides in the way 'encryption key negotiation protocol' lets two Bluetooth … [Read more...] about New Bluetooth Vulnerability Lets Attackers Spy On Encrypted Connections