A late-stage candidate encryption algorithm that was meant to withstand decryption by powerful quantum computers in the future has been trivially cracked by using a computer running Intel Xeon CPU in an hour's time. The algorithm in question is SIKE — short for Supersingular Isogeny Key Encapsulation — which made it to the fourth round of the Post-Quantum Cryptography (PQC) … [Read more...] about Single-Core CPU Cracked Post-Quantum Encryption Candidate Algorithm in Just an Hour
encryption
Researchers Uncover Ways to Break the Encryption of ‘MEGA’ Cloud Storage Service
A new piece of research from academics at ETH Zurich has identified a number of critical security issues in the MEGA cloud storage service that could be leveraged to break the confidentiality and integrity of user data. In a paper titled "MEGA: Malleable Encryption Goes Awry," the researchers point out how MEGA's system does not protect its users against a malicious server, … [Read more...] about Researchers Uncover Ways to Break the Encryption of ‘MEGA’ Cloud Storage Service
Researchers Demonstrate New Side-Channel Attack on Homomorphic Encryption
A group of academics from the North Carolina State University and Dokuz Eylul University have demonstrated what they say is the "first side-channel attack" on homomorphic encryption that could be exploited to leak data as the encryption process is underway. "Basically, by monitoring power consumption in a device that is encoding data for homomorphic encryption, we are able to … [Read more...] about Researchers Demonstrate New Side-Channel Attack on Homomorphic Encryption
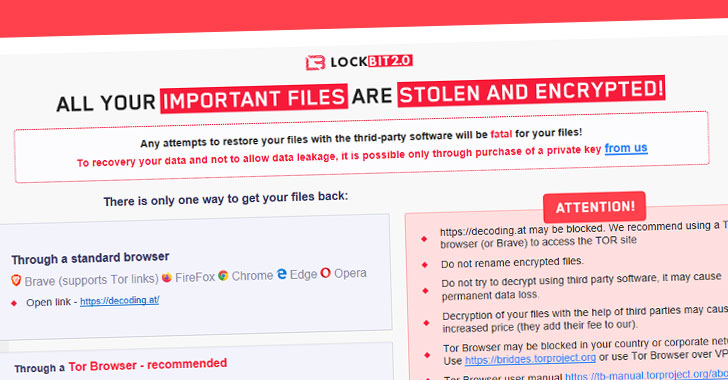
Master Key for Hive Ransomware Retrieved Using a Flaw in its Encryption Algorithm
Researchers have detailed what they call the "first successful attempt" at decrypting data infected with Hive ransomware without relying on the private key used to lock access to the content. "We were able to recover the master key for generating the file encryption key without the attacker's private key, by using a cryptographic vulnerability identified through analysis," a … [Read more...] about Master Key for Hive Ransomware Retrieved Using a Flaw in its Encryption Algorithm
Patching the CentOS 8 Encryption Bug is Urgent – What Are Your Plans?
There are three things you can be sure of in life: death, taxes – and new CVEs. For organizations that rely on CentOS 8, the inevitable has now happened, and it didn't take long. Just two weeks after reaching the official end of life, something broke spectacularly, leaving CentOS 8 users at major risk of a severe attack – and with no support from CentOS. You'd think that this … [Read more...] about Patching the CentOS 8 Encryption Bug is Urgent – What Are Your Plans?
LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "intermittent encryption." Called LockFile, the operators of the ransomware has been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware … [Read more...] about LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
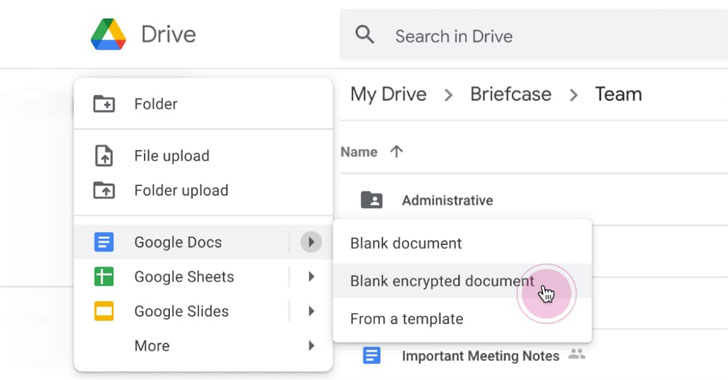
Google Workspace Now Offers Client-side Encryption For Drive and Docs
Google on Monday announced that it's rolling out client-side encryption to Google Workspace (formerly G Suite), thereby giving its enterprise customers direct control of encryption keys and the identity service they choose to access those keys. "With client-side encryption, customer data is indecipherable to Google, while users can continue to take advantage of Google's native … [Read more...] about Google Workspace Now Offers Client-side Encryption For Drive and Docs
Future Focused: Encryption and Visibility Can Co-Exist
Privacy and security are in constant tension. Hiding internet activity strengthens privacy—but also makes it easier for bad actors to infiltrate the network. In fact, 63% of threats detected by Cisco Stealthwatch in 2019 were in encrypted traffic. The European Union is concerned enough that it drafted a resolution in November 2020 to ban end-to-end encryption, prompting outcry … [Read more...] about Future Focused: Encryption and Visibility Can Co-Exist
Network Security Efficacy in the Age of Pervasive TLS Encryption
A Reality Check on Firewall Visibility One question which I love to ask next-generation firewall (NGFW) and intrusion prevention system (IPS) administrators is whether they have seen a gradual decline in their deployments’ security efficacy over the last few years. Most answer this question with a resounding “yes,” and then wonder how I knew. With over 90% of Internet traffic … [Read more...] about Network Security Efficacy in the Age of Pervasive TLS Encryption
New Raccoon Attack Could Let Attackers Break SSL/TLS Encryption
A group of researchers has detailed a new timing vulnerability in Transport Layer Security (TLS) protocol that could potentially allow an attacker to break the encryption and read sensitive communication under specific conditions.Dubbed "Raccoon Attack," the server-side attack exploits a side-channel in the cryptographic protocol (versions 1.2 and lower) to extract the shared … [Read more...] about New Raccoon Attack Could Let Attackers Break SSL/TLS Encryption