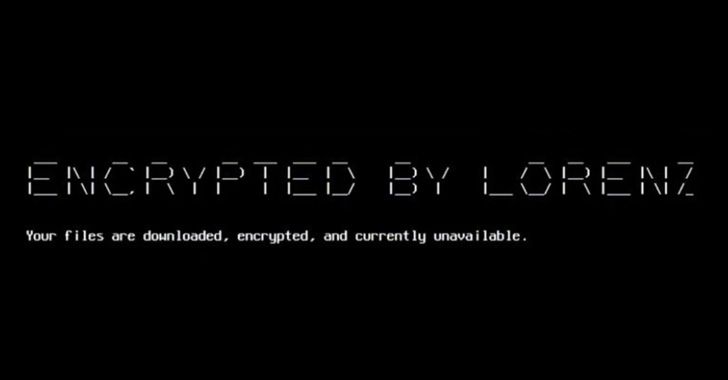
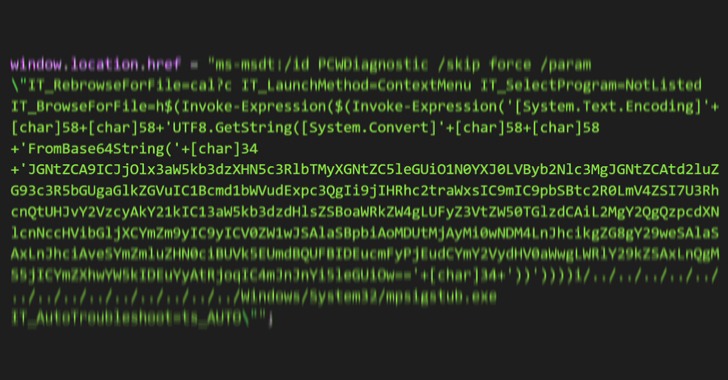
The operators behind the Lornenz ransomware operation have been observed exploiting a now-patched critical security flaw in Mitel MiVoice Connect to obtain a foothold into target environments for follow-on malicious activities. "Initial malicious activity originated from a Mitel appliance sitting on the network perimeter," researchers from cybersecurity firm Arctic Wolf said in … [Read more...] about Lorenz Ransomware Exploit Mitel VoIP Systems to Breach Business Networks
exploit
Hackers Exploit Twitter Vulnerability to Exposes 5.4 Million Accounts
Twitter on Friday revealed that a now-patched zero-day bug was used to link phone numbers and emails to user accounts on the social media platform. "As a result of the vulnerability, if someone submitted an email address or phone number to Twitter's systems, Twitter's systems would tell the person what Twitter account the submitted email addresses or phone number was associated … [Read more...] about Hackers Exploit Twitter Vulnerability to Exposes 5.4 Million Accounts
Hackers Exploit Mitel VoIP Zero-Day in Likely Ransomware Attack
A suspected ransomware intrusion against an unnamed target leveraged a Mitel VoIP appliance as an entry point to achieve remote code execution and gain initial access to the environment. The findings come from cybersecurity firm CrowdStrike, which traced the source of the attack to a Linux-based Mitel VoIP device sitting on the network perimeter, while also identifying a … [Read more...] about Hackers Exploit Mitel VoIP Zero-Day in Likely Ransomware Attack
Watch Out! Researchers Spot New Microsoft Office Zero-Day Exploit in the Wild
Cybersecurity researchers are calling attention to a zero-day flaw in Microsoft Office that could be abused to achieve arbitrary code execution on affected Windows systems. The vulnerability came to light after an independent cybersecurity research team known as nao_sec uncovered a Word document ("05-2022-0438.doc") that was uploaded to VirusTotal from an IP address in … [Read more...] about Watch Out! Researchers Spot New Microsoft Office Zero-Day Exploit in the Wild
New Exploit Bypasses Existing Spectre-V2 Mitigations in Intel, AMD, Arm CPUs
Researchers have disclosed a new technique that could be used to circumvent existing hardware mitigations in modern processors from Intel, AMD, and Arm, and stage speculative execution attacks such as Spectre to leak sensitive information from host memory. Attacks like Spectre are designed to break the isolation between different applications by taking advantage of an … [Read more...] about New Exploit Bypasses Existing Spectre-V2 Mitigations in Intel, AMD, Arm CPUs
Exploit Research Strengthens Customer Protection
CrowdStrike continuously observes and researches exploit behavior to strengthen protection for customers Code execution techniques constantly target Windows, Linux and macOS operating systems Successful remote/arbitrary code execution can enable a foothold for attackers to continue compromise Understanding and detecting post-exploit activity is imperative for keeping … [Read more...] about Exploit Research Strengthens Customer Protection
How Exploit Intel Makes You Less Vulnerable
New research shows effective and efficient vulnerability management hinges on a key ingredient: exploit intel. The data arrives just in time. An expanding threat landscape In 2021, a record-breaking 20,130 Common Vulnerabilities and Exposures (CVEs) were published in the National Vulnerability Database. CVEs are exploding just as attackers are growing more sophisticated, … [Read more...] about How Exploit Intel Makes You Less Vulnerable
Kubernetes Container Escape Using Linux Kernel Exploit
On Jan. 18, 2022, researchers found a heap base buffer overflow flaw (CVE-2022-0185) in the Linux kernel (5.1-rc1+) function “legacy_parse_param” of filesystem context functionality, which allows an out-of-bounds write in kernel memory. Using this primitive, an unprivileged attacker can escalate its privilege to root, bypassing any Linux namespace restrictions. CVE-2022-0185 … [Read more...] about Kubernetes Container Escape Using Linux Kernel Exploit
Hackers Attempt to Exploit New SolarWinds Serv-U Bug in Log4Shell Attacks
Microsoft on Wednesday disclosed details of a new security vulnerability in SolarWinds Serv-U software that it said was being weaponized by threat actors to propagate attacks leveraging the Log4j flaws to compromise targets. Tracked as CVE-2021-35247 (CVSS score: 5.3), the issue is an "input validation vulnerability that could allow attackers to build a query given some input … [Read more...] about Hackers Attempt to Exploit New SolarWinds Serv-U Bug in Log4Shell Attacks
noPac Exploit: Microsoft AD Flaw May Lead to Total Domain Compromise
What Happened? Microsoft recently published two critical CVEs related to Active Directory (CVE-2021-42278 and CVE-2021-42287), which when combined by a malicious actor could lead to privilege escalation with a direct path to a compromised domain. In mid-December 2021, a public exploit that combined these two Microsoft Active Directory design flaws (referred also as “noPac”) … [Read more...] about noPac Exploit: Microsoft AD Flaw May Lead to Total Domain Compromise