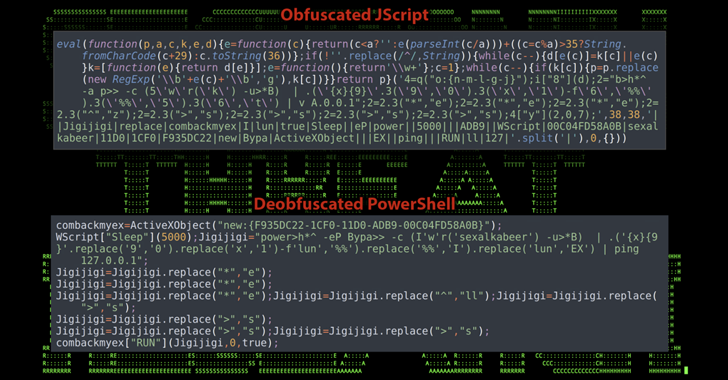
May 17, 2024NewsroomCryptojacking / Malware The cryptojacking group known as Kinsing has demonstrated its ability to continuously evolve and adapt, proving to be a persistent threat by swiftly integrating newly disclosed vulnerabilities to exploit arsenal and expand its botnet. The findings come from cloud security firm Aqua, which described the threat actor as actively … [Read more...] about Kinsing Hacker Group Exploits More Flaws to Expand Botnet for Cryptojacking
exploits
CISA Issues Emergency Directive to Federal Agencies on Ivanti Zero-Day Exploits
Jan 20, 2024NewsroomNetwork Security / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday issued an emergency directive urging Federal Civilian Executive Branch (FCEB) agencies to implement mitigations against two actively exploited zero-day flaws in Ivanti Connect Secure (ICS) and Ivanti Policy Secure (IPS) products. The … [Read more...] about CISA Issues Emergency Directive to Federal Agencies on Ivanti Zero-Day Exploits
Alert: Over 178,000 SonicWall Firewalls Potentially Vulnerable to Exploits
Jan 16, 2024NewsroomVulnerability / Network Security Over 178,000 SonicWall firewalls exposed over the internet are exploitable to at least one of the two security flaws that could be potentially exploited to cause a denial-of-service (DoS) condition and remote code execution (RCE). "The two issues are fundamentally the same but exploitable at different HTTP URI paths due to … [Read more...] about Alert: Over 178,000 SonicWall Firewalls Potentially Vulnerable to Exploits
New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
May 26, 2023Ravie LakshmananICS/SCADA Security A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unearthed. Google-owned threat intelligence firm Mandiant dubbed the malware COSMICENERGY, adding it was uploaded to a public malware scanning utility in December 2021 by a submitter in Russia. There … [Read more...] about New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
XWorm Malware Exploits Follina Vulnerability in New Wave of Attacks
May 12, 2023Ravie LakshmananCyber Threat / Malware Cybersecurity researchers have discovered an ongoing phishing campaign that makes use of a unique attack chain to deliver the XWorm malware on targeted systems. Securonix, which is tracking the activity cluster under the name MEME#4CHAN, said some of the attacks have primarily targeted manufacturing firms and healthcare … [Read more...] about XWorm Malware Exploits Follina Vulnerability in New Wave of Attacks
NSO Group Used 3 Zero-Click iPhone Exploits Against Human Rights Defenders
Israeli spyware maker NSO Group deployed at least three novel "zero-click" exploits against iPhones in 2022 to infiltrate defenses erected by Apple and deploy Pegasus, according to the latest findings from Citizen Lab. "NSO Group customers widely deployed at least three iOS 15 and iOS 16 zero-click exploit chains against civil society targets around the world," the … [Read more...] about NSO Group Used 3 Zero-Click iPhone Exploits Against Human Rights Defenders
Cytrox’s Predator Spyware Targeted Android Users with Zero-Day Exploits
Google's Threat Analysis Group (TAG) on Thursday pointed fingers at a North Macedonian spyware developer named Cytrox for developing exploits against five zero-day (aka 0-day) flaws, four in Chrome and one in Android, to target Android users. "The 0-day exploits were used alongside n-day exploits as the developers took advantage of the time difference between when some critical … [Read more...] about Cytrox’s Predator Spyware Targeted Android Users with Zero-Day Exploits
Google Project Zero Detects a Record Number of Zero-Day Exploits in 2021
Google Project Zero called 2021 a "record year for in-the-wild 0-days," as 58 security vulnerabilities were detected and disclosed during the course of the year. The development marks more than a two-fold jump from the previous maximum when 28 0-day exploits were tracked in 2015. In contrast, only 25 0-day exploits were detected in 2020. "The large uptick in in-the-wild 0-days … [Read more...] about Google Project Zero Detects a Record Number of Zero-Day Exploits in 2021
New “B1txor20” Linux Botnet Uses DNS Tunnel and Exploits Log4J Flaw
A previously undocumented backdoor has been observed targeting Linux systems with the goal of corralling the machines into a botnet and acting as a conduit for downloading and installing rootkits. Qihoo 360's Netlab security team called it B1txor20 "based on its propagation using the file name 'b1t,' the XOR encryption algorithm, and the RC4 algorithm key length of 20 … [Read more...] about New “B1txor20” Linux Botnet Uses DNS Tunnel and Exploits Log4J Flaw
PROPHET SPIDER Exploits Citrix ShareFile
At the start of 2022, CrowdStrike Intelligence and CrowdStrike Services investigated an incident in which PROPHET SPIDER exploited CVE-2021-22941 — a remote code execution (RCE) vulnerability impacting Citrix ShareFile Storage Zones Controller — to compromise a Microsoft Internet Information Services (IIS) web server. The adversary exploited the vulnerability to deploy a … [Read more...] about PROPHET SPIDER Exploits Citrix ShareFile