CrowdStrike Falcon receives second half-year award for Approved Business Security Product from AV-Comparatives in 2021 This marks the tenth consecutive Approved Business Security Product award from AV-Comparatives since 2016 CrowdStrike Falcon achieves the highest 99.9% protection rate, demonstrating its ability to protect against real-world threats using the power of machine … [Read more...] about CrowdStrike Falcon Receives Second AV-Comparatives Product Award
Falcon
CrowdStrike Falcon and Humio: Leverage All Your FDR Data in One Place
This blog was originally published Nov. 8, 2021 on humio.com. Humio is a CrowdStrike Company. In 2021, Humio and Crowdstrike joined forces to deliver a truly robust security solution. CrowdStrike delivers the industry’s most comprehensive security solution for protecting endpoints and workloads, processing 1 trillion security-related events per day with its pioneering Threat … [Read more...] about CrowdStrike Falcon and Humio: Leverage All Your FDR Data in One Place
How Falcon OverWatch Detected SILENT CHOLLIMA’s Custom Tooling
CrowdStrike Falcon OverWatch™ recently released its annual threat hunting report, detailing the interactive intrusion activity observed by hunters over the course of the past year. The tactics, techniques and procedures (TTPs) an adversary uses serve as key indicators to threat hunters of who might be behind an intrusion. OverWatch threat hunters uncovered an intrusion against … [Read more...] about How Falcon OverWatch Detected SILENT CHOLLIMA’s Custom Tooling
CrowdStrike Falcon Platform Receives 12th AAA Rating from SE Labs
The CrowdStrike Falcon® platform receives new AAA rating from SE Labs, one of the most prestigious independent third-party testing institutions Falcon achieves AAA rating, scoring 99% total accuracy and 100% legitimate accuracy This marks the Falcon platform’s 12th AAA rating from SE Labs since March 2018 CrowdStrike remains committed to transparency and our mission to stop … [Read more...] about CrowdStrike Falcon Platform Receives 12th AAA Rating from SE Labs
Falcon Spotlight ExPRT.AI Helps Federal Agencies Meet CISA Mandate
The Cybersecurity and Infrastructure Security Agency (CISA) issued a mandate on November 2, 2021, for all U.S. federal agencies to fix hundreds of known vulnerabilities. Binding Operational Directive 22-01 (BOD 22-01) compels all federal departments and agencies to specifically address the vulnerabilities in the published catalog to protect and safeguard valuable federal data … [Read more...] about Falcon Spotlight ExPRT.AI Helps Federal Agencies Meet CISA Mandate
How to Use Falcon Spotlight’s ExPRT.AI
Introduction Organizations have historically been reliant on CVSS severity scoring to help prioritize vulnerability remediations. Unfortunately, that single data point is often not enough to drive an effective patching strategy. With limited time and resources, organizations are commonly left with large quantities of unaddressed, severely-ranked vulnerabilities. While the … [Read more...] about How to Use Falcon Spotlight’s ExPRT.AI
Falcon CWP Complete Closing Cloud Security Skills Gap
The need for speed and agility in today’s digital business requires changes to IT infrastructure, most notably the shift to cloud-native architectures and the adoption of DevOps best practices to improve the speed and efficiency with which enterprise applications are brought to market. This shift has led many businesses to move to containers, microservices and Kubernetes (K8s) … [Read more...] about Falcon CWP Complete Closing Cloud Security Skills Gap
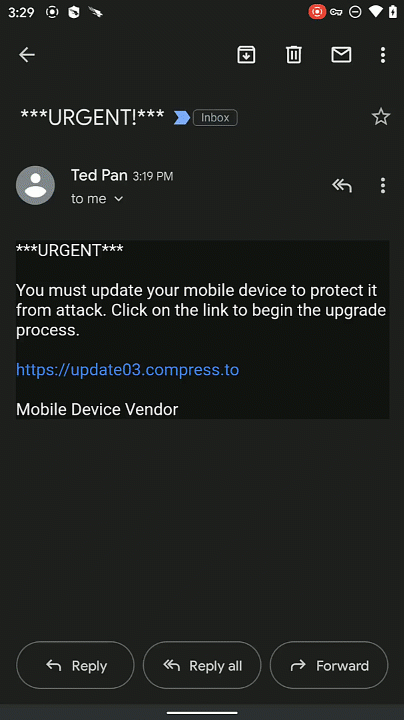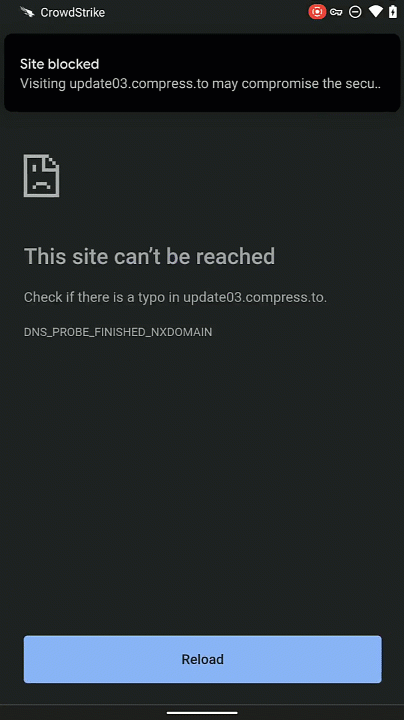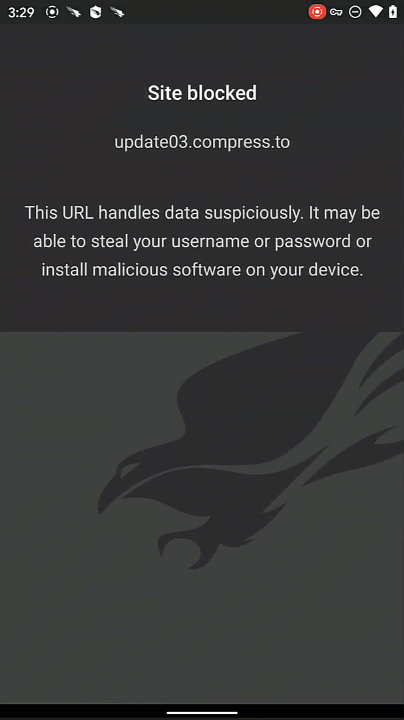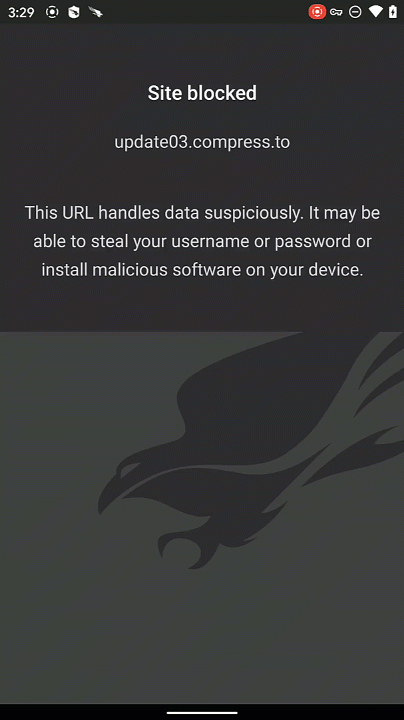
Protecting Users from Malicious Sites with Falcon for Mobile
Introduction Today, mobile devices are ubiquitous within enterprise environments. But with their proliferation, it provides adversaries with yet another attack surface with which they can target users and cause a breach. From phishing attacks to malicious apps, mobile users tend to let their guard down and potentially click on obfuscated links to malicious sites. Falcon for … [Read more...] about Protecting Users from Malicious Sites with Falcon for Mobile
How to Setup the CrowdStrike Falcon SIEM Connector
Introduction The Falcon SIEM Connector provides users a turnkey, SIEM-consumable data stream. The Falcon SIEM Connector: Transforms Crowdstrike API data into a format that a SIEM can consume Maintains the connection to the CrowdStrike Event Streaming API and your SIEM Manages the data-stream pointer to prevent data loss Prerequisites Before using the Falcon SIEM Connector, … [Read more...] about How to Setup the CrowdStrike Falcon SIEM Connector
How to Import IOCs Into the CrowdStrike Falcon Platform
Introduction As part of the CrowdStrike API, the “Custom IOC APIs” allows you to retrieve, upload, update, search, and delete custom Indicators of Compromise (IOCs) that you want CrowdStrike to identify. With the ability to upload IOCs to the endpoints can automatically detect and prevent attacks identified by the indicators provided from a threat feed. Prerequisites To get … [Read more...] about How to Import IOCs Into the CrowdStrike Falcon Platform