Organizations today battle an ever-evolving cyber threat landscape, yet many security teams struggle to keep pace due to a critical skills gap and limited access to high-quality training. As teams are expected to do more with fewer resources, cybersecurity education is essential. At CrowdStrike, we’re committed to breaking down these barriers. That’s why we’ve reimagined … [Read more...] about CrowdStrike University Fast Track Fuels Cybersecurity Training
fast
Get the Info You Need, Fast
TL;DR What’s New? Logz.io customers can now use the AI Agent to run Root Cause Analysis (RCA) on alerts set up in the platform Users can get to the root causes of issues with a trigger process through alerting Why Does It Matter? Through RCA on Alerts, users will get detailed insights and actionable recommendations to dramatically reduce troubleshooting timeframes Get … [Read more...] about Get the Info You Need, Fast
Logz.io Telemetry Collector for Fast Data Shipping
Today we’re excited to announce Logz.io Telemetry Collector – an agent that can send logs, metrics, and traces to Logz.io in a single installation as part of our Open 360™ platform. With Telemetry Collector, customers can get started monitoring their services with Logz.io faster than ever by simplifying the data collection process.Why we built Logz.io’s Telemetry CollectorTo … [Read more...] about Logz.io Telemetry Collector for Fast Data Shipping
Accelerate Troubleshooting, Forensics and Response With Fast and Efficient Search
This blog was originally published Nov. 22, 2021 on humio.com. Humio is a CrowdStrike Company. Whether you’re diagnosing a system outage, mitigating a malicious attack or trying to get to the bottom of an application-response-time issue, speed is critical. Pinpointing and resolving issues quickly and easily can mean the difference between success and crisis for any business, … [Read more...] about Accelerate Troubleshooting, Forensics and Response With Fast and Efficient Search
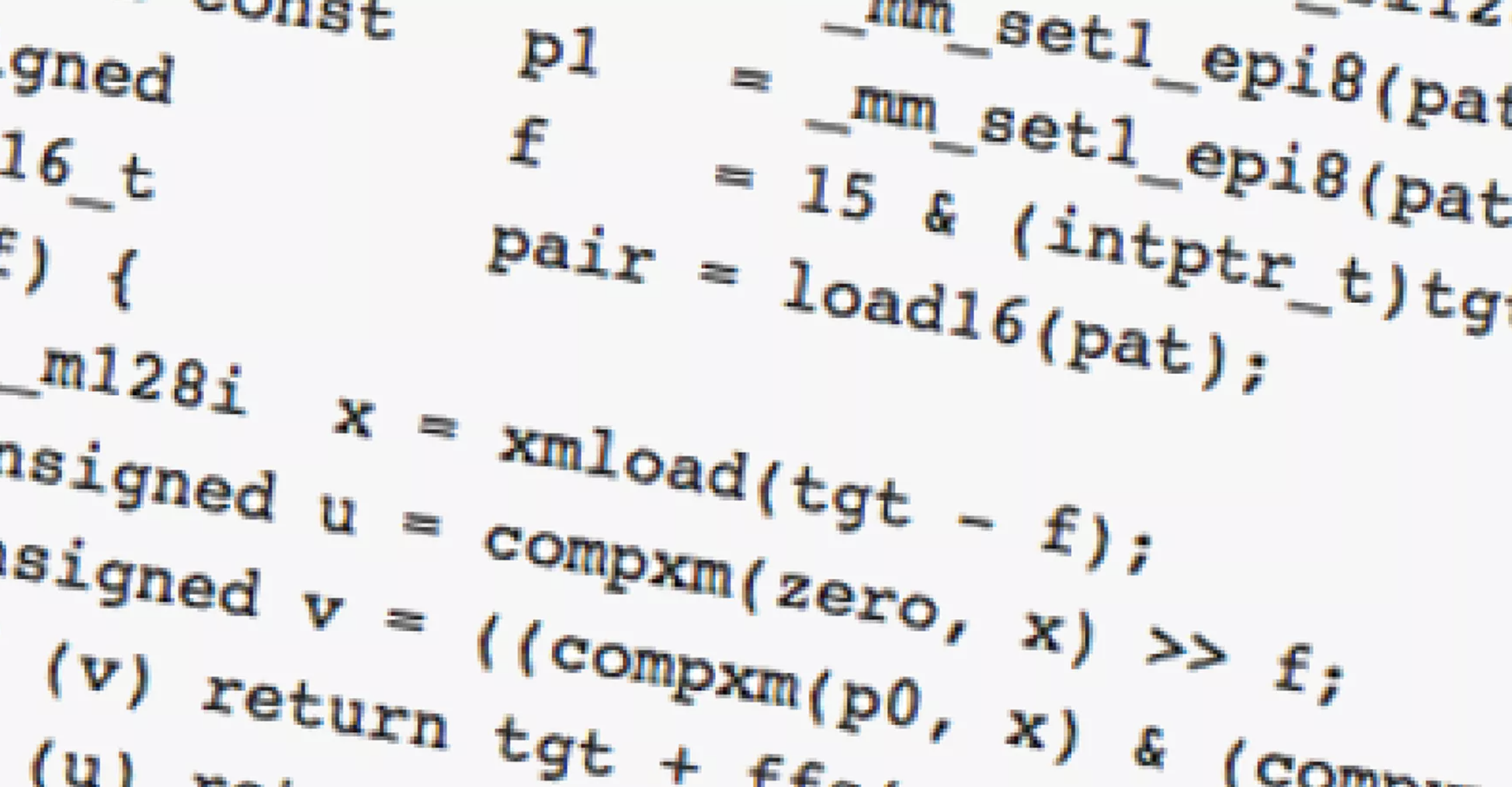
How Fast Can You Grep?
This blog was originally published Sept. 28, 2017 on humio.com. Humio is a CrowdStrike Company. Assume that you have a 1GB text you want to search. A typical SSD lets you read on the order of 1GB/s, which means that you can copy the file contents from disk into memory at that speed. Next, you will then need to scan through that 1GB of memory using some string search … [Read more...] about How Fast Can You Grep?
Threat Intelligence in SecureX: Fast, Free, or Easy (pick any three)
SecureX is Cisco’s free, acronym-defying security platform. (“Is it XDR? Is it SOAR? Does it solve the same problems as a SIEM? As a TIP?” “Yes.”) From the very beginning, one of the pillars of SecureX was the ability to consume and operationalize your local security context alongside global threat intelligence. And to that end, SecureX includes, by default, a few very … [Read more...] about Threat Intelligence in SecureX: Fast, Free, or Easy (pick any three)
The death of the network perimeter and the firewall? Not so fast.
Welcome to The Future of Firewalling, Part 1… For over two decades, the firewall has been the de-facto tool that facilitated secure connectivity between different networks. Firewalls were traditionally designed around the idea that internal traffic and users were inherently trustworthy and external traffic wasn’t. Thus, the firewall was deployed to create a trust boundary – or … [Read more...] about The death of the network perimeter and the firewall? Not so fast.