No one can deny the convenience of cloud file-storage services like Dropbox or OneDrive. The one drawback is that cybercriminals, intelligence agencies, or the hosting provider itself can view your cloud-based files without authorization. But there’s a more secure alternative: encrypted cloud file-storage. Some call it end-to-end encryption (E2EE) — similar to Signal and … [Read more...] about Which encrypted file storage to choose?
File
Cleo File Transfer Vulnerability Under Exploitation – Patch Pending, Mitigation Urged
Dec 10, 2024Ravie LakshmananVulnerability / Threat Analysis Users of Cleo-managed file transfer software are being urged to ensure that their instances are not exposed to the internet following reports of mass exploitation of a vulnerability affecting fully patched systems. Cybersecurity company Huntress said it discovered evidence of threat actors exploiting the issue en … [Read more...] about Cleo File Transfer Vulnerability Under Exploitation – Patch Pending, Mitigation Urged
Generating a browser HAR file for Kibana troubleshooting
Internet website pages load raw backend data (usually via HTML, JSON, and/or XML) through browser network sockets/API and extend this raw data to make it both presentable (usually via CSS) and interactive (commonly through JavaScript). The Kibana website experience follows this model. All major browsers allow users to inspect a web page loading through their developer tools, … [Read more...] about Generating a browser HAR file for Kibana troubleshooting
Channel File 291 Incident RCA is Available
On July 19, 2024, as part of regular operations, CrowdStrike released a content configuration update (via channel files) for the Windows sensor that resulted in a widespread outage. We apologize unreservedly. View the Channel File 291 Incident Executive Summary We acknowledge the incredible round-the-clock efforts of our customers and partners who, working alongside our teams, … [Read more...] about Channel File 291 Incident RCA is Available
Tech Analysis: Channel File May Contain Null Bytes
Key Points CrowdStrike has observed instances internally and in the field in which the content of one or more channel files on disk is all zeroes. This has been observed in the context of a channel file being written to disk shortly before a machine crashes. The file containing zero content observed after a reboot is an artifact of the way in which the Windows operating system … [Read more...] about Tech Analysis: Channel File May Contain Null Bytes
DarkGate Malware Exploits Samba File Shares in Short-Lived Campaign
Jul 12, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have shed light on a short-lived DarkGate malware campaign that leveraged Samba file shares to initiate the infections. Palo Alto Networks Unit 42 said the activity spanned the months of March and April 2024, with the infection chains using servers running public-facing Samba file shares hosting Visual Basic … [Read more...] about DarkGate Malware Exploits Samba File Shares in Short-Lived Campaign
Tracing Linux: A file integrity monitoring use case
In the current landscape of tracing Linux, eBPF emerges as the de-facto solution to implement FIM, facilitating real-time kernel event instrumentation with extensive detail delivered to user space. However, tracing file events with user information on older Linux kernels proves more complex than initially perceived. In such scenarios, eBPF is not always the straightforward … [Read more...] about Tracing Linux: A file integrity monitoring use case
Popular Android Apps Like Xiaomi, WPS Office Vulnerable to File Overwrite Flaw
May 02, 2024NewsroomVulnerability / Android Several popular Android applications available in Google Play Store are susceptible to a path traversal-affiliated vulnerability that could be exploited by a malicious app to overwrite arbitrary files in the vulnerable app's home directory. "The implications of this vulnerability pattern include arbitrary code execution and token … [Read more...] about Popular Android Apps Like Xiaomi, WPS Office Vulnerable to File Overwrite Flaw
A Guide to Log File Parsing Tools
While log parsing isn’t very sexy and never gets much credit, it is fundamental to productive and centralized log analysis. Log parsing extracts information in your logs and organizes them into fields. Without well-structured fields in your logs, searching and visualizing your log data is near impossible.In this article, we’ll review some of the more popular technologies for … [Read more...] about A Guide to Log File Parsing Tools
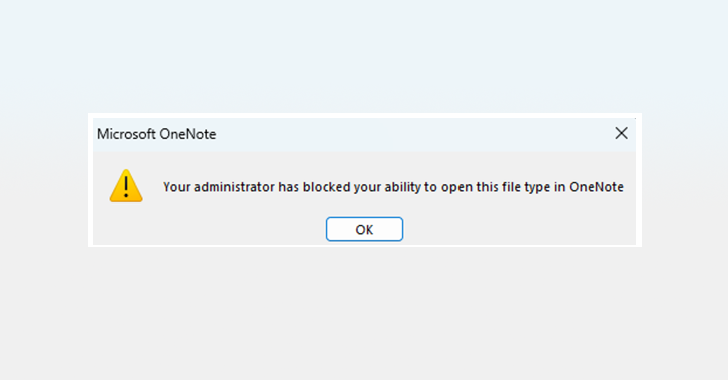
Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
Microsoft has announced plans to automatically block embedded files with "dangerous extensions" in OneNote following reports that the note-taking service is being increasingly abused for malware delivery. Up until now, users were shown a dialog warning them that opening such attachments could harm their computer and data, but it was possible to dismiss the prompt and open the … [Read more...] about Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions