Aug 16, 2024Ravie LakshmananCloud Security / Application Security A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files (.env) that contain credentials associated with cloud and social media applications. "Multiple security missteps were present in the course of this campaign, including the … [Read more...] about Attackers Exploit Public .env Files to Breach Cloud and Social Media Accounts
Files
New Attack Technique Exploits Microsoft Management Console Files
Jun 25, 2024NewsroomVulnerability / Threat Detection Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management Console (MMC) and evade security defenses. Elastic Security Labs has codenamed the approach GrimResource after identifying an artifact … [Read more...] about New Attack Technique Exploits Microsoft Management Console Files
Popular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files
"Test files" associated with the XZ Utils backdoor have made their way to a Rust crate known as liblzma-sys, new findings from Phylum reveal. liblzma-sys, which has been downloaded over 21,000 times to date, provides Rust developers with bindings to the liblzma implementation, an underlying library that is part of the XZ Utils data compression software. The impacted version in … [Read more...] about Popular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files
N. Korea-linked Kimsuky Shifts to Compiled HTML Help Files in Ongoing Cyberattacks
Mar 24, 2024NewsroomArtificial Intelligence / Cyber Espionage The North Korea-linked threat actor known as Kimsuky (aka Black Banshee, Emerald Sleet, or Springtail) has been observed shifting its tactics, leveraging Compiled HTML Help (CHM) files as vectors to deliver malware for harvesting sensitive data. Kimsuky, active since at least 2012, is known to target entities … [Read more...] about N. Korea-linked Kimsuky Shifts to Compiled HTML Help Files in Ongoing Cyberattacks
Secrets, Secrets Are No Fun. Secrets, Secrets (Stored in Plain Text Files) Hurt Someone
Secrets are meant to be hidden or, at the very least, only known to a specific and limited set of individuals (or systems). Otherwise, they aren't really secrets. In personal life, a secret revealed can damage relationships, lead to social stigma, or, at the very least, be embarrassing. In a developer's or application security engineer's professional life, the consequences of … [Read more...] about Secrets, Secrets Are No Fun. Secrets, Secrets (Stored in Plain Text Files) Hurt Someone
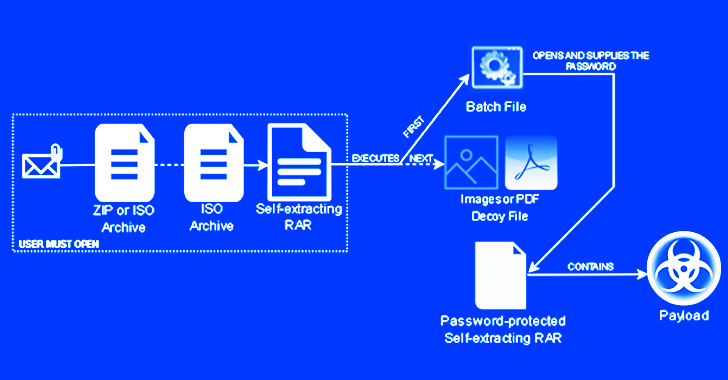
Emotet Botnet Distributing Self-Unlocking Password-Protected RAR Files to Drop Malware
The notorious Emotet botnet has been linked to a new wave of malspam campaigns that take advantage of password-protected archive files to drop CoinMiner and Quasar RAT on compromised systems. In an attack chain detected by Trustwave SpiderLabs researchers, an invoice-themed ZIP file lure was found to contain a nested self-extracting (SFX) archive, the first archive acting as a … [Read more...] about Emotet Botnet Distributing Self-Unlocking Password-Protected RAR Files to Drop Malware
This New Malware Family Using CLFS Log Files to Avoid Detection
Cybersecurity researchers have disclosed details about a new malware family that relies on the Common Log File System (CLFS) to hide a second-stage payload in registry transaction files in an attempt to evade detection mechanisms. FireEye's Mandiant Advanced Practices team, which made the discovery, dubbed the malware PRIVATELOG, and its installer, STASHLOG. Specifics about the … [Read more...] about This New Malware Family Using CLFS Log Files to Avoid Detection
Secret Chat in Telegram Left Self-Destructing Media Files On Devices
Popular messaging app Telegram fixed a privacy-defeating bug in its macOS app that made it possible to access self-destructing audio and video messages long after they disappeared from secret chats. The vulnerability was discovered by security researcher Dhiraj Mishra in version 7.3 of the app, who disclosed his findings to Telegram on December 26, 2020. The issue has since … [Read more...] about Secret Chat in Telegram Left Self-Destructing Media Files On Devices
How to decrypt files encrypted by Fonix
When the Fonix ransomware group suddenly announced the end of its activities and published a master key for decoding encrypted files, our experts immediately updated the Rakhni Decryptor tool to automate the process. You can download the tool right here. The Fonix example illustrates yet again why even if you don’t plan to pay the ransom (a smart choice), you should hold on to … [Read more...] about How to decrypt files encrypted by Fonix
How to recover files encrypted by Yatron and FortuneCrypt
Ransomware has been and remains a big headache for both users and experts alike. It is not a simple task to recover files encrypted by ransomware, and in many cases it’s impossible. But we have good news for the victims of Yatron and FortuneCrypt malware: Kaspersky experts have developed and published decryptors for the files this particular malware encrypts. How to decrypt … [Read more...] about How to recover files encrypted by Yatron and FortuneCrypt