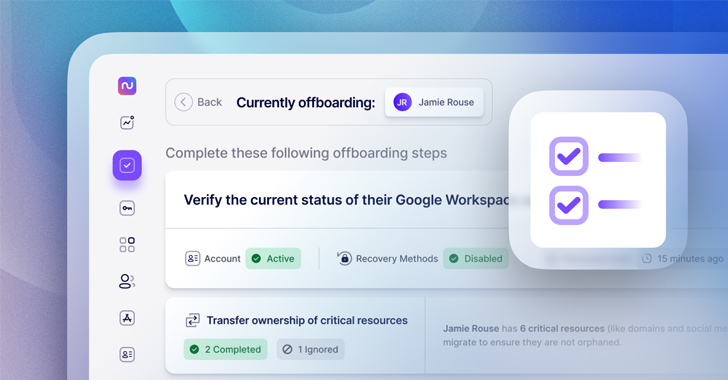
Employee offboarding is no one's favorite task, yet it is a critical IT process that needs to be executed diligently and efficiently. That's easier said than done, especially considering that IT organizations have less visibility and control over employees' IT use than ever. Today, employees can easily adopt new cloud and SaaS applications whenever and wherever they want, and … [Read more...] about Avoid These 5 IT Offboarding Pitfalls
hacker news
Identity Threat Detection & Response (ITDR) – Rips in Your Identity Fabric
Sep 13, 2023The Hacker NewsThreat Detection / SaaS Security In today's digital age, SaaS applications have become the backbone of modern businesses. They streamline operations, enhance productivity, and foster innovation. But with great power comes great responsibility. As organizations integrate more SaaS applications into their workflows, they inadvertently open the door to … [Read more...] about Identity Threat Detection & Response (ITDR) – Rips in Your Identity Fabric
Critical GitHub Vulnerability Exposes 4,000+ Repositories to Repojacking Attack
Sep 12, 2023THNSoftware Security / Vulnerability A new vulnerability disclosed in GitHub could have exposed thousands of repositories at risk of repojacking attacks, new findings show. The flaw "could allow an attacker to exploit a race condition within GitHub's repository creation and username renaming operations," Checkmarx security researcher Elad Rapoport said in a … [Read more...] about Critical GitHub Vulnerability Exposes 4,000+ Repositories to Repojacking Attack
A Guide to Robust Security
With the growing reliance on web applications and digital platforms, the use of application programming interfaces (APIs) has become increasingly popular. If you aren't familiar with the term, APIs allow applications to communicate with each other and they play a vital role in modern software development. However, the rise of API use has also led to an increase in the number of … [Read more...] about A Guide to Robust Security
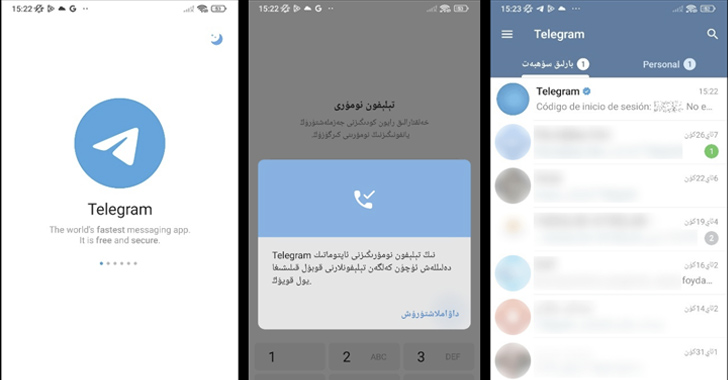
Millions Infected by Spyware Hidden in Fake Telegram Apps on Google Play
Sep 09, 2023THNMobile Security / Spyware Spyware masquerading as modified versions of Telegram have been spotted in the Google Play Store that's designed to harvest sensitive information from compromised Android devices. According to Kaspersky security researcher Igor Golovin, the apps come with nefarious features to capture and exfiltrate names, user IDs, contacts, phone … [Read more...] about Millions Infected by Spyware Hidden in Fake Telegram Apps on Google Play
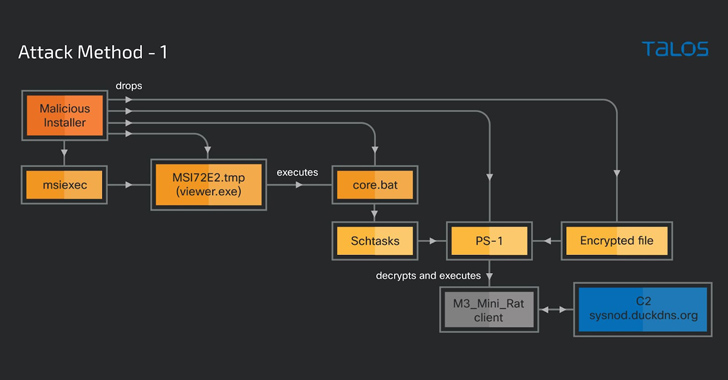
Cybercriminals Weaponizing Legitimate Advanced Installer Tool in Crypto-Mining Attacks
Sep 09, 2023THNMalware / Hacking A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021. "The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and … [Read more...] about Cybercriminals Weaponizing Legitimate Advanced Installer Tool in Crypto-Mining Attacks
Protecting Your Microsoft IIS Servers Against Malware Attacks
Microsoft Internet Information Services (IIS) is a web server software package designed for Windows Server. Organizations commonly use Microsoft IIS servers to host websites, files, and other content on the web. Threat actors increasingly target these Internet-facing resources as low-hanging fruit for finding and exploiting vulnerabilities that facilitate access to IT … [Read more...] about Protecting Your Microsoft IIS Servers Against Malware Attacks
MSP/MSSP Security Strategies for 2024
Sep 07, 2023The Hacker NewsVirtual CISO / Cybersecurity By the end of 2024, the number of MSPs and MSSPs offering vCISO services is expected to grow by almost 5 fold, as can be seen in figure 1. This incredible surge reflects the growing business demand for specialized cybersecurity expertise and the lucrative opportunities for MSPs and MSSPs in vCISO services. Figure 1: … [Read more...] about MSP/MSSP Security Strategies for 2024
Three CISOs Share How to Run an Effective SOC
Sep 06, 2023The Hacker NewsSecurity Operations Center (SOC) The role of the CISO keeps taking center stage as a business enabler: CISOs need to navigate the complex landscape of digital threats while fostering innovation and ensuring business continuity. Three CISOs; Troy Wilkinson, CISO at IPG; Rob Geurtsen, former Deputy CISO at Nike; and Tammy Moskites, Founder of … [Read more...] about Three CISOs Share How to Run an Effective SOC
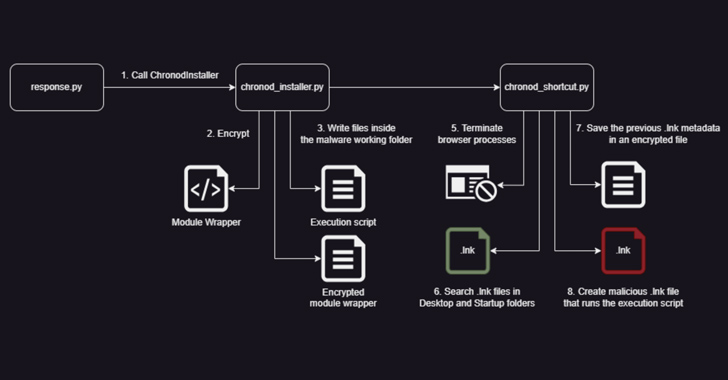
New Python Variant of Chaes Malware Targets Banking and Logistics Industries
Sep 05, 2023THNCyber Threat / Malware Banking and logistics industries are under the onslaught of a reworked variant of a malware called Chaes. "It has undergone major overhauls: from being rewritten entirely in Python, which resulted in lower detection rates by traditional defense systems, to a comprehensive redesign and an enhanced communication protocol," Morphisec said in … [Read more...] about New Python Variant of Chaes Malware Targets Banking and Logistics Industries