As cloud applications are built, tested and updated, they wind their way through an ever-complex series of different tools and teams. Across hundreds or even thousands of technologies that make up the patchwork quilt of development and cloud environments, security processes are all too often applied in only the final phases of software development. Placing security at the very … [Read more...] about The 4 Keys to Building Cloud Security Programs That Can Actually Shift Left
hacker news
How to Detect this Silent Threat
A new study conducted by Uptycs has uncovered a stark increase in the distribution of information stealing (a.k.a. infostealer or stealer) malware. Incidents have more than doubled in Q1 2023, indicating an alarming trend that threatens global organizations. According to the new Uptycs' whitepaper, Stealers are Organization Killers, a variety of new info stealers have emerged … [Read more...] about How to Detect this Silent Threat
Examining the Growing Threat and User Perspectives
Jul 25, 2023The Hacker NewsEndpoint Security / macOS As the number of people using macOS keeps going up, so does the desire of hackers to take advantage of flaws in Apple's operating system. What Are the Rising Threats to macOS? There is a common misconception among macOS fans that Apple devices are immune to hacking and malware infection. However, users have been facing … [Read more...] about Examining the Growing Threat and User Perspectives
New OpenSSH Vulnerability Exposes Linux Systems to Remote Command Injection
Jul 24, 2023THNLinux / Network Security Details have emerged about a now-patched flaw in OpenSSH that could be potentially exploited to run arbitrary commands remotely on compromised hosts under specific conditions. "This vulnerability allows a remote attacker to potentially execute arbitrary commands on vulnerable OpenSSH's forwarded ssh-agent," Saeed Abbasi, manager of … [Read more...] about New OpenSSH Vulnerability Exposes Linux Systems to Remote Command Injection
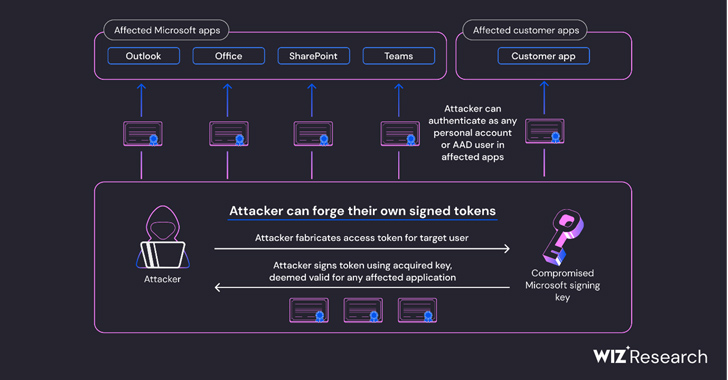
Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports
Jul 21, 2023THNEmail Security / Cyber Attack The recent attack against Microsoft's email infrastructure by a Chinese nation-state actor referred to as Storm-0558 is said to have a broader scope than previously thought. According to cloud security company Wiz, the inactive Microsoft account (MSA) consumer signing key used to forge Azure Active Directory (Azure AD or AAD) … [Read more...] about Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports
DDoS Botnets Hijacking Zyxel Devices to Launch Devastating Attacks
Jul 21, 2023THNVulnerability / Botnet Several distributed denial-of-service (DDoS) botnets have been observed exploiting a critical flaw in Zyxel devices that came to light in April 2023 to gain remote control of vulnerable systems. "Through the capture of exploit traffic, the attacker's IP address was identified, and it was determined that the attacks were occurring in … [Read more...] about DDoS Botnets Hijacking Zyxel Devices to Launch Devastating Attacks
Turla’s New DeliveryCheck Backdoor Breaches Ukrainian Defense Sector
Jul 20, 2023THNCyber Attack / Malware The defense sector in Ukraine and Eastern Europe has been targeted by a novel .NET-based backdoor called DeliveryCheck (aka CAPIBAR or GAMEDAY) that's capable of delivering next-stage payloads. The Microsoft threat intelligence team, in collaboration with the Computer Emergency Response Team of Ukraine (CERT-UA), attributed the attacks to … [Read more...] about Turla’s New DeliveryCheck Backdoor Breaches Ukrainian Defense Sector
How to Manage Your Attack Surface?
Attack surfaces are growing faster than security teams can keep up. To stay ahead, you need to know what's exposed and where attackers are most likely to strike. With cloud migration dramatically increasing the number of internal and external targets, prioritizing threats and managing your attack surface from an attacker's perspective has never been more important. Let's look … [Read more...] about How to Manage Your Attack Surface?
VirusTotal Data Leak Exposes Some Registered Customers’ Details
Jul 18, 2023THNPrivacy / Malware Data associated with a subset of registered customers of VirusTotal, including their names and email addresses, have leaked on the internet. The security incident, which comprises a database of 5,600 names in a 313KB file, was first disclosed by Der Spiegel and Der Standard yesterday. Launched in 2004, VirusTotal is a popular service that … [Read more...] about VirusTotal Data Leak Exposes Some Registered Customers’ Details