If you use VLC media player on your computer and haven't updated it recently, don't you even dare to play any untrusted, randomly downloaded video file on it.Doing so could allow hackers to remotely take full control over your computer system.That's because VLC media player software versions prior to 3.0.7 contain two high-risk security vulnerabilities, besides many other … [Read more...] about Beware! Playing Untrusted Videos On VLC Player Could Hack Your Computer
hacking
MongoDB 4.2 Introduces End-to-End Field Level Encryption for Databases
At its developer conference held earlier this week in New York, the MongoDB team announced the latest version of its database management software that includes a variety of advanced features, including Field Level Encryption, Distributed Transactions, and Wildcard Indexes.The newly introduced Field Level Encryption (FLE), which will be available in the upcoming MongoDB 4.2 … [Read more...] about MongoDB 4.2 Introduces End-to-End Field Level Encryption for Databases
Gain the Trust of Your Business Customers With SOC 2 Compliance
In today's business environment, data is what matters most. It matters to organizations that monetize it into operational insights and optimisations, and it matters the threat actors that relentlessly seek to achieve similar monetisation by compromising it.In the very common scenario in which organisation A provides services to organization B, it’s imperative for the latter to … [Read more...] about Gain the Trust of Your Business Customers With SOC 2 Compliance
Firefox Releases Critical Patch Update to Stop Ongoing Zero-Day Attacks
If you use the Firefox web browser, you need to update it right now.Mozilla earlier today released Firefox 67.0.3 and Firefox ESR 60.7.1 versions to patch a critical zero-day vulnerability in the browsing software that hackers have been found exploiting in the wild.Discovered and reported by Samuel Groß, a cybersecurity researcher at Google Project Zero, the vulnerability could … [Read more...] about Firefox Releases Critical Patch Update to Stop Ongoing Zero-Day Attacks
When Time is of the Essence – Testing Controls Against the Latest Threats Faster
A new threat has hit head the headlines (Robinhood anyone?), and you need to know if you're protected right now. What do you do? Traditionally, you would have to go with one of the options below.Option 1 – Manually check that IoCs have been updated across your security controls. This would require checking that security controls such as your email gateway, web gateway, and … [Read more...] about When Time is of the Essence – Testing Controls Against the Latest Threats Faster
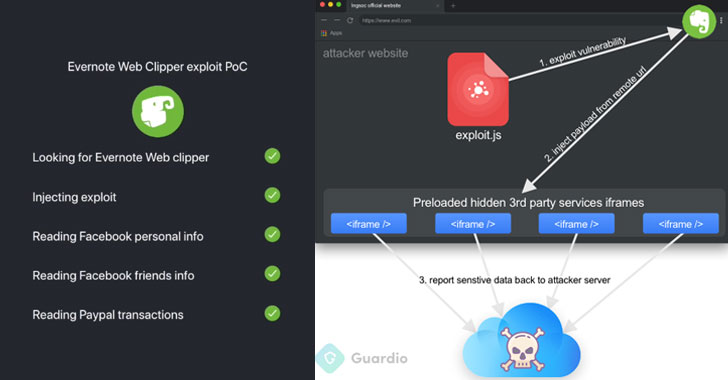
Critical Flaw Reported in Popular Evernote Extension for Chrome Users
Cybersecurity researchers discover a critical flaw in the popular Evernote Chrome extension that could have allowed hackers to hijack your browser and steal sensitive information from any website you accessed.Evernote is a popular service that helps people taking notes and organize their to-do task lists, and over 4,610,000 users have been using its Evernote Web Clipper … [Read more...] about Critical Flaw Reported in Popular Evernote Extension for Chrome Users
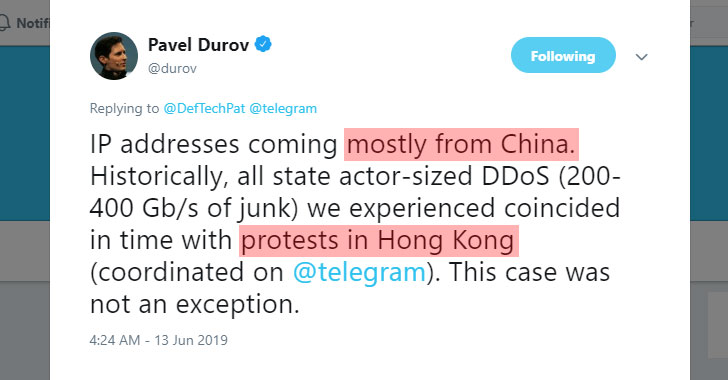
Telegram Suffers ‘Powerful DDoS Attack’ From China During Hong Kong Protests
Telegram, one of the most popular encrypted messaging app, briefly went offline yesterday for hundreds of thousands of users worldwide after a powerful distributed denial-of-service (DDoS) attack hit its servers.Telegram founder Pavel Durov later revealed that the attack was mainly coming from the IP addresses located in China, suggesting the Chinese government could be behind … [Read more...] about Telegram Suffers ‘Powerful DDoS Attack’ From China During Hong Kong Protests
Cynet Free Visibility Experience – Unmatched Insight into IT Assets and Activities
Real-time visibility into IT assets and activities introduces speed and efficiency to many critical productivity and security tasks organizations are struggling with—from conventional asset inventory reporting to proactive elimination of exposed attack surfaces.However, gaining such visibility is often highly resource consuming and entails manual integration of various … [Read more...] about Cynet Free Visibility Experience – Unmatched Insight into IT Assets and Activities
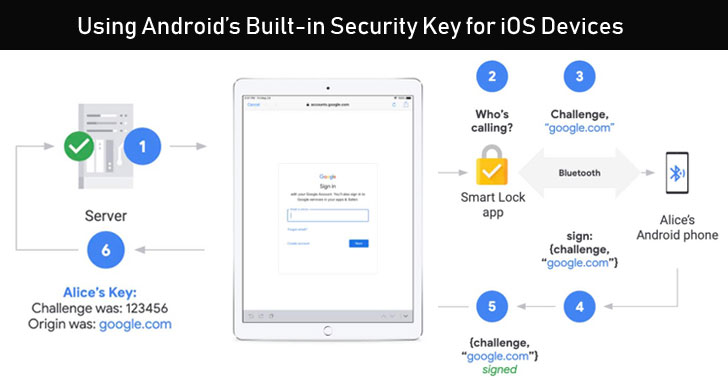
Android’s Built-in Security Key Now Works With iOS Devices For Secure Login
In April this year, a software update from Google overnight turned all Android phones, running Android 7.0 Nougat and up, into a FIDO-certified hardware security key as part of a push to encourage two-step verification.The feature made it possible for users to confirm their identity when logging into a Google account more effortless and secure, without separately managing and … [Read more...] about Android’s Built-in Security Key Now Works With iOS Devices For Secure Login
RAMBleed Attack – Flip Bits to Steal Sensitive Data from Computer Memory
A team of cybersecurity researchers yesterday revealed details of a new side-channel attack on dynamic random-access memory (DRAM) that could allow malicious programs installed on a modern system to read sensitive memory data from other processes running on the same hardware.Dubbed RAMBleed and identified as CVE-2019-0174, the new attack is based on a well-known class of DRAM … [Read more...] about RAMBleed Attack – Flip Bits to Steal Sensitive Data from Computer Memory