Smartphones, tablets, and even cars with Samsung Exynos microprocessors are at risk of remote hacking. Bug hunters at Google Project Zero say you just need the victim’s phone number. This is due to the presence of 18 vulnerabilities in the Exynos baseband radio processor, which is widely used in Google, Vivo, Samsung, and many other smartphones. Four of them are critical and … [Read more...] about Zero-click remote hacks for Samsung, Google, and Vivo smartphones
hacks
Cybercriminals Hold $115,000-Prize Contest to Find New Cryptocurrency Hacks
A top Russian-language underground forum has been running a "contest" for the past month, calling on its community to submit "unorthodox" ways to conduct cryptocurrency attacks. The forum's administrator, in an announcement made on April 20, 2021, invited members to submit papers that assess the possibility of targeting cryptocurrency-related technology, including the theft of … [Read more...] about Cybercriminals Hold $115,000-Prize Contest to Find New Cryptocurrency Hacks
Researchers Demonstrate 2 New Hacks to Modify Certified PDF Documents
Cybersecurity researchers have disclosed two new attack techniques on certified PDF documents that could potentially enable an attacker to alter a document's visible content by displaying malicious content over the certified content without invalidating its signature. "The attack idea exploits the flexibility of PDF certification, which allows signing or adding annotations to … [Read more...] about Researchers Demonstrate 2 New Hacks to Modify Certified PDF Documents
Google Patches Critical Remote Code-Execution Flaws in Android
The Android security update patches 15 bugs, four rated critical, 10 rated high and one ranked moderate in severity. Source link … [Read more...] about Google Patches Critical Remote Code-Execution Flaws in Android
Lax Telco Security Allows Mobile Phone Hijacking and Redirects
A Q&A with Kaspersky Lab researcher David Jacoby examines a gaping hole in the telco customer-service process that allows adversaries to commandeer phone calls. Source link … [Read more...] about Lax Telco Security Allows Mobile Phone Hijacking and Redirects
Google Touts Android Q’s New Security Update Process and Better Privacy Controls for Apps
The administrator of your personal data will be Threatpost, Inc., 500 Unicorn Park, Woburn, MA 01801. Detailed information on the processing of personal data can be found in the privacy policy. In addition, you will find them in the message confirming the subscription to the newsletter. Source link … [Read more...] about Google Touts Android Q’s New Security Update Process and Better Privacy Controls for Apps
Verizon Data Breach Report: Espionage, C-Suite and Cloud Attacks on the Rise
The administrator of your personal data will be Threatpost, Inc., 500 Unicorn Park, Woburn, MA 01801. Detailed information on the processing of personal data can be found in the privacy policy. In addition, you will find them in the message confirming the subscription to the newsletter. Source link … [Read more...] about Verizon Data Breach Report: Espionage, C-Suite and Cloud Attacks on the Rise
Top 5 Configuration Mistakes That Create Field Days for Hackers
Having appropriate security configurations requires your applications, servers and databases to be hardened in accordance with best practices. Source link … [Read more...] about Top 5 Configuration Mistakes That Create Field Days for Hackers
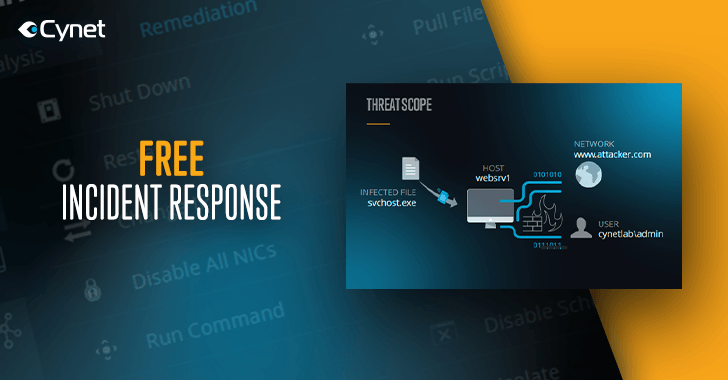
Cynet Provides Security Responders with Free IR Tool to Validate and Respond to Active Threats
Cynet Free IR empowers its users with a solution that is accessible and easy to use, bringing crucial incident response services in-house, while saving them valuable time and resources. Source link … [Read more...] about Cynet Provides Security Responders with Free IR Tool to Validate and Respond to Active Threats
Critical Flaw in Cisco Elastic Services Controller Allows Full System Takeover
Cisco has patched a critical flaw in its virtualized function automation tool, Cisco Elastic Services Controller. Source link … [Read more...] about Critical Flaw in Cisco Elastic Services Controller Allows Full System Takeover