Observability isn’t new. But organizations are struggling to adopt mature observability practices, and the impact on business is palpable.Organizations are seeing the value of observability for their applications and infrastructure—the results of our 2024 Observability Pulse survey of 500 global IT professionals reflects that across the board. But respondents are challenged by … [Read more...] about Does Your Observability Practice Lack Maturity? Here’s What to Do.
Heres
Exposed Secrets are Everywhere. Here’s How to Tackle Them
Picture this: you stumble upon a concealed secret within your company's source code. Instantly, a wave of panic hits as you grasp the possible consequences. This one hidden secret has the power to pave the way for unauthorized entry, data breaches, and a damaged reputation. Understanding the secret is just the beginning; swift and resolute action becomes imperative. However, … [Read more...] about Exposed Secrets are Everywhere. Here’s How to Tackle Them
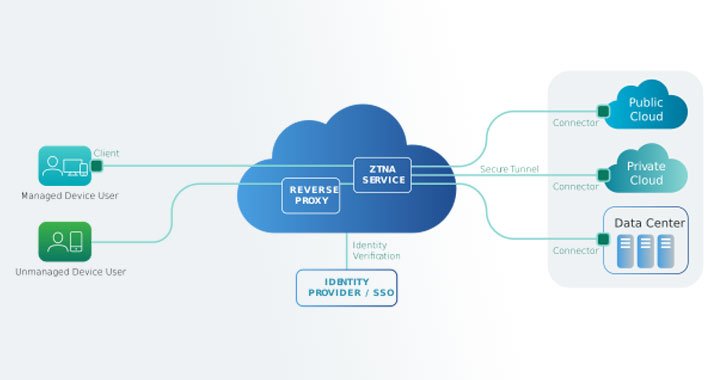
ZTNAs Address Requirements VPNs Cannot. Here’s Why.
I recently hopped on the Lookout podcast to talk about virtual private networks (VPNs) and how they've been extended beyond their original use case of connecting remote laptops to your corporate network. Even in this new world where people are using personal devices and cloud apps, VPN continues to be the go-to solution for remote access and cloud access. After my conversation … [Read more...] about ZTNAs Address Requirements VPNs Cannot. Here’s Why.
Here’s a New Free Tool to Discover Unprotected Cloud Storage Instances
The IDC cloud security survey 2021 states that as many as 98% of companies were victims of a cloud data breach within the past 18 months. Fostered by the pandemic, small and large organizations from all over the world are migrating their data and infrastructure into a public cloud, while often underestimating novel and cloud-specific security or privacy issues. Nearly every … [Read more...] about Here’s a New Free Tool to Discover Unprotected Cloud Storage Instances
Here’s How Iran Spies on Dissidents with the Help of Hackers
Twin cyber operations conducted by state-sponsored Iranian threat actors demonstrate their continued focus on compiling detailed dossiers on Iranian citizens that could threaten the stability of the Islamic Republic, including dissidents, opposition forces, and ISIS supporters, and Kurdish natives. Tracing the extensive espionage operations to two advanced Iranian cyber-groups … [Read more...] about Here’s How Iran Spies on Dissidents with the Help of Hackers
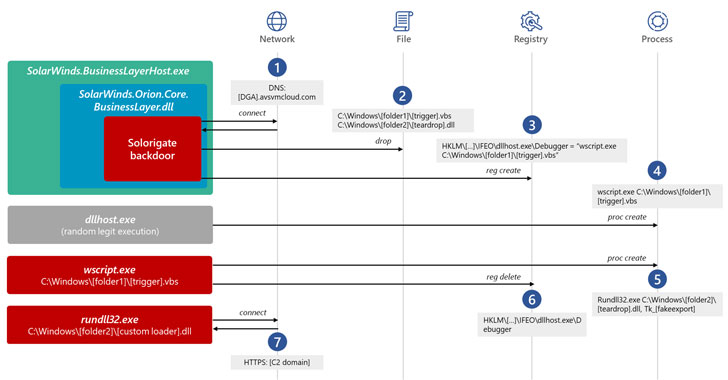
Here’s How SolarWinds Hackers Stayed Undetected for Long Enough
Microsoft on Wednesday shared more specifics about the tactics, techniques, and procedures (TTPs) adopted by the attackers behind the SolarWinds hack to stay under the radar and avoid detection, as cybersecurity companies work towards getting a "clearer picture" of one of the most sophisticated attacks in recent history. Calling the threat actor "skillful and methodic operators … [Read more...] about Here’s How SolarWinds Hackers Stayed Undetected for Long Enough
iPhone stolen? Here’s what not to do
Almost a year ago, we wrote about a classic phishing scheme aimed at unlinking a stolen iPhone from the victim’s Apple ID account. The purpose was to resell the phone not for spare parts, but as a full-fledged second-hand smartphone that’s way more valuable. Last time, fortune favored the scammers, who were able to phish out the iCloud username and password they needed. This … [Read more...] about iPhone stolen? Here’s what not to do