In this blog post, we will discuss our journey to significantly reduce Common Vulnerabilities and Exposures (CVEs) in Elastic container images by switching to a minimal base image in our Elastic products and optimizing our workflows for a scalable vulnerability management program.Elastic Stack based on Chainguard imagesChainguard images are a collection of container images that … [Read more...] about Reducing CVEs in Elastic container images
Images
WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams
Aug 19, 2023THNMalvertising / Website Security Cybersecurity researchers have detailed an updated version of an advanced fingerprinting and redirection toolkit called WoofLocker that's engineered to conduct tech support scams. The sophisticated traffic redirection scheme was first documented by Malwarebytes in January 2020, leveraging JavaScript embedded in compromised … [Read more...] about WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams
Neural networks reveal the images used to train them
Your (neural) networks are leaking Researchers at universities in the U.S. and Switzerland, in collaboration with Google and DeepMind, have published a paper showing how data can leak from image-generation systems that use the machine-learning algorithms DALL-E, Imagen or Stable Diffusion. All of them work the same way on the user side: you type in a specific text query — for … [Read more...] about Neural networks reveal the images used to train them
Apple Delays Plans to Scan Devices for Child Abuse Images After Privacy Backlash
Apple is temporarily hitting the pause button on its controversial plans to screen users' devices for child sexual abuse material (CSAM) after receiving sustained blowback over worries that the tool could be weaponized for mass surveillance and erode the privacy of users. "Based on feedback from customers, advocacy groups, researchers, and others, we have decided to take … [Read more...] about Apple Delays Plans to Scan Devices for Child Abuse Images After Privacy Backlash
Magecart Hackers Hide Stolen Credit Card Data Into Images for Evasive Exfiltration
Cybercrime actors part of the Magecart group have latched on to a new technique of obfuscating the malware code within comment blocks and encoding stolen credit card data into images and other files hosted on the server, once again demonstrating how the attackers are continuously improving their infection chains to escape detection. "One tactic that some Magecart actors employ … [Read more...] about Magecart Hackers Hide Stolen Credit Card Data Into Images for Evasive Exfiltration
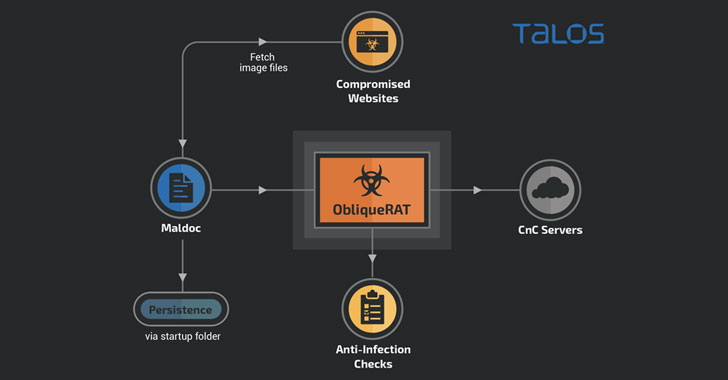
Hackers Now Hiding ObliqueRAT Payload in Images to Evade Detection
Cybercriminals are now deploying remote access Trojans (RATs) under the guise of seemingly innocuous images hosted on infected websites, once again highlighting how threat actors quickly change tactics when their attack methods are discovered and exposed publicly. New research released by Cisco Talos reveals a new malware campaign targeting organizations in South Asia that … [Read more...] about Hackers Now Hiding ObliqueRAT Payload in Images to Evade Detection
Docker Images Containing Cryptojacking Malware Distributed via Docker Hub
With Docker gaining popularity as a service to package and deploy software applications, malicious actors are taking advantage of the opportunity to target exposed API endpoints and craft malware-infested images to facilitate distributed denial-of-service (DDoS) attacks and mine cryptocurrencies.According to a report published by Palo Alto Networks' Unit 42 threat intelligence … [Read more...] about Docker Images Containing Cryptojacking Malware Distributed via Docker Hub
Facebook Patches “Memory Disclosure Using JPEG Images” Flaws in HHVM Servers
Facebook has patched two high-severity vulnerabilities in its server application that could have allowed remote attackers to unauthorisedly obtain sensitive information or cause a denial of service just by uploading a maliciously constructed JPEG image file.The vulnerabilities reside in HHVM (HipHop Virtual Machine)—a high-performance, open source virtual machine developed by … [Read more...] about Facebook Patches “Memory Disclosure Using JPEG Images” Flaws in HHVM Servers