May 03, 2024NewsroomCloud Security / Threat Intelligence Threat actors have been increasingly weaponizing Microsoft Graph API for malicious purposes with the aim of evading detection. This is done to "facilitate communications with command-and-control (C&C) infrastructure hosted on Microsoft cloud services," the Symantec Threat Hunter Team, part of Broadcom, said in a … [Read more...] about Hackers Increasingly Abusing Microsoft Graph API for Stealthy Malware Communications
Increasingly
Adversaries Increasingly Target Cloud Environments
The CrowdStrike eBook, “Protectors of the Cloud: Combating the Rise in Threats to Cloud Environments,” reveals how adversaries target and infiltrate cloud environments and recommends best practices for defense. As organizations move critical applications and data to the cloud, these resources have come under increasing attack. Adversaries view cloud environments as soft targets … [Read more...] about Adversaries Increasingly Target Cloud Environments
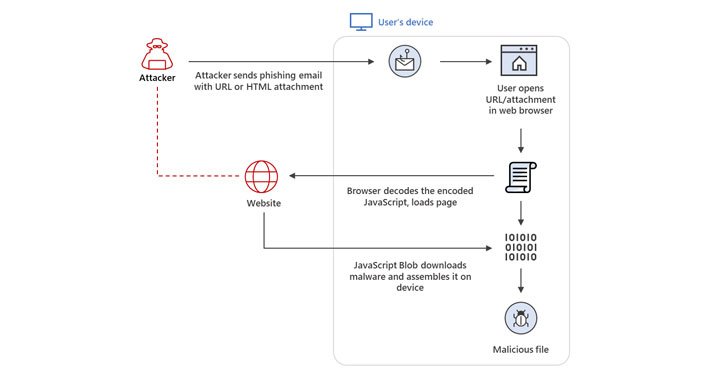
Hackers Increasingly Using HTML Smuggling in Malware and Phishing Attacks
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans (RATs), and ransomware payloads. Microsoft 365 Defender Threat Intelligence Team, in a new report published Thursday, disclosed that it identified infiltrations … [Read more...] about Hackers Increasingly Using HTML Smuggling in Malware and Phishing Attacks
Online Trackers Increasingly Switching to Invasive CNAME Cloaking Technique
With browser makers steadily clamping down on third-party tracking, advertising technology companies are increasingly embracing a DNS technique to evade such defenses, thereby posing a threat to web security and privacy. Called CNAME Cloaking, the practice of blurring the distinction between first-party and third-party cookies not only results in leaking sensitive private … [Read more...] about Online Trackers Increasingly Switching to Invasive CNAME Cloaking Technique