Cost optimization has been one of the hottest topics in observability (and beyond!) lately. Everyone is striving to be efficient, spend money wisely, and get the most out of every dollar invested. At Logz.io, we recently embarked on a very interesting and fruitful data volume optimization journey, reducing our own internal log volume by a whopping 50%. In this article, I’ll … [Read more...] about How Logz.io Reduced Internal Logs Volume by 50% Using Data Optimization Hub
Internal
Reddit Suffers Security Breach Exposing Internal Documents and Source Code
Feb 10, 2023Ravie LakshmananData Breach / Source Code Popular social news aggregation platform Reddit has disclosed that it was the victim of a security incident that enabled unidentified threat actors to gain unauthorized access to internal documents, code, and some unspecified business systems. The company blamed it on a "sophisticated and highly-targeted phishing attack" … [Read more...] about Reddit Suffers Security Breach Exposing Internal Documents and Source Code
T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code
Telecom company T-Mobile on Friday confirmed that it was the victim of a security breach in March after the LAPSUS$ mercenary gang managed to gain access to its networks. The acknowledgment came after investigative journalist Brian Krebs shared internal chats belonging to the core members of the group indicating that LAPSUS$ breached the company several times in March prior to … [Read more...] about T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code
Integrating Perimeter and Internal Defenses: 5 Facts That May or May Not Surprise
This blog has been authored by Frank Dickson, Program Vice President, Cybersecurity Products Practice, and Christopher Rodriguez, Research Director, IDC Network Security IDC recently had the opportunity to talk to CISOs regarding the integration of Cisco Secure Workload and Secure Firewall. As analysts, we can articulate the technical benefits. The realized benefits can be … [Read more...] about Integrating Perimeter and Internal Defenses: 5 Facts That May or May Not Surprise
CD Projekt confirms ransomware attack on internal system
CD Projekt has issued a statement, saying that unspecified ransomware attacked the company’s information systems. The company, known for game series The Witcher and the notorious Cyberpunk 2077 project and behind digital distribution service GOG.com, says that to its knowledge users’ personal data wasn’t affected by the attack. What happened? According to the statement, unknown … [Read more...] about CD Projekt confirms ransomware attack on internal system
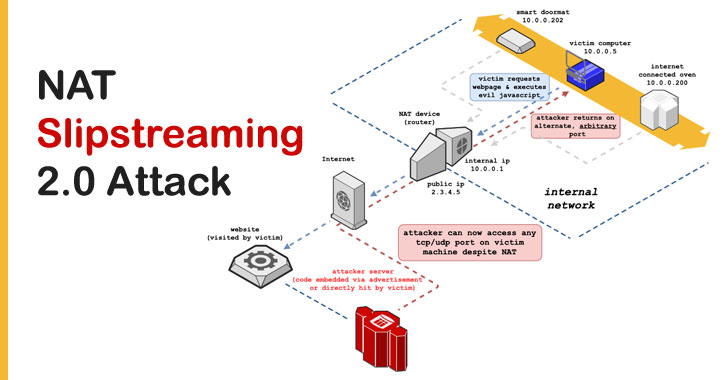
New Attack Could Let Remote Hackers Target Devices On Internal Networks
A newly devised variant of the NAT Slipstreaming attack can be leveraged to compromise and expose any device in an internal network, according to the latest research. Detailed by enterprise IoT security firm Armis, the new attack (CVE-2020-16043 and CVE-2021-23961) builds on the previously disclosed technique to bypass routers and firewalls and reach any unmanaged device within … [Read more...] about New Attack Could Let Remote Hackers Target Devices On Internal Networks
Firefox Blocks Inline and Eval JavaScript on Internal Pages to Prevent Injection Attacks
In an effort to mitigate a large class of potential cross-site scripting issues in Firefox, Mozilla has blocked execution of all inline scripts and potentially dangerous eval-like functions for built-in "about: pages" that are the gateway to sensitive preferences, settings, and statics of the browser.Firefox browser has 45 such internal locally-hosted about pages, some of which … [Read more...] about Firefox Blocks Inline and Eval JavaScript on Internal Pages to Prevent Injection Attacks