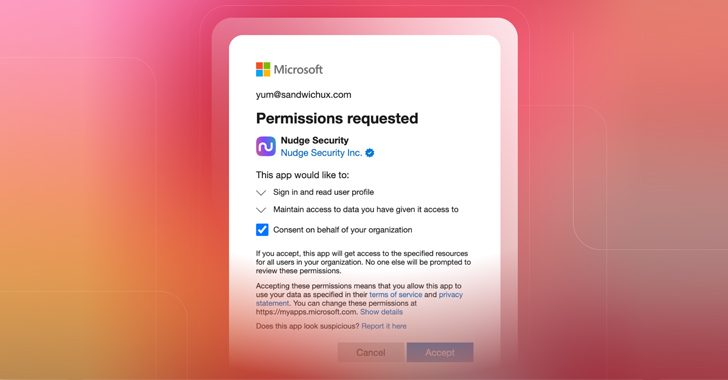
From a user's perspective, OAuth works like magic. In just a few keystrokes, you can whisk through the account creation process and gain immediate access to whatever new app or integration you're seeking. Unfortunately, few users understand the implications of the permissions they allow when they create a new OAuth grant, making it easy for malicious actors to manipulate … [Read more...] about How to Investigate an OAuth Grant for Suspicious Activity or Overly Permissive Scopes
Investigate
Investigate Log4Shell exploits with Elastic Security and Observability
OverviewFollowing the discovery of Log4Shell, a vulnerability in Log4J2, Elastic released a blog post describing how users of our platform can leverage Elastic Security to help defend their networks. We also released an advisory detailing how Elastic products and users are impacted.In this blog, we expand on these initial posts and highlight how the combination of security and … [Read more...] about Investigate Log4Shell exploits with Elastic Security and Observability