Companies are increasingly relying on cloud-based infrastructure, especially as more of their employees are working remotely — and may continue to do so. Public, private and hybrid clouds allow access to data and other assets, no matter where an employee is located — but they also create opportunities for cyberattackers to exploit. In recent months, the CrowdStrike® Services … [Read more...] about CrowdStrike Observes an Increase in IaaS API Key Theft
Key
5 Key Takeaways from 2019 Stealthwatch Customer Research
At Cisco, our customers drive what we do in security. Stealthwatch provides customers around the clock visibility, and a system that keeps up with changes in their IT environments. In a survey that was sent to over 10,000 Stealthwatch customers, we were able to identify what sorts of security challenges are top of mind. Next, we examined how we could address these issues in the … [Read more...] about 5 Key Takeaways from 2019 Stealthwatch Customer Research
Key Trends From the 2019 Global Threat Report
The CrowdStrike® 2019 Global Threat Report: “Adversary Tradecraft and the Importance of Speed,” includes the combined work of CrowdStrike’s skilled and seasoned teams that engage in global intelligence gathering and analyzing, proactive threat hunting, and incident response investigations. The threat report also reveals the trends that these teams have seen in 2018 — trends … [Read more...] about Key Trends From the 2019 Global Threat Report
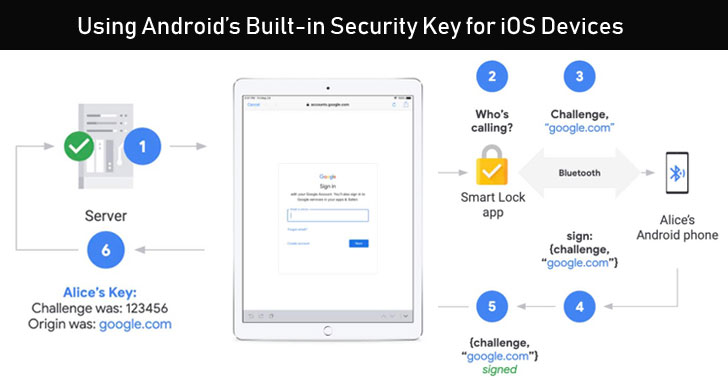
Android’s Built-in Security Key Now Works With iOS Devices For Secure Login
In April this year, a software update from Google overnight turned all Android phones, running Android 7.0 Nougat and up, into a FIDO-certified hardware security key as part of a push to encourage two-step verification.The feature made it possible for users to confirm their identity when logging into a Google account more effortless and secure, without separately managing and … [Read more...] about Android’s Built-in Security Key Now Works With iOS Devices For Secure Login