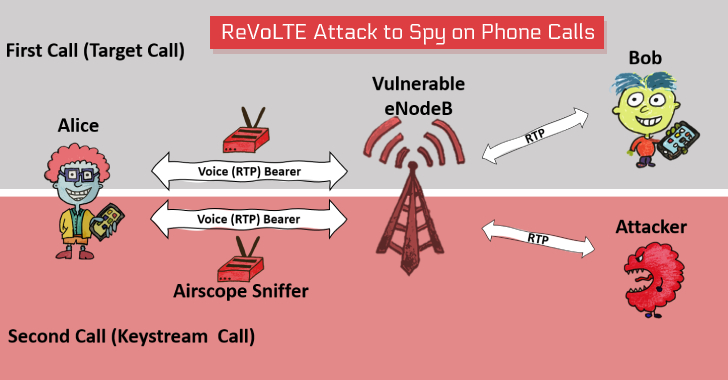
A team of academic researchers—who previously made the headlines earlier this year for uncovering severe security issues in the 4G LTE and 5G networks—today presented a new attack called 'ReVoLTE,' that could let remote attackers break the encryption used by VoLTE voice calls and spy on targeted phone calls.The attack doesn't exploit any flaw in the Voice over LTE (VoLTE) … [Read more...] about New Attack Lets Hackers Decrypt VoLTE Encryption to Spy on Phone Calls
Lets
Amazon’s Ring Video Doorbell Lets Attackers Steal Your Wi-Fi Password
Security researchers at Bitdefender have discovered a high-severity security vulnerability in Amazon's Ring Video Doorbell Pro devices that could allow nearby attackers to steal your WiFi password and launch a variety of cyberattacks using MitM against other devices connected to the same network.In case you don't own one of these, Amazon's Ring Video Doorbell is a smart … [Read more...] about Amazon’s Ring Video Doorbell Lets Attackers Steal Your Wi-Fi Password
New Cache Poisoning Attack Lets Attackers Target CDN Protected Sites
A team of German cybersecurity researchers has discovered a new cache poisoning attack against web caching systems that could be used by an attacker to force a targeted website into delivering error pages to most of its visitors instead of legitimate content or resources.The issue affects reverse proxy cache systems like Varnish and some widely-used Content Distribution … [Read more...] about New Cache Poisoning Attack Lets Attackers Target CDN Protected Sites
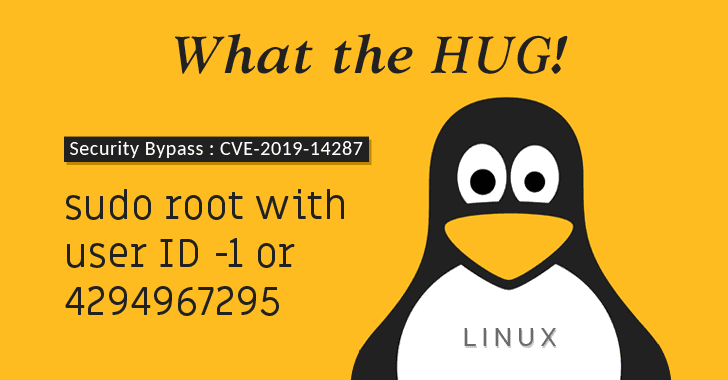
Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted
Attention Linux Users!A new vulnerability has been discovered in Sudo—one of the most important, powerful, and commonly used utilities that comes as a core command installed on almost every UNIX and Linux-based operating system.The vulnerability in question is a sudo security policy bypass issue that could allow a malicious user or a program to execute arbitrary commands as … [Read more...] about Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted
Signal Messenger Bug Lets Callers Auto-Connect Calls Without Receivers’ Interaction
Almost every application contains security vulnerabilities, some of which you may find today, but others would remain invisible until someone else finds and exploits them—which is the harsh reality of cybersecurity and its current state.And when we say this, Signal Private Messenger—promoted as one of the most secure messengers in the world—isn't any exception.Google Project … [Read more...] about Signal Messenger Bug Lets Callers Auto-Connect Calls Without Receivers’ Interaction
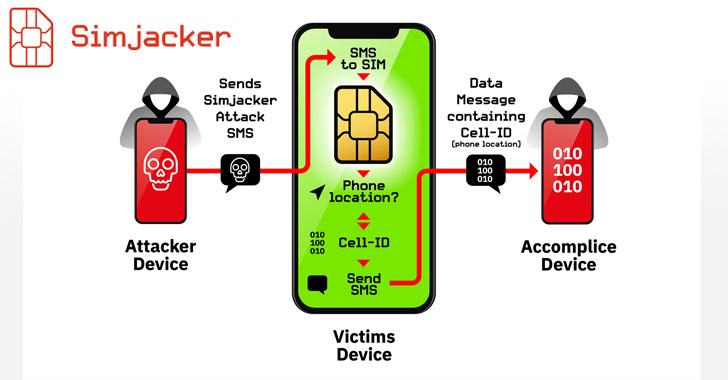
New SIM Card Flaw Lets Hackers Hijack Any Phone Just By Sending SMS
Cybersecurity researchers today revealed the existence of a new and previously undetected critical vulnerability in SIM cards that could allow remote attackers to compromise targeted mobile phones and spy on victims just by sending an SMS.Dubbed "SimJacker," the vulnerability resides in a particular piece of software, called the S@T Browser (a dynamic SIM toolkit), embedded on … [Read more...] about New SIM Card Flaw Lets Hackers Hijack Any Phone Just By Sending SMS
New Bluetooth Vulnerability Lets Attackers Spy On Encrypted Connections
Over a billion Bluetooth-enabled devices, including smartphones, laptops, smart IoT devices, and industrial devices, have been found vulnerable to a high severity vulnerability that could allow attackers to spy on data transmitted between the two devices.The vulnerability, assigned as CVE-2019-9506, resides in the way 'encryption key negotiation protocol' lets two Bluetooth … [Read more...] about New Bluetooth Vulnerability Lets Attackers Spy On Encrypted Connections
Let’s Destroy Democracy – Cisco Blog
Threat Research Election security through an adversary’s eyes This post was authored by Matt Olney. Over the past few years, Cisco Talos has increasingly been involved in election security research and support, most recently supporting the Security Service of Ukraine in their efforts to secure the two Ukrainian presidential elections in … [Read more...] about Let’s Destroy Democracy – Cisco Blog
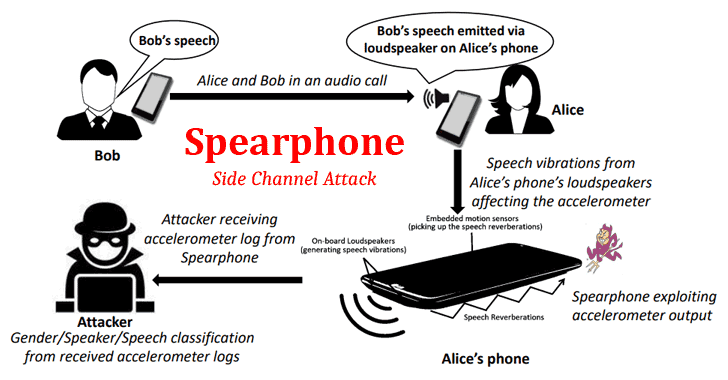
New Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission
Earlier this month, The Hacker News covered a story on research revealing how over 1300 Android apps are collecting sensitive data even when users have explicitly denied the required permissions.The research was primarily focused on how app developers abuse multiple ways around to collect location data, phone identifiers, and MAC addresses of their users by exploiting both … [Read more...] about New Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission