Detecting MFA Fatigue The following rule looks for instances where multiple MFA push notifications are sent to a given user and identifies scenarios where multiple failed push notifications are sent and a successful push notification followed. Note that when a push notification is sent, it’s also transmitted to each registered device, which may result in a slightly skewed … [Read more...] about Leveraging CrowdStrike Falcon Next-Gen SIEM Against Attacks Targeting Okta
Leveraging
Leveraging Threat Intelligence in Cisco Secure Network Analytics
Cisco Secure Network Analytics provides pervasive network visibility and security analytics for advanced protection across the extended network and cloud. The purpose of this blog is to review two methods of using threat intelligence in Secure Network Analytics. First, we will cover the threat intelligence feed, and then we will look at using your own internal threat … [Read more...] about Leveraging Threat Intelligence in Cisco Secure Network Analytics
Maximize IT efficiency leveraging alert management with Elastic AI Assistant for Observability
To tackle the complexities of event management, it's crucial to understand how data evolves throughout the process and its role in managing and correlating events.To begin, we collect data from a multitude of sources, a task Elastic is adept at handling with its robust capabilities for integrating new data streams. Ideally, there should be some commonalities between these data … [Read more...] about Maximize IT efficiency leveraging alert management with Elastic AI Assistant for Observability
Ukrainian Military Targeted in Phishing Campaign Leveraging Drone Manuals
Sep 25, 2023THNCyber Attack / Phishing Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as lures to deliver a Go-based open-source post-exploitation toolkit called Merlin. "Since drones or Unmanned Aerial Vehicles (UAVs) have been an integral tool used by the Ukrainian military, malware-laced lure files themed as UAVs service … [Read more...] about Ukrainian Military Targeted in Phishing Campaign Leveraging Drone Manuals
AVRecon Botnet Leveraging Compromised Routers to Fuel Illegal Proxy Service
Jul 31, 2023THNNetwork Security / Botnet More details have emerged about a botnet called AVRecon, which has been observed making use of compromised small office/home office (SOHO) routers as part of a multi-year campaign active since at least May 2021. AVRecon was first disclosed by Lumen Black Lotus Labs earlier this month as malware capable of executing additional commands … [Read more...] about AVRecon Botnet Leveraging Compromised Routers to Fuel Illegal Proxy Service
Leveraging Elastic Security for comprehensive cloud protection
This comprehensive suite of capabilities, coupled with Elastic Security's power to customize and integrate, solidifies its position as a critical tool in your cloud security arsenal. With such a dynamic platform, your cloud security strategy is not only about defense but also about leveraging intelligence and adaptability to stay one step ahead.ConclusionNavigating the world of … [Read more...] about Leveraging Elastic Security for comprehensive cloud protection
Microsoft Warns of Uptick in Hackers Leveraging Publicly-Disclosed 0-Day Vulnerabilities
Microsoft is warning of an uptick in the nation-state and criminal actors increasingly leveraging publicly-disclosed zero-day vulnerabilities for breaching target environments. The tech giant, in its 114-page Digital Defense Report, said it has "observed a reduction in the time between the announcement of a vulnerability and the commoditization of that vulnerability," making it … [Read more...] about Microsoft Warns of Uptick in Hackers Leveraging Publicly-Disclosed 0-Day Vulnerabilities
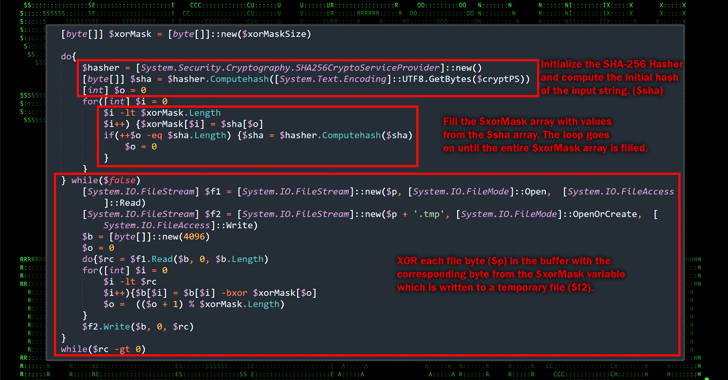
Iranian Hackers Leveraging BitLocker and DiskCryptor in Ransomware Attacks
A ransomware group with an Iranian operational connection has been linked to a string of file-encrypting malware attacks targeting organizations in Israel, the U.S., Europe, and Australia. Cybersecurity firm Secureworks attributed the intrusions to a threat actor it tracks under the moniker Cobalt Mirage, which it said is linked to an Iranian hacking crew dubbed Cobalt Illusion … [Read more...] about Iranian Hackers Leveraging BitLocker and DiskCryptor in Ransomware Attacks