These logs provide deep visibility into the resource and service layers of cloud environments, enabling security teams to monitor for suspicious behavior, identify vulnerabilities and detect unauthorized actions. In the event of a breach, cloud logs are essential for incident response. They serve as the digital evidence needed to understand how an attack unfolded, which … [Read more...] about Cloud Data Logs: Heroes of Detection and Response
logs
Optimize the cost of logs storage in Elastic Cloud using hot and frozen data tiers
Collecting data is crucial for observability and security, and ensuring it is quickly searchable with low-latency results is essential for managing and protecting applications and infrastructure effectively. However, storing all of this data incurs ongoing storage costs, creating a key opportunity for cost savings. In Elastic Cloud, you can optimize storage expenses by setting … [Read more...] about Optimize the cost of logs storage in Elastic Cloud using hot and frozen data tiers
Beyond Logs, Metrics and Traces
Despite what you may have seen and heard, the intersection of logging, metrics and tracing does not tell the whole story about observability.Our systems emit telemetry, and those previously noted telemetry signals are considered the “three pillars” of observability. They’re all important, but by themselves, they aren’t observability.Many users I see day in and day out find … [Read more...] about Beyond Logs, Metrics and Traces
Why do customers choose Elastic for logs?
Elastic strongly believes that the future of observability is one in which logging, APM, infrastructure monitoring, security, and profiling are fully integrated, providing a holistic view through a single unified interface. Doing so puts all your observability data in one place, free of friction. This in turn encourages your SREs to look at problems from multiple angles, … [Read more...] about Why do customers choose Elastic for logs?
Getting Value from Your Proxy Logs with Falcon LogScale
All web traffic flowing out of your company network should be passing through a web proxy. These proxy logs are a great resource for threat hunting and security investigations, yet they often translate into extremely large volumes of data.In a previous blog post, we shared the value of proxy logs in addressing a range of use cases, including hunting for threats, investigating … [Read more...] about Getting Value from Your Proxy Logs with Falcon LogScale
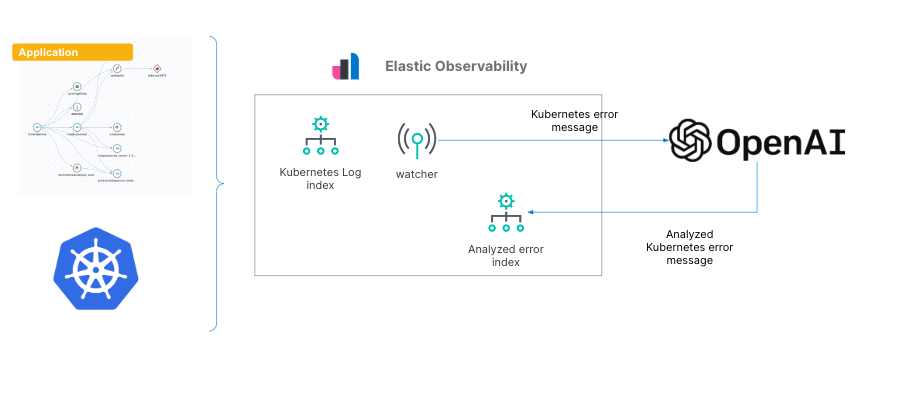
Gain insights into Kubernetes errors with Elastic Observability logs and OpenAI
As we’ve shown in previous blogs, Elastic® provides a way to ingest and manage telemetry from the Kubernetes cluster and the application running on it. Elastic provides out-of-the-box dashboards to help with tracking metrics, log management and analytics, APM functionality (which also supports native OpenTelemetry), and the ability to analyze everything with AIOps features and … [Read more...] about Gain insights into Kubernetes errors with Elastic Observability logs and OpenAI
How Logz.io Reduced Internal Logs Volume by 50% Using Data Optimization Hub
Cost optimization has been one of the hottest topics in observability (and beyond!) lately. Everyone is striving to be efficient, spend money wisely, and get the most out of every dollar invested. At Logz.io, we recently embarked on a very interesting and fruitful data volume optimization journey, reducing our own internal log volume by a whopping 50%. In this article, I’ll … [Read more...] about How Logz.io Reduced Internal Logs Volume by 50% Using Data Optimization Hub
Why metrics, logs, and traces aren’t enough
Identifying performance bottlenecks and wasteful computations can be a complex and challenging task, particularly in modern cloud-native environments. As the complexity of cloud-native environments increases, so does the need for effective observability solutions. Organizations typically rely on the established three pillars of observability –– metrics, logs, and traces –– to … [Read more...] about Why metrics, logs, and traces aren’t enough
This New Fileless Malware Hides Shellcode in Windows Event Logs
A new malicious campaign has been spotted taking advantage of Windows event logs to stash chunks of shellcode for the first time in the wild. "It allows the 'fileless' last stage trojan to be hidden from plain sight in the file system," Kaspersky researcher Denis Legezo said in a technical write-up published this week. The stealthy infection process, not attributed to a known … [Read more...] about This New Fileless Malware Hides Shellcode in Windows Event Logs
Why Actionable Logs Require Sufficient History
This blog was originally published Oct. 26, 2021 on humio.com. Humio is a CrowdStrike Company. Improve visibility and increase insights by logging everything ITOps, DevOps and SecOps teams need historical log data to ensure the security, performance and availability of IT systems and applications. Detailed historical log data is fundamental for understanding system behavior, … [Read more...] about Why Actionable Logs Require Sufficient History