Cybersecurity researchers have uncovered 29 packages in Python Package Index (PyPI), the official third-party software repository for the Python programming language, that aim to infect developers' machines with a malware called W4SP Stealer. "The main attack seems to have started around October 12, 2022, slowly picking up steam to a concentrated effort around October 22," … [Read more...] about Researchers Uncover 29 Malicious PyPI Packages Targeted Developers with W4SP Stealer
Malicious
Researchers Detail Malicious Tools Used by Cyberespionage Group Earth Aughisky
A new piece of research has detailed the increasingly sophisticated nature of the malware toolset employed by an advanced persistent threat (APT) group named Earth Aughisky. "Over the last decade, the group has continued to make adjustments in the tools and malware deployments on specific targets located in Taiwan and, more recently, Japan," Trend Micro disclosed in a technical … [Read more...] about Researchers Detail Malicious Tools Used by Cyberespionage Group Earth Aughisky
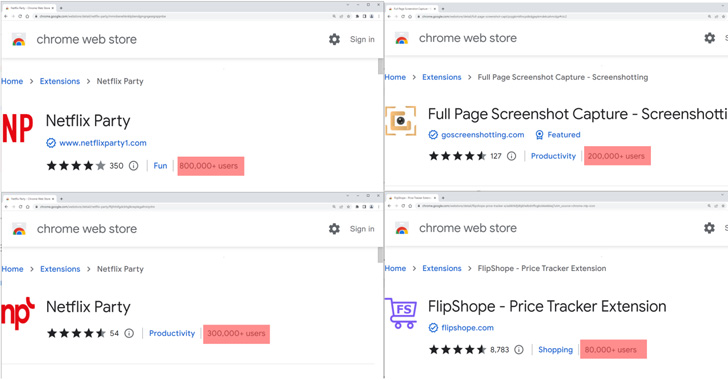
Experts Find Malicious Cookie Stuffing Chrome Extensions Used by 1.4 Million Users
Five imposter extensions for the Google Chrome web browser masquerading as Netflix viewers and others have been found to track users' browsing activity and profit of retail affiliate programs. "The extensions offer various functions such as enabling users to watch Netflix shows together, website coupons, and taking screenshots of a website," McAfee researchers Oliver Devane and … [Read more...] about Experts Find Malicious Cookie Stuffing Chrome Extensions Used by 1.4 Million Users
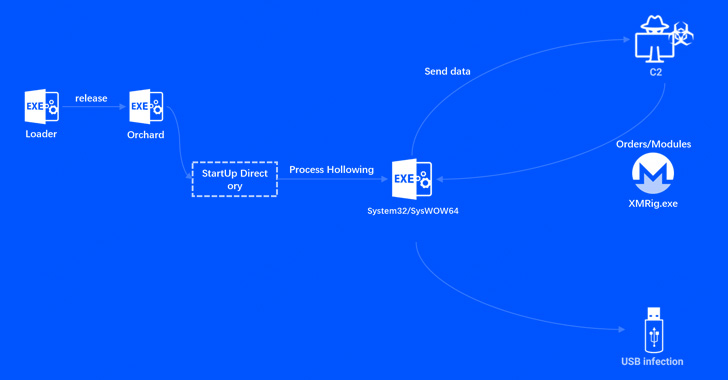
New Orchard Botnet Uses Bitcoin Founder’s Account Info to Generate Malicious Domains
A new botnet named Orchard has been observed using Bitcoin creator Satoshi Nakamoto's account transaction information to generate domain names to conceal its command-and-control (C2) infrastructure. "Because of the uncertainty of Bitcoin transactions, this technique is more unpredictable than using the common time-generated [domain generation algorithms], and thus more … [Read more...] about New Orchard Botnet Uses Bitcoin Founder’s Account Info to Generate Malicious Domains
LofyLife: malicious packages in npm repository
Open-source code is a blessing for the IT industry — it helps programmers save time and build products faster and more efficiently by eliminating the need of writing repetitive common code. To facilitate this knowledge sharing, there are repositories — open platforms where any developer can publish their own packages with their code to speed up the development process for other … [Read more...] about LofyLife: malicious packages in npm repository
Researchers Uncover Malicious NPM Packages Stealing Data from Apps and Web Forms
A widespread software supply chain attack has targeted the NPM package manager at least since December 2021 with rogue modules designed to steal data entered in forms by users on websites that include them. The coordinated attack, dubbed IconBurst by ReversingLabs, involves no fewer than two dozen NPM packages that include obfuscated JavaScript, which comes with malicious code … [Read more...] about Researchers Uncover Malicious NPM Packages Stealing Data from Apps and Web Forms
Google Blocks Dozens of Malicious Domains Operated by Hack-for-Hire Groups
Google's Threat Analysis Group (TAG) on Thursday disclosed it had acted to block as many as 36 malicious domains operated by hack-for-hire groups from India, Russia, and the U.A.E. In a manner analogous to the surveillanceware ecosystem, hack-for-hire firms equip their clients with capabilities to enable targeted attacks aimed at corporates as well as activists, journalists, … [Read more...] about Google Blocks Dozens of Malicious Domains Operated by Hack-for-Hire Groups
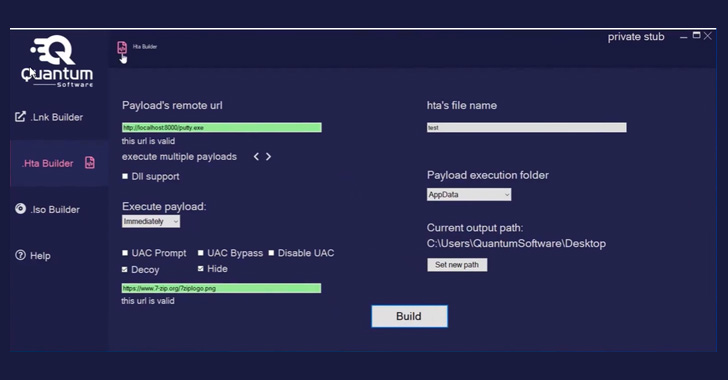
New ‘Quantum’ Builder Lets Attackers Easily Create Malicious Windows Shortcuts
A new malware tool that enables cybercriminal actors to build malicious Windows shortcut (.LNK) files has been spotted for sale on cybercrime forums. Dubbed Quantum Lnk Builder, the software makes it possible to spoof any extension and choose from over 300 icons, not to mention support UAC and Windows SmartScreen bypass as well as "multiple payloads per .LNK" file. Also offered … [Read more...] about New ‘Quantum’ Builder Lets Attackers Easily Create Malicious Windows Shortcuts
Technical Analysis of the WhisperGate Malicious Bootloader
On Jan. 15, 2022, a set of malware dubbed WhisperGate was reported to have been deployed against Ukrainian targets. The incident is widely reported to contain three individual components deployed by the same adversary, including a malicious bootloader that corrupts detected local disks, a Discord-based downloader and a file wiper. The activity occurred at approximately the same … [Read more...] about Technical Analysis of the WhisperGate Malicious Bootloader
Malicious KMSPico Windows Activator Stealing Users’ Cryptocurrency Wallets
Users looking to activate Windows without using a digital license or a product key are being targeted by tainted installers to deploy malware designed to plunder credentials and other information in cryptocurrency wallets. The malware, dubbed "CryptBot," is an information stealer capable of obtaining credentials for browsers, cryptocurrency wallets, browser cookies, credit … [Read more...] about Malicious KMSPico Windows Activator Stealing Users’ Cryptocurrency Wallets